PWS:Win32/Zbot.gen!AK
PWS:Win32/Zbot.gen!AK is Trojan that enables attackers to obtain full remote access and control over the targeted PC, and steals confidential information, such as online shopping and banking passwords, email credentials and network information from affected computer users. PWS:Win32/Zbot.gen!AK proliferates and installs itself on the victimized computer system with the help of other malware infections, can be downloaded as a payload for exploit kits such as blackhole, detected as Blacole, or is spread via spam email out attachments. When activated, PWS:Win32/Zbot.gen!AK creates a modified copy of itself with a randomly-generated file name in the specific location. PWS:Win32/Zbot.gen!AK then modifies the Windows Registry to make sure that this copy is run every time you boot up Windows. PWS:Win32/Zbot.gen!AK also replicates itself in the default user startup folder. PWS:Win32/Zbot.gen!AK embeds a code into all running processes of the victimized computer to hide its occurrence from security applications. PWS:Win32/Zbot.gen!AK strives to distribute itself to other PCs that might be remotely connected to the infected computer using the Remote Desktop Service (RDS).
Table of Contents
SpyHunter Detects & Remove PWS:Win32/Zbot.gen!AK
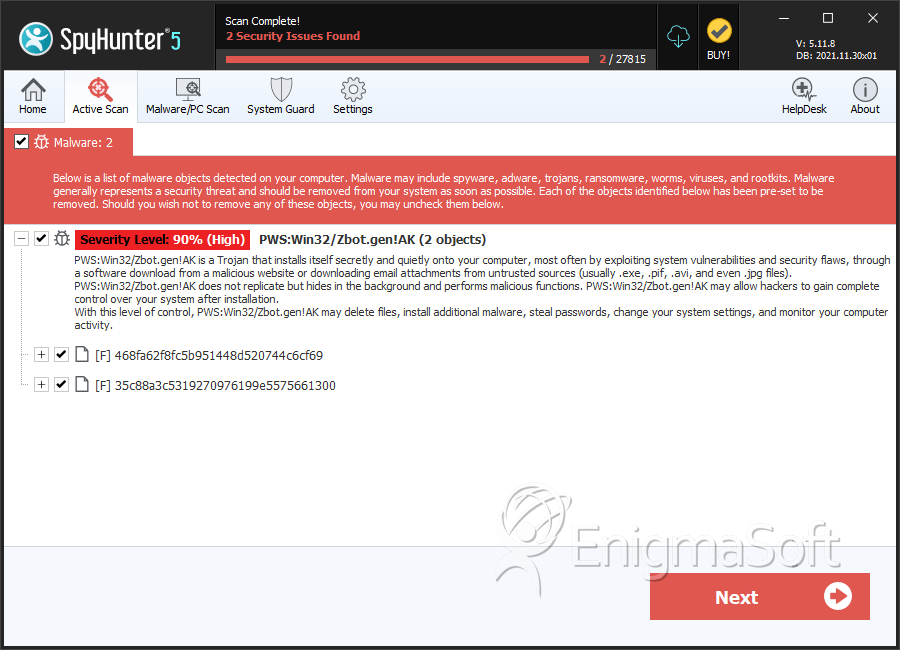
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | \Programs\Startup\.exe | ||
| 2. |
C:\Documents and Settings\ |
||
| 3. |
C:\Documents and Settings\ |
||
| 4. |
C:\Users\ |
||
| 5. | %APPDATA%\\.exe | ||
| 6. | C:\Users\\\Programs\Startup\.exe | ||
| 7. | C:\Documents and Settings\\\Programs\Startup\.exe | ||
| 8. | 468fa62f8fc5b951448d520744c6cf69 | 468fa62f8fc5b951448d520744c6cf69 | 0 |
| 9. | 35c88a3c5319270976199e5575661300 | 35c88a3c5319270976199e5575661300 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.