RARSTONE
 RARSTONE is a RAT (Remote Access Tool), which was used in targeted attacks against Asian organizations. RARSTONE was utilized in a cybercriminal campaign, dubbed Naikon, that targeted communications, oil, government, media and other types of organizations in Asia. The name stems from a string found in related attacks (NOKIAN95/WEB).
RARSTONE is a RAT (Remote Access Tool), which was used in targeted attacks against Asian organizations. RARSTONE was utilized in a cybercriminal campaign, dubbed Naikon, that targeted communications, oil, government, media and other types of organizations in Asia. The name stems from a string found in related attacks (NOKIAN95/WEB).
Targeted attacks initiated by RARSTONE that root from Asian areas of the world are often carried out utilizing spear-phishing techniques. Such techniques involve targeting a specific organization using messages that entice such an organization. Fundamentally, the spear-phishing methods use messages that are directly related to the target using subjects that those at the targeted entity would relate to or understand.
The RARSTONE RAT was used in expanded operations all across Asia, with a many industries hit with it: telecommunications, oil and gas companies, governments, media outlets and more. Many of the targets were located in Vietnam, Singapore, Malaysia and India.
RARSTONE Goes Spear-Phishing to Zone-In on Specific Targets
During the attacks of RARSTONE, the cybercriminals behind the threat sent out spear-phishing emails that allegedly included documents pertaining to diplomatic discussions in the Asia-Pacific region. When the victims opened the documents attached to the emails, the threat exploited a Windows vulnerability (CVE-2012-0158) in common control to inject RARSTONE into the victim's computer system. In the meantime, RARSTONE also dropped a decoy document in an attempt to not raise suspicion. Once it found itself on a device, RARSTONE downloaded a backdoor component from a command and control C2 server directly to the memory. This enabled the malware infection to go undetected by numerous security applications. RARSTONE checked the Uninstall Registry Key and used it to find out what programs were installed on the PC. The applications that could interfere with its functions were uninstalled and deleted. RARSTONE communicated with a C2 server via SSL to secure the connection and to ensure infected traffic blends in with genuine traffic.
Phishing emails were making the rounds around the first time the RARSTONE RAT appeared, containing a .DOC file that drops and executes RARSTONE. The Trojan in turn dropped two more files:
- %System%\ymsgr_tray.exe – A copy of the RARSTONE RAT
- %Application Data%\profile.dat – A file containing the malware routines
The RARSTONE RAT connects to websites and performs routines, such as shown in Figure 1 below for processes of mapping out files and directories, downloading, uploading and executing files, as well as updating itself. The backdoor routine has the ability to get installer properties from Uninstall Registry Key entries. That allows it to take information about installed applications on the infected system, as well as knowing how to uninstall applications. That may have been used by attackers to quietly uninstall applications that target the backdoor's routine, such as antimalware software.
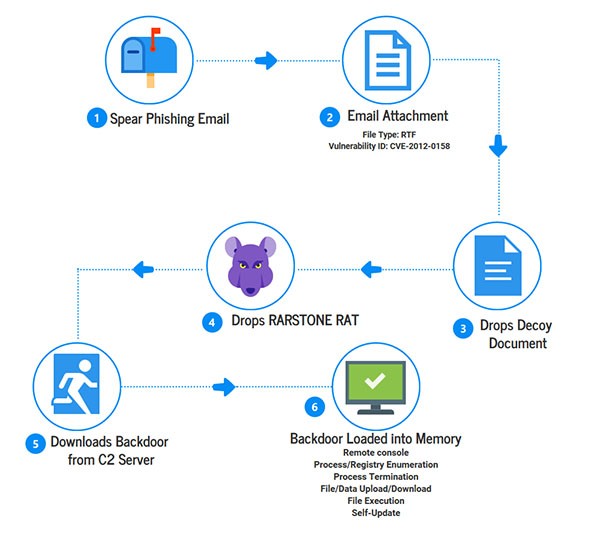
Figure 1: The RARSTONE infection process
RARSTONE was similar to another RAT named PlugX. The main feature to distinguish RARSTONE was the use of the registry keys to check for software that could hinder the cybercriminals' efforts. Another measure the criminals took was to use dynamic DNS domains, or registrars with privacy protection.'
Threats like RARSTONE are unique from PlugX and other RATs as they have the ability to get installer properties from the registry keys within the attacked Windows computer. Many of the targeted attacks of RARSTONE are part of larger campaigns that are initially designed to evade detection while they steal information from their targets. Combating RARSTONE and similar threats usually will require technologies to identify suspicious network traffic and computer activity, which can be found in some anti-malware solutions.


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.