PWSteal.Fareit
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 80 % (High) |
| Infected Computers: | 296 |
| First Seen: | October 25, 2011 |
| OS(es) Affected: | Windows |
PWSteal.Fareit is a terrible Trojan that is a dangerous threat to your computer system and personal information. PWSteal.Fareit can drop other high-risk malware infections and is difficult to detect, because some PWSteal.Fareit's files use a rootkit method to disguise the processes of PWSteal.Fareit. If you spot the malicious application running inside your Windows system, delete all infected files and uninstall PWSteal.Fareit from your machine as early as you can. PWSteal.Fareit uses software packing procedures to access your PC system. PWSteal.Fareit can collect your private details and drop other malware threats. After successful installation, PWSteal.Fareit will restrict you from accessing Windows Registry and Task Manager, and won't allow you to delete the essential components of PWSteal.Fareit. The malicious components of PWSteal.Fareit can send emails via SMTP protocols, contact other PCs, download unsafe content from the web, generate IE toolbar extensions (iexplore.exe) and even trace your browsing activities. These files cannot be detected by actual security software and work together to disable Windows Security Center processes. Remove PWSteal.Fareit before it harms your computer system.
Table of Contents
Aliases
15 security vendors flagged this file as malicious.
| Anti-Virus Software | Detection |
|---|---|
| Panda | Trj/OCJ.E |
| AVG | PSW.Generic11.IWK |
| Fortinet | W32/Tepfer.JCRZ!tr.pws |
| BitDefender | Gen:Variant.Zusy.45431 |
| Kaspersky | Trojan-PSW.Win32.Tepfer.jcrz |
| Avast | Win32:Downloader-TCM [Trj] |
| McAfee | Artemis!5957EEF06CE4 |
| Panda | Trj/Dtcontx.A |
| AVG | SHeur4.AZNP |
| Fortinet | W32/Yakes.BRQC!tr |
| Ikarus | Virus.Win32.CeeInject |
| AhnLab-V3 | Dropper/Win32.Dapato |
| TrendMicro | TROJ_RANSOM.SMC8 |
| AntiVir | TR/Agent.94208 |
| Sophos | Mal/EncPk-AGE |
SpyHunter Detects & Remove PWSteal.Fareit
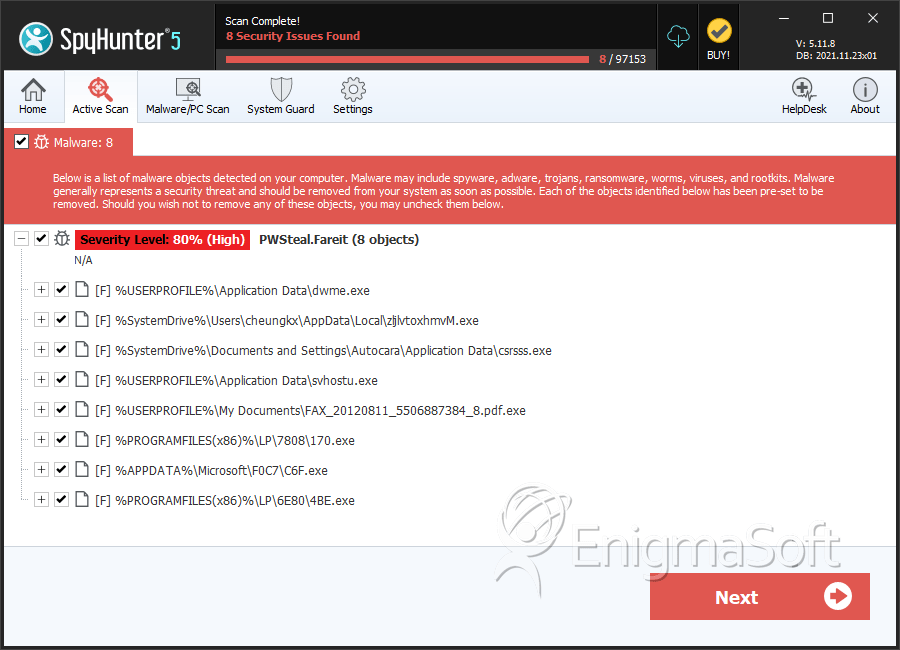
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | dwme.exe | cc6f0b2fd70c63672de6c1249f0e9cbb | 137 |
| 2. | zljlvtoxhmvM.exe | 22f6f8064d43c9271574ef0d2698889c | 49 |
| 3. | csrsss.exe | 80f0c02e7f858d1cd74b324c3a61e3e8 | 23 |
| 4. | csrsss.exe | d974a50833111e26cecd0ecd7d36bcf6 | 15 |
| 5. | svhostu.exe | 0f98a3a23e013479bffab7f233ce39a4 | 14 |
| 6. | FAX_20120811_5506887384_8.pdf.exe | f060ba7a5a4660494cce673c24feb15f | 9 |
| 7. | java.exe | 287b3de0d02e964678c18a990c7502e0 | 8 |
| 8. | 170.exe | 9c4243b8df3c2b0eb069c18b3afaf608 | 6 |
| 9. | C6F.exe | f447a6233c1d8f26183ec9835d2754d3 | 5 |
| 10. | 4BE.exe | 4651d7e2baa354742863ea2d1ce66872 | 3 |
| 11. | 06D.exe | 4d722ed619351b71d585a0adc5a5370d | 2 |
| 12. | java.exe | c1c763dd72fe3f55c2ffe0e5833743ad | 2 |
| 13. | EAA.exe | 10dd6fc881e4f09d7da5036d5833ffd7 | 1 |
| 14. | 644.exe | 8023bde63e18907c9fb614749ddf1952 | 1 |
| 15. | iexplore.exe | 0fa353ae401cf237fb06de60734c8444 | 1 |
| 16. | YOUTUBE.PLAYER.exe | 0e90bb9ddcb98e1e2759858b0b74bbce | 1 |
| 17. | msromko.com | 5957eef06ce4f0f930925651dbb40ade | 1 |
| 18. | gwkkIIVrlON.exe | ||
| 19. | nHH55sWJJ7EL8RZ.exe | ||
| 20. | fcunfcogfupdt32.dll | ||
| 21. | 6B9.exe | ||
| 22. | 7D7.exe | ||
| 23. | 8B8.exe | ||
| 24. | F7ddEL8gTZqYCkV.exe | ||
| 25. | d000uvvS2ibFpn5.exe | ||
| 26. | 306.exe | ||
| 27. | wmplayer.exe | ||
| 28. | 4D7.exe | ||
| 29. | GoogleNotifierOnline.dll | ||
| 30. | 14247e.exe | ||
| 31. | 93F.exe | ||
| 32. | C6F.exe | ||
| 33. | hWWWK77fRL9g.exe | ||
| 34. | djjUUCeekIrzPyA.exe | ||
| 35. | A66ssWKK7fE9gZq.exe | ||
| 36. | E33.exe | ||
| 37. | 8EE.exe | ||
| 38. | 41816797-5016.exe | ||
| 39. | be792753.dll | ||
| 40. | A89.exe | ||
| 41. | AE947CD1935.exe | ||
| 42. | kdhr.exe | ||
| 43. | 4c770a9bd1e8373a1ebd4a9f2245c315 | 4c770a9bd1e8373a1ebd4a9f2245c315 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.