T9000
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 80 % (High) |
| Infected Computers: | 2 |
| First Seen: | February 10, 2016 |
| OS(es) Affected: | Windows |
T9000 is a threatening Trojan infection that may be used to collect files and monitor Skype calls. T9000 is also designed to prevent detection from anti-malware software, making it difficult for computer users to recover from T9000 attacks. T9000 surveil the victim's computer and may be used to collect data or track the victim's activities. T9000 includes sophisticated self-protection techniques that allow T9000 to avoid detection by anti-malware software. T9000 is being used to target Skype users especially and is associated with a backdoor component that allows con artists to gain access to the infected computer.
Table of Contents
T9000 was Able to Hide its Activities for a Long Time
One particularly worrying aspect of T9000 is that many of the top anti-virus programs on the market failed to detect a T9000 infection on a computer. T9000 is designed to collect data from the victim's computer automatically, searching for certain files especially. T9000 also may search for files on removable memory devices. However, T9000 has gained fame because of the way T9000 targets Skype users, allowing third parties keep a watch on Skype conversations.
How T9000 Carries out Its Attack
T9000 is being distributed using a threatening RTF file typically delivered as an email file attachment. The T9000 installation process has several steps that allow con artists to both prevent malware researchers from studying their threats in full while at the same time allow them to check for anti-malware components and bypass different threat protections. Once T9000 has made sure that no anti-malware software can detect it, T9000 is installed and starts collecting information from the victim's computer, sending it to its Command and Control server through the installed backdoor. One way in which computer users can tell if T9000 has infected their computers is if they receive a message that reads 'explorer.exe wants to use Skype' when they start up Skype. This indicates that T9000 has been installed and is now accessing their Skype connection.
Dealing with T9000 and Protecting Computers from this Threat
PC security researchers strongly recommend computer users to update their security software to ensure that it is capable of detecting and removing T9000. The original intent of T9000 may have been to carry out industrial espionage and collect important data such as intellectual property, corporate secrets or sensitive military data. However, T9000 may be adapted to attack virtually any target. T9000 is an updated version of T5000, and older version of this threat that was used in 2013 to carry out attacks against companies in the automotive sector. Previous sightings of older versions of T9000 also include threat attacks carried out in 2014, which lured computer users into opening a corrupted file by claiming that it contained information about the disappeared Malaysian Airlines flight that was trending in the news during that time.
To prevent T9000 attacks, PC security researchers strongly recommend taking the following steps:
- Computer users should ensure that their computers are protected with a reliable, fully updated anti-malware application. Apart from anti-malware software, computer users also should ensure that their computers have a reliable firewall and anti-spam filter for their email. These measures can prevent threats from entering in the first place.
- All software should be kept up-to-date. Computer users should ensure that all security patches are applied, since a threat may be installed by taking advantage of vulnerabilities present in software used commonly.
- Computer users should never open unsolicited email attachments and learn to spot common tactics and spam emails used to deliver corrupted email attachments. This applies to any format of attached file, since files like RTF, DOC, and PDF (which are not commonly associated with threats) also may be exploited to deliver threatening components like T9000 – which is delivered using a threatening RTF file.
- Computer users should avoid websites that may be considered to be associated with threats and other unwanted components.
SpyHunter Detects & Remove T9000
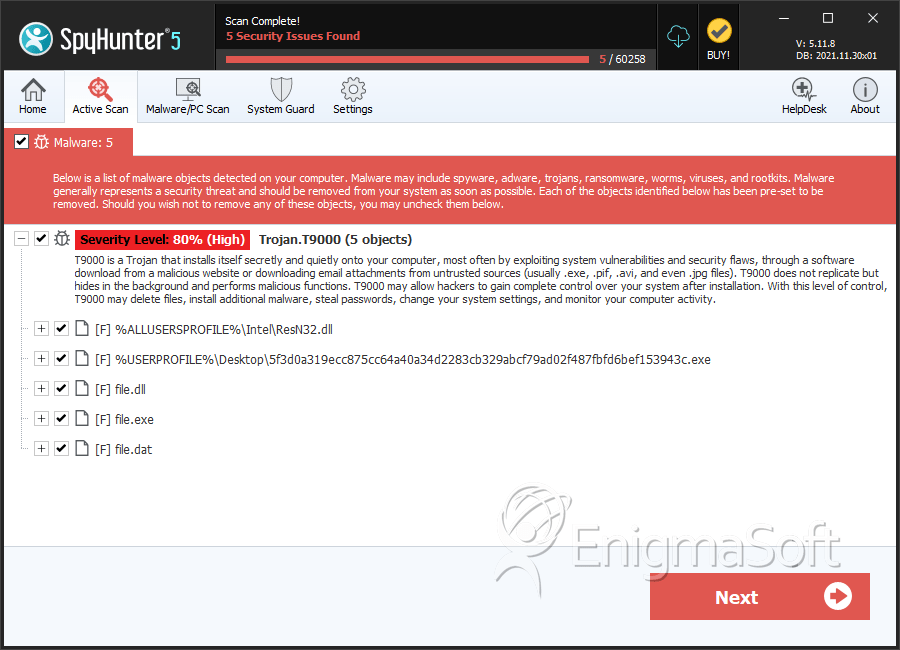
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | ResN32.dll | a45e5c32fc2bc7be9d6e4bba8b2807bf | 1 |
| 2. | 5f3d0a319ecc875cc64a40a34d2283cb329abcf79ad02f487fbfd6bef153943c.exe | e4e8493898d94f737ff4dc8fab743a4a | 1 |
| 3. | file.dll | 1d335f6a58cb9fab503a9b9cb371f57b | 0 |
| 4. | file.dll | 2299fb8268f47294eb2b18282540a955 | 0 |
| 5. | file.exe | d3601a5160b8d122261989d147221eb7 | 0 |
| 6. | file.exe | a9de62186cb8d0e23b0dc75e1ae373ac | 0 |
| 7. | file.exe | b9c584c7c34d14599de8cd3b72f2074b | 0 |
| 8. | file.dat | 29ec20f5fa1817dc9250c434e61420ea | 0 |
| 9. | file.dat | 35f4ce864c3a3dc016fea3459d6402a9 | 0 |
| 10. | file.exe | d8d70851641efbdfce8d561e6b1a2f29 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.