SmokeLoader
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Popularity Rank: | 6,416 |
| Threat Level: | 80 % (High) |
| Infected Computers: | 6,769 |
| First Seen: | December 15, 2012 |
| Last Seen: | January 10, 2026 |
| OS(es) Affected: | Windows |
Criminals can use a data collector Trojan named Smoke Loader to collect information from a victim's computer. Computer users working for large businesses or organizations seem to be the targets of SmokeLoader attacks, often attempting to collect important data or gain access to a network or servers in search of a large payout. It seems that criminals can develop custom versions of SmokeLoader to carry out specific attacks depending on the target and the needs of the attackers. SmokeLoader was installed on the victim's computer in association with a different Trojan, TrickBot, which is used to carry out the initial phase of the attack. It seems that the initial phase of the attack comes from a corrupted Microsoft Word document attached to a spam email message, which will often use embedded macro scripts to download and install TrickBot and then SmokeLoader onto the victim's computer.
Table of Contents
There’s no Smoke to Cover a SmokeLoader Attack
SmokeLoader is designed in a modular way, which allows criminals to customize it for a variety of purposes. The most common use for SmokeLoader is for collecting credentials from the infected computers. SmokeLoader can be used to collect information and credentials from a wide variety of software sources and locations on the targeted computer. Criminals can easily expand on the SmokeLoader attack or update this threat through its modules. SmokeLoader will exploit several known vulnerabilities in the Windows operating system, making it essential that computer users ensure that their machines are protected with all the latest security patches and updates from Microsoft and their software's developers properly. SmokeLoader seems to target vulnerabilities in the Windows Explorer, which have been patched in 2018 (although many computer users are still unprotected). SmokeLoader is capable of detecting whether it is running in a virtual environment or similar computer used by PC security researchers to study threats like SmokeLoader, apart from carrying out its attack.
How SmokeLoader Carries Out Its Attack
There are numerous modules that can be used in the SmokeLoader attack. SmokeLoader has four major plugins that can be used to carry out different attacks currently:
- The first SmokeLoader plugin includes more than two thousand functions and allows criminals to collect passwords and credentials from a wide variety of programs, including Web browsers, FTP clients, email clients, and numerous other popular programs.
- The second SmokeLoader plugin is used to search for files on the infected computer, and can be used to collect these files and upload them to a remove server.
- The third SmokeLoader plugin associated with SmokeLoader will copy Web browser copies and can intercept HTTP and HTTPS.
- The fourth major plugin associated with SmokeLoader will attempt to collect credentials from various data transfer protocols, including IMAP, POP3, SMTP, and FTP, and can be used to collect files and emails received by the affected computer.
Dealing with a SmokeLoader Infection
SmokeLoader carries out a highly-effective data collecting attack on the victim's computer and is considered a serious danger to the victims' data and privacy. SmokeLoader is a sophisticated threat that can be used against high-level targets such as businesses and government organizations. SmokeLoader can be used for espionage, as well as other operations. SmokeLoader can move through a network and spread within a computer or from one computer to another when operated by the criminals from a remote location. The best protection against threats like SmokeLoader includes having strong security software, strong policies for computer access, and strong passwords. Since threats like SmokeLoader tend to exploit vulnerabilities in Windows and software, it is important to have protocols for updating and keeping all software and operating systems up-to-date at all time with the latest security patches.
SpyHunter Detects & Remove SmokeLoader
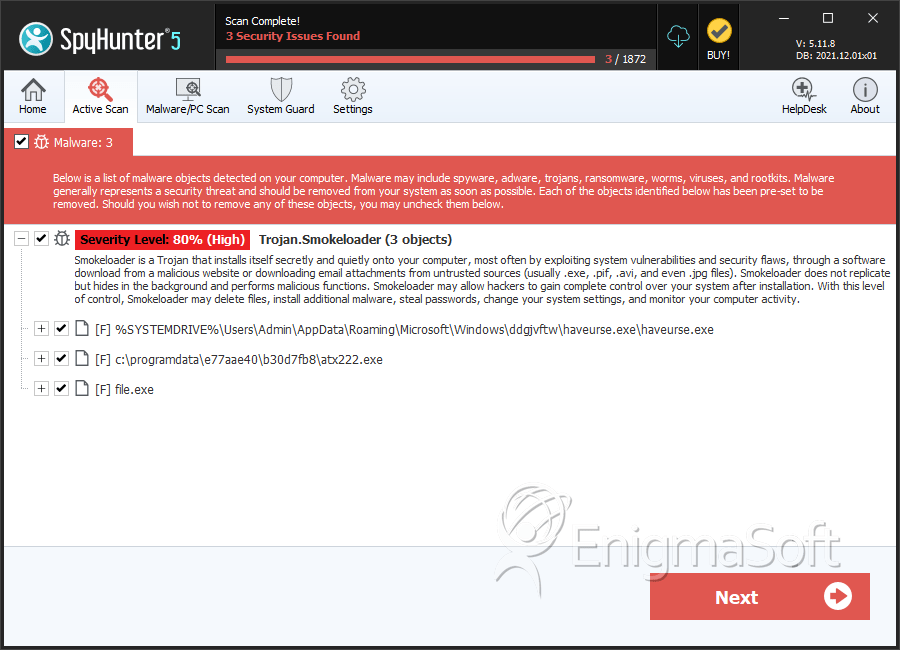
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | haveurse.exe | 7ae3cee8c55e38122a8fc04c7a65ad09 | 5,180 |
| 2. | atx222.exe | 7a2323d5dac16e3063b6c53d5dc51ab4 | 7 |
| 3. | file.exe | faab4e23a5876e096f6869c8fad14860 | 0 |
Analysis Report
General information
| Family Name: | Trojan.Smokeloader |
|---|---|
| Signature status: | No Signature |
Known Samples
Known Samples
This section lists other file samples believed to be associated with this family.|
MD5:
cdc6b8abfb117cf158bdb11c2c2ff47b
SHA1:
172e6f88744f244d9b377f90155636dd7c85396a
File Size:
321.02 KB, 321024 bytes
|
|
MD5:
90dcbdb023e8816ff866a33ea9180d23
SHA1:
bb8b47cb6dfbce8e824a5fe9e2c1ff87a821a70a
File Size:
526.85 KB, 526848 bytes
|
|
MD5:
e5d12f8dc817f4da69cc34aaf47023a1
SHA1:
82bd2ac0d706643b8be62142e6bb7c0082fff635
SHA256:
29E61106C38F28403B1F7531B692987539856561AB6A8EB7EA413435D0B16FC4
File Size:
731.14 KB, 731136 bytes
|
|
MD5:
8f865462798082ac7473e6edd13c3cf3
SHA1:
bd0ef3a8af4427a74813cc0586997bff9111ea00
SHA256:
79BF1EC4C6E4E477CA272F542F958F6A7332D1488F9A7F301CB55B4479A7254C
File Size:
801.79 KB, 801792 bytes
|
|
MD5:
8e21207b426f7f6a132c495a99ad3d1e
SHA1:
f0d0960eee4c47bc08f21f12f54a525b19590e87
SHA256:
A387AFC512E7F898D15E40039CA07BEBF2E8DAE9B726CD4915BE45D1E81F52EA
File Size:
799.74 KB, 799744 bytes
|
Show More
|
MD5:
096c0f1ccab515c63ce67b33a4a1e694
SHA1:
708dc21e5c272122954943b9243f4323b5a947a6
SHA256:
8FB3AA851FBEA348B382426F916F40D15382E1B7BF3EB9067497600820E9F8B5
File Size:
3.96 MB, 3964890 bytes
|
Windows Portable Executable Attributes
- File doesn't have "Rich" header
- File doesn't have debug information
- File doesn't have exports table
- File doesn't have relocations information
- File doesn't have security information
- File is 32-bit executable
- File is either console or GUI application
- File is GUI application (IMAGE_SUBSYSTEM_WINDOWS_GUI)
- File is Native application (NOT .NET application)
- File is not packed
Show More
- IMAGE_FILE_DLL is not set inside PE header (Executable)
- IMAGE_FILE_EXECUTABLE_IMAGE is set inside PE header (Executable Image)
File Icons
File Icons
This section displays icon resources found within family samples. Malware often replicates icons commonly associated with legitimate software to mislead users into believing the malware is safe.Windows PE Version Information
Windows PE Version Information
This section displays values and attributes that have been set in the Windows file version information data structure for samples within this family. To mislead users, malware actors often add fake version information mimicking legitimate software.| Name | Value |
|---|---|
| File Description |
|
| File Version | 1.00 |
| File Verus | 1.0.2.27 |
| Files Version | 21.21.28.6 |
| Internal Name |
|
| Legal Copyright | Copyright (C) 2023, historic |
| Legal Trademark1 | DoesntGet |
| Original Filename |
|
| Product Name |
|
| Product Version |
|
| Product Versus | 1.5.8.28 |
| Production Version |
|
| Products Version |
|
File Traits
- HighEntropy
- x86
Windows API Usage
Windows API Usage
This section lists Windows API calls that are used by the samples in this family. Windows API usage analysis is a valuable tool that can help identify malicious activity, such as keylogging, security privilege escalation, data encryption, data exfiltration, interference with antivirus software, and network request manipulation.| Category | API |
|---|---|
| Other Suspicious |
|
