PUP.Turbo VPN
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Popularity Rank: | 330 |
| Threat Level: | 10 % (Normal) |
| Infected Computers: | 52,957 |
| First Seen: | March 17, 2022 |
| Last Seen: | February 1, 2026 |
| OS(es) Affected: | Windows |
Table of Contents
SpyHunter Detects & Remove PUP.Turbo VPN
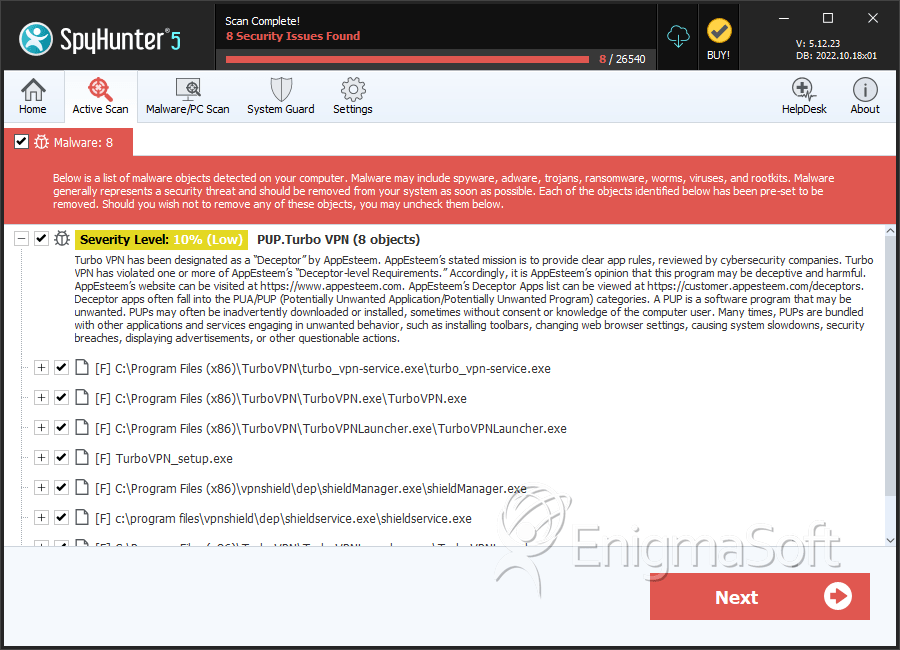
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | TurboVPNLauncher.exe | 9f5ef8f6a7e06a46ebb02e7066c660f2 | 2,526 |
| 2. | shieldManager.exe | 99b972a717c6728c5c863c51d20590ba | 1,281 |
| 3. | turbo_vpn-service.exe | cba8718cf01a7d489d00695bed5011f6 | 1,194 |
| 4. | shieldservice.exe | 8331134761d0db7b3196280e8fb9c202 | 1,185 |
| 5. | TurboVPN_setup.exe | df96bc092b1ab5a0408d6e9f1a73b040 | 539 |
| 6. | TurboVPN.exe | 781ae32e7d42865284b8a21e83e7fedd | 495 |
| 7. | vpnshield_install.exe | 7b4f897f3c16309d64f5ec8eef3f7625 | 104 |
| 8. | vpn_shield.exe | c7d27c7a545e589ba02068ea0b034978 | 81 |
Registry Details
Directories
PUP.Turbo VPN may create the following directory or directories:
| %PROGRAMFILES%\TurboVPN |
Analysis Report
General information
| Family Name: | PUP.Turbo VPN |
|---|---|
| Signature status: | Root Not Trusted |
Known Samples
Known Samples
This section lists other file samples believed to be associated with this family.|
MD5:
8c44740052fb786dac00742c07e9a174
SHA1:
ed9f5b23ac80a7984e3721f00638c18ce77c450a
File Size:
7.24 MB, 7243416 bytes
|
|
MD5:
de549711c878dbafdad8b4af411a6c23
SHA1:
c09a740c9337cebec8e2955124bd737740142db3
File Size:
1.51 MB, 1511208 bytes
|
|
MD5:
646056d5dad9f7202ab51dfd31a97103
SHA1:
4b141385ba8de4fef3389004ac88e28947acc010
SHA256:
0F6E484109123A81102A8738D8BAE45EEA4E39370113B6D01C742B30E2A637BB
File Size:
3.14 MB, 3139584 bytes
|
|
MD5:
94880054fae8150736ddd0940cf3d052
SHA1:
1cef9367490f6dbae44e0c06a30ed6901eb51f72
SHA256:
64FF17EA1B755078EB71910CA6705327724CAD87D6B83528487EAE4A0EE48AD7
File Size:
570.53 KB, 570527 bytes
|
|
MD5:
b55ba4ab6d14a0a6970a4c1b7e41ea3c
SHA1:
6b2423dd680c30db43cec317d23318d1f6208f0d
SHA256:
006AF2C668ABADBEE3F5E09494B05070FE63E3C9A66141B494FF053F4213346C
File Size:
7.45 MB, 7453400 bytes
|
Show More
|
MD5:
987fdf7e056940e7c168a8b36ca92a7b
SHA1:
5093cf5854a2bcdc5900073c8846c617e782411a
SHA256:
4DFE0CABC8E90401CB0E1A12054C6F630230B4DA43052551C1E360BA8BB65A23
File Size:
213.14 KB, 213144 bytes
|
|
MD5:
f0b68b4fe175f02fa094f7dfad99bc06
SHA1:
153d3fe4e46b8c54323b07902dea4863e80d6d08
SHA256:
F2EED5CF684E6D33D15F1DD1402C4EA885F85EAE5C10AEE0A31364BB7C22EE62
File Size:
7.46 MB, 7455960 bytes
|
|
MD5:
35ffcd64dad49bbb380379553421efa8
SHA1:
ca556d3306fcf6e782dd457944a4437c66c8ab05
SHA256:
7B4FDA9BC9415E3859E6FFDC49F280AB21CEFD7158F2DD405375B6D8BE4EB790
File Size:
3.66 MB, 3662101 bytes
|
|
MD5:
9aaf163322a412c654f94808bf8b06d2
SHA1:
cefe8c75414743a7073c0001f207e5b9a089df2d
SHA256:
46F27DFEB41681BED5B9568D0126B33AA7EFC571DA0A84772B52D1F670CF9324
File Size:
749.67 KB, 749671 bytes
|
|
MD5:
a8579d02d10fe0905d1374f357a12edd
SHA1:
09935471031fffdde3cc65c21f007c948478c7f2
SHA256:
3AF4D6B4CD79830AD8A5746A197A3A1D4EC04C997FA296D0F4286E83FA248A54
File Size:
1.51 MB, 1511192 bytes
|
|
MD5:
d4885f1cd65dc17870c2043b63659d4b
SHA1:
2613ca41844a1ff87ffe7711638a5a0ce5c2d4cb
SHA256:
5E18D9FFD9F0CB39AEA3024BB24B0C3BB28F4AED1E9C03CDA63BD3296407B766
File Size:
1.51 MB, 1511512 bytes
|
|
MD5:
8916651bc99b4b64edf735fdda2fc0f7
SHA1:
c668632d4b3db8b957ed7b9785655728fe4f2556
SHA256:
4C3D5F864D0EBFAFA74EA0B68D22B93EF40D26F9224246BB239286C16DB3B8AE
File Size:
7.47 MB, 7473368 bytes
|
|
MD5:
d826ca74a2d83a6e5909da48a642ff3b
SHA1:
888b1901daa4505a181ebdc6a03258ea46caea3d
SHA256:
5A63B628AA400BDB116A955CCA8B8126FAB9E7C016AEA35D7700556DA7607EB8
File Size:
1.80 MB, 1798773 bytes
|
|
MD5:
a061a4a8dac4df34fb139637394fa0db
SHA1:
84dca533e1f27a6a52e9ca026866a5217f44c2f4
SHA256:
462BEED5FED8BF1783394C23AB2C737137043C061A25516361C2A0D351E016CF
File Size:
7.47 MB, 7473368 bytes
|
|
MD5:
9ea227083f4efd382476cc47ca8b21da
SHA1:
65da92a868db84d9daa240bc4e1bd30e19a6ad84
SHA256:
BAEFD3EDCD88177C4B9A2FB77302B6CFE7F7B358AF5B50E6834C627C663F3587
File Size:
1.51 MB, 1511512 bytes
|
|
MD5:
aa1f82f17c95a0fb0d29409e0f98a4e1
SHA1:
845f282b4669406a4ebf4bd498330c3f0cd66637
SHA256:
36043E09D52C69D284B250462240CEF8CB4FCAA3216F2A487AAEBDB03F34CFDD
File Size:
586.62 KB, 586618 bytes
|
Windows Portable Executable Attributes
- File doesn't have "Rich" header
- File doesn't have debug information
- File doesn't have exports table
- File doesn't have relocations information
- File doesn't have security information
- File has exports table
- File has TLS information
- File is 32-bit executable
- File is console application (IMAGE_SUBSYSTEM_WINDOWS_CUI)
- File is either console or GUI application
Show More
- File is GUI application (IMAGE_SUBSYSTEM_WINDOWS_GUI)
- File is Native application (NOT .NET application)
- File is not packed
- IMAGE_FILE_DLL is not set inside PE header (Executable)
- IMAGE_FILE_EXECUTABLE_IMAGE is set inside PE header (Executable Image)
File Icons
File Icons
This section displays icon resources found within family samples. Malware often replicates icons commonly associated with legitimate software to mislead users into believing the malware is safe.Windows PE Version Information
Windows PE Version Information
This section displays values and attributes that have been set in the Windows file version information data structure for samples within this family. To mislead users, malware actors often add fake version information mimicking legitimate software.| Name | Value |
|---|---|
| Comments |
|
| Company Name |
|
| File Description |
|
| File Version |
|
| Internal Name |
|
| Legal Copyright |
|
| Legal Trademarks |
|
| Original Filename |
|
| Product Name |
|
| Product Version |
|
Digital Signatures
Digital Signatures
This section lists digital signatures that are attached to samples within this family. When analyzing and verifying digital signatures, it is important to confirm that the signature’s root authority is a well-known and trustworthy entity and that the status of the signature is good. Malware is often signed with non-trustworthy “Self Signed” digital signatures (which can be easily created by a malware author with no verification). Malware may also be signed by legitimate signatures that have an invalid status, and by signatures from questionable root authorities with fake or misleading “Signer” names.| Signer | Root | Status |
|---|---|---|
| INNOVATIVE CONNECTING PTE. LIMITED | DigiCert Trusted Root G4 | Root Not Trusted |
| INNOVATIVE CONNECTING PTE. LIMITED | DigiCert Trusted Root G4 | Hash Mismatch |
| INNOVATIVE CONNECTING PTE. LIMITED | Symantec Class 3 Extended Validation Code Signing CA - G2 | Hash Mismatch |
File Traits
- 2+ executable sections
- Inno
- InnoSetup Installer
- Installer Manifest
- Installer Version
- nosig nsis
- Nullsoft Installer
- VirtualQueryEx
- x86
Block Information
Block Information
During analysis, EnigmaSoft breaks file samples into logical blocks for classification and comparison with other samples. Blocks can be used to generate malware detection rules and to group file samples into families based on shared source code, functionality and other distinguishing attributes and characteristics. This section lists a summary of this block data, as well as its classification by EnigmaSoft. A visual representation of the block data is also displayed, where available.Similar Families
Similar Families
This section lists other families that share similarities with this family, based on EnigmaSoft’s analysis. Many malware families are created from the same malware toolkits and use the same packing and encryption techniques but uniquely extend functionality. Similar families may also share source code, attributes, icons, subcomponents, compromised and/or invalid digital signatures, and network characteristics. Researchers leverage these similarities to rapidly and effectively triage file samples and extend malware detection rules.- Injector.AK
- Lumma.GFD
- Rugmi.IA
- Sheloader.A
- Stealer.KF
Files Modified
Files Modified
This section lists files that were created, modified, moved and/or deleted by samples in this family. File system activity can provide valuable insight into how malware functions on the operating system.| File | Attributes |
|---|---|
| c:\users\user\appdata\local\temp\nsf84d.tmp\nsniuniuskin.dll | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\nsf84d.tmp\skin.zip | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\nsg6442.tmp\nsniuniuskin.dll | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\nsg6442.tmp\skin.zip | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\nsi7b98.tmp\nsniuniuskin.dll | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\nsi7b98.tmp\skin.zip | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\nso507e.tmp\nsniuniuskin.dll | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\nso507e.tmp\skin.zip | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\~nsu.tmp\au_.exe | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete,LEFT 262144 |
| c:\users\user\appdata\local\temp\~nsua.tmp\un_a.exe | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete,LEFT 262144 |
Registry Modifications
Registry Modifications
This section lists registry keys and values that were created, modified and/or deleted by samples in this family. Windows Registry activity can provide valuable insight into malware functionality. Additionally, malware often creates registry values to allow itself to automatically start and indefinitely persist after an initial infection has compromised the system.| Key::Value | Data | API Name |
|---|---|---|
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Users\Hpldutbx\AppData\Local\Temp\~nsu.tmp\Au_.exe | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Users\Hpldutbx\AppData\Local\Temp\~nsu.tmp\Au_.exe��\??\C:\Users\Hpldutbx\AppData\Local\Temp\~nsu.tmp | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Program Files (x86)\Microsoft\EdgeUpdate\1.3.205.9��\??\C:\Windows\SystemTemp\b1a39cca-eadf-4949-a384-a0ef6a3b3fd2.tmp��\ | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | *1\??\C:\Windows\SystemTemp\MicrosoftEdgeUpdate.exe.old122e4��*1\??\C:\Windows\SystemTemp\CopilotUpdate.exe.old12352��*1\??\C:\P | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | *1\??\C:\Windows\SystemTemp\MicrosoftEdgeUpdate.exe.old5af52��*1\??\C:\Windows\SystemTemp\CopilotUpdate.exe.old5af62��*1\??\C:\P | RegNtPreCreateKey |
Windows API Usage
Windows API Usage
This section lists Windows API calls that are used by the samples in this family. Windows API usage analysis is a valuable tool that can help identify malicious activity, such as keylogging, security privilege escalation, data encryption, data exfiltration, interference with antivirus software, and network request manipulation.| Category | API |
|---|---|
| Process Shell Execute |
|
| Anti Debug |
|
| Keyboard Access |
|
| User Data Access |
|
| Syscall Use |
Show More
|
Shell Command Execution
Shell Command Execution
This section lists Windows shell commands that are run by the samples in this family. Windows Shell commands are often leveraged by malware for nefarious purposes and can be used to elevate security privileges, download and launch other malware, exploit vulnerabilities, collect and exfiltrate data, and hide malicious activity.
"C:\Users\Hpldutbx\AppData\Local\Temp\~nsu.tmp\Au_.exe" _?=c:\users\user\downloads\
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\5093cf5854a2bcdc5900073c8846c617e782411a_0000213144.,LiQMAxHB
|
"C:\Users\Sgbyajgo\AppData\Local\Temp\~nsu.tmp\Au_.exe" _?=c:\users\user\downloads\
|
"C:\Users\Zzxtmdvk\AppData\Local\Temp\~nsu.tmp\Au_.exe" _?=c:\users\user\downloads\
|
"C:\Users\Mjcjmvol\AppData\Local\Temp\~nsu.tmp\Au_.exe" _?=c:\users\user\downloads\
|
Show More
"C:\Users\Uifgtmke\AppData\Local\Temp\~nsuA.tmp\Un_A.exe" _?=c:\users\user\downloads\
|
