Searchcore.net
Searchcore.net Image
Table of Contents
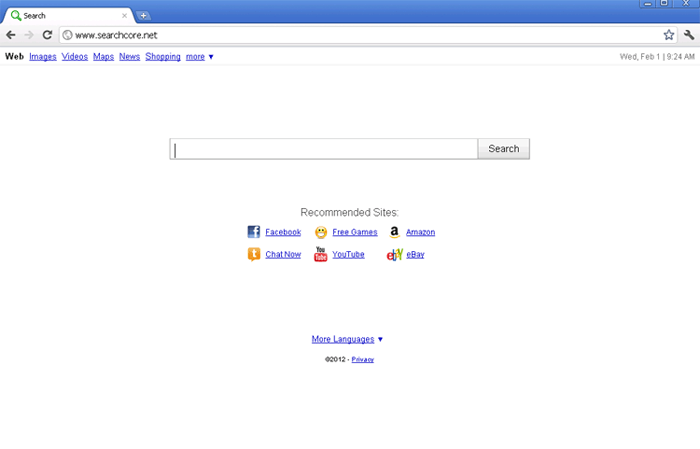
Searchcore.net – A Bogus Search Engine that Plagiarizes Google
At first glance, Searchcore.net appears to be Google without the Google logo. The menu at the top of the page, the color scheme and the layout of the page was all designed to imitate the Google search engine. If plagiarism and lack of originality were the only things wrong with Searchcore.net, then there would be little reason to be worried about this fake search engine. However, the dangerous aspect of Searchcore.net is the fact that criminals use browser hijackers in order to boost this web page's traffic artificially. According to ESG security researchers, Searchcore.net has no real search capabilities – that is, Searchcore.net does not have any kind of search algorithm or directory in order to display conclusions that are consistent with the keywords its visitors enter. Rather, Searchcore.net will display a list of advertisements and links to various malicious websites regardless of its visitors' searches. This means that the results on a Searchcore.net search will be irrelevant at best, and will often actively promote seedy websites involved in various online scams or will try to sell various products and services that may put your computer system's security in danger. If you have had any contact with Searchcore.net, and especially if you are being forced to visit Searchcore.net repeatedly, ESG security analysts recommend the utilization of a dedicated anti-malware application to search for malware on your computer. A redirect to Searchcore.net is a definite sign of a browser hijacker infection.
Understanding the Searchcore.net Scam
Searchcore.net is part of a well-known online scam which consists in setting up fake search engines which are actually designed to display advertisements. These scams online are quite common. In fact, if you mistype the URL for various popular websites, you are probably going to end up at one of these spam-ridden search engines (this particular kind of website is known as a typosquatter). In the case of Searchcore.net, criminals force their victims to visit this website repeatedly. This is done by infecting the victim's computer system with a Trojan infection known as a browser hijacker. A browser hijacker takes over the victim's computer system and forces the web browsers to direct the victim to Searchcore.net after carrying out a search, entering a URL clicking on a link or into the address bar. Trojans associated with Searchcore.net, in particular, will change the results on legitimate online searches so that the results will lead to Searchcore.net instead of to the website corresponding to that search result.
File System Details
| # | File Name |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|
| 1. | %Documents and Settings%\Application Data\[RANDOM CHARACTERS].exe | |
| 2. | %Documents and Settings%\Application Data\[RANDOM CHARACTERS].dll | |
| 3. | %Documents and Settings%\Application Data\~r | |
| 4. | %Documents and Settings%\All Users\Application Data\~ |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.