System Antivirus Microsoft 2011
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 80 % (High) |
| Infected Computers: | 20 |
| First Seen: | August 31, 2011 |
| Last Seen: | October 27, 2020 |
| OS(es) Affected: | Windows |
System Antivirus Microsoft 2011 is a malicious Russian ransomware that attacks mainly Russian PC users; however, other Internet may also get infected by it if they're looking for some Russian porn on the web. System Antivirus Microsoft 2011 is able to block infected PC users from accessing their files and software programs until they pay a fee via the SMS text message ($17). The main key is to require unlock the corrupted PC and regain access. System Antivirus Microsoft 2011 declares that your machine was blocked because you were downloading/watching illegitimate videos. System Antivirus Microsoft 2011 also states that if you don't pay the ransom, you system files will be deleted. System Antivirus Microsoft 2011 is delivered via fraudulent porn websites. If your PC has been corrupted by System Antivirus Microsoft 2011, you can either enter a valid serial number or uninstall it manually. However, a valid serial number might not always work because attackers change it very often; besides, the phone numbers will work only in Russia. ESG's security analysts highly recommend you to remove System Antivirus Microsoft 2011 as soon as possible to avoid PC damage and financial losses.
Table of Contents
SpyHunter Detects & Remove System Antivirus Microsoft 2011
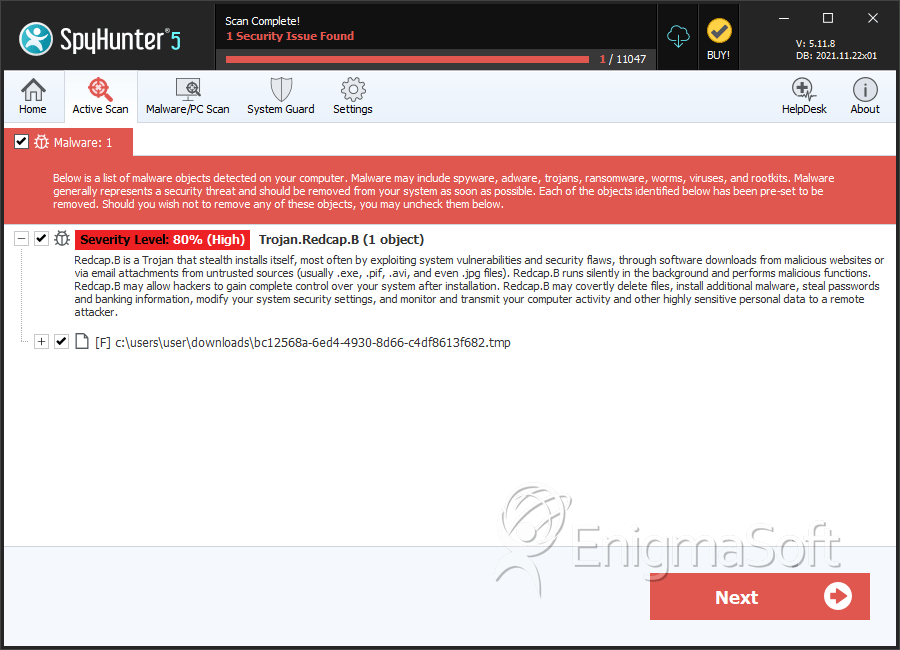
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | bc12568a-6ed4-4930-8d66-c4df8613f682.tmp | 08725ffa2d3f4d93389e589f81c5e657 | 16 |
| 2. | [SET OF RANDOM CHARACTERS].exe |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.