StrongPity
The StrongPity threat is a piece of malware that belongs to the arsenal of the Promethium APT (Advanced Persistent Threat). This hacking group was first spotted back in 2012 and has remained active to this day. In its early campaigns, the Promethium APT would mainly go after targets in Turkey and Syria. However, the hacking group has recently opted to expand its reach and has carried out attacks against targets located in India, Canada, Vietnam, and Colombia reportedly.
The StrongPity threat serves a spyware tool that is capable of exfiltrating various data types from its hosts. The Promethium APT has updated this hacking tool several times over the years. The latest iteration of the StrongPity malware is called StrongPity3 – this threat is very stealthy thanks to new and enhanced exfiltration methods combined with contemporary libraries. According to researchers, the StrongPity3 malware is propagated with the help of bogus application installs and updates. The attackers appear to use bogus copies of popular utilities like Mozilla Firefox, DriverPack, 5kPlayer, and VPNPro. To make sure that the user does not spot anything out of the ordinary, the bogus application that is used to deliver the StrongPity malware would spawn a copy of the utility, which works as intended. This way, the user may not realize that the application they have installed is responsible for delivering the payload of the StrongPity threat.
The evolution from StrongPity2 to StrongPity3 brought a few minor differences to the malware. In StrongPity3, the threat actors replaced libcurl with winhttp, which performs all requests to the C&C (Command & Control) servers. The utilization of the HKCU\Software\Microsoft\Windows\CurrentVersion\Run registry key uses a persistence mechanism that's been replaced by the creation of a service. The only job of the service executable is to launch the C&C contact module upon system startup.
Table of Contents
Trojanized Applications
As previously mentioned, security researchers have come across several trojanized applications used as a distribution vehicle. The Firefox, DriverPack, and 5kplayer trojanized installers use a service in order to achieve persistence, while VPNpro uses an AutoRun registry key. The fake Firefox installer, for example, adds the directories used by the StrongPity3 malware to the Windows Defender exclusions list through a PowerShell command, preventing sample submissions in the process. Subsequently, the installer will check if antivirus software is installed on the system before dropping the malware. If specific programs are detected, the installer will not deploy the malware.
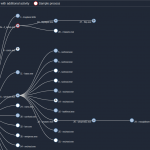
The 5kplayer trojanized installer, on the other hand, deploys three files that are part of the toolset. The setup will execute the first file, named rmaserv.exe, which is used to launch the remaining two modules once it is run as a service.
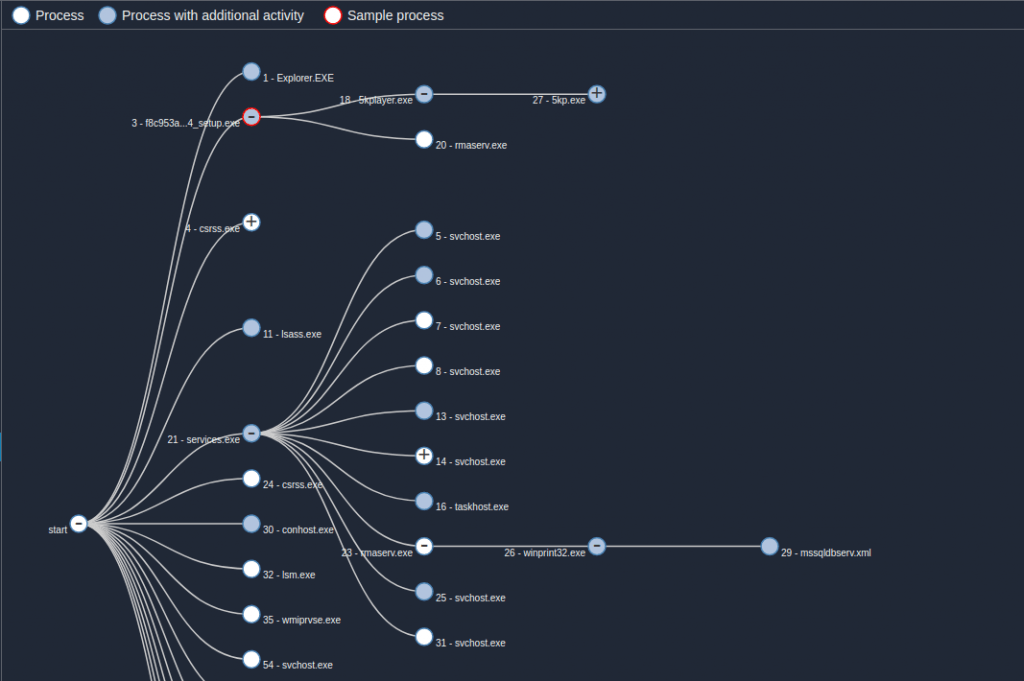
Execution flow. Source: blog.talosintelligence.com
The second file is the winprint32.exe module, which is responsible for launching the mssqldbserv.xml document search module, contacting the C&C servers, and exfiltrating the documents collected by mssqldbserv.xml anytime it detects Explorer is running.
Once the StrongPity malware is running on the targeted system, it will look for certain filetypes. When the StrongPity threat detects a file that matches its criteria, it will create a copy of it and exfiltrate it to the C&C server of the attackers. Recently, the Promethium APT has set up over thirty new C&C servers, which are meant to be used with the StrongPity malware. The StrongPity malware is able to gain persistence on the compromised host by spawning a new Windows Service, which is designed to launch the threat whenever the user reboots their system.
The Promethium APT is a very threatening hacking group, and its signature tool is the StrongPity malware. This is why it is unlikely that the Promethium hacking group would soon abandon the StrongPity project. If you want your system free of the StrongPity malware, it is advisable to install a reputable antivirus software suite, which will not allow this pest anywhere near your PC and your data.
StrongPity Screenshots
URLs
StrongPity may call the following URLs:
| app-system2-update.com |
| apt5-secure3-state.com |
| awe232-service-app.com |
| cdn2-system3-secrv.com |
| file3-netwk-system.com |
| fileservingpro.com |
| hostoperationsystems.com |
| inhousesoftwaredevelopment.com |
| mailtransfersagents.com |
| mentiononecommon.com |
| ms-sys-security.com |
| ms21-app3-upload.com |
| ms6-upload-serv3.com |
| mx3-rewc-state.com |
| network-msx-system33.com |
| safecopydisk.com |
| secure-upd21-app2.com |
| service-net2-file.com |
| state-awe3-apt.com |
| syse-update-app4.com |
| system2-access-sec43.com |
| system2-cdn5-mx8.com |
| upd-ncx4-server.com |
| upd3-srv-system-app.com |
| upd32-secure-serv4.com |
| upd8-sys2-apt.com |
| update5-sec3-system.com |
| updt-servc-app2.com |