PUP.Goobzo
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Popularity Rank: | 6,372 |
| Threat Level: | 10 % (Normal) |
| Infected Computers: | 42,830 |
| First Seen: | February 20, 2014 |
| Last Seen: | February 1, 2026 |
| OS(es) Affected: | Windows |
Table of Contents
Aliases
5 security vendors flagged this file as malicious.
| Antivirus Vendor | Detection |
|---|---|
| AVG | Skodna.A8D |
| Panda | Adware/Goobzo |
| Sophos | Goobzo |
| AVG | MalSign.Skodna.A8D |
| McAfee | Artemis!D5495D2562BC |
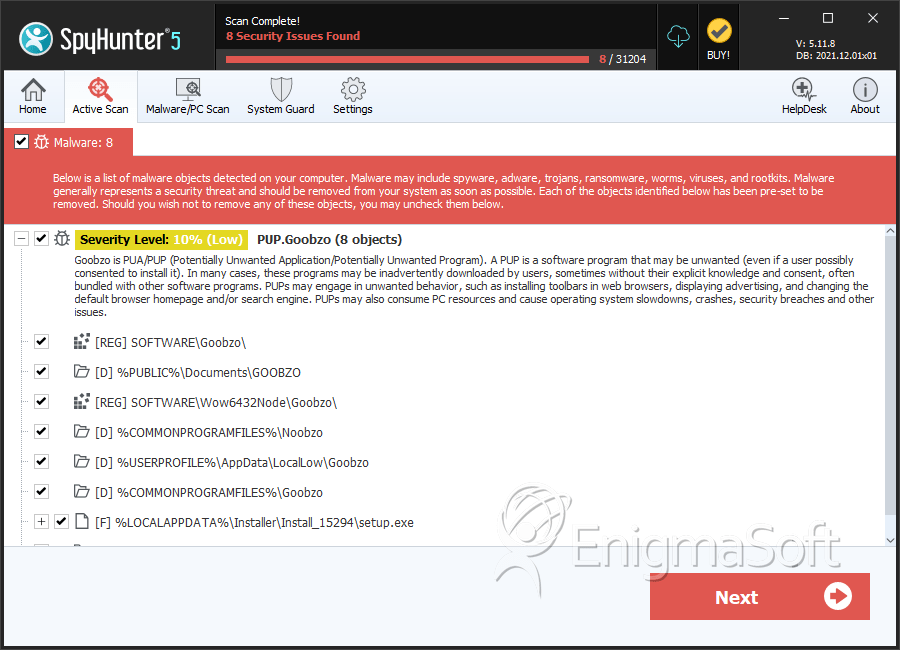
SpyHunter Detects & Remove PUP.Goobzo
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | SysMenu.dll | dca076f9531e7940d94a48f0edc3c737 | 109 |
| 2. | smp.exe | 2b22c2ad8b9ba60b0369293de8330acd | 77 |
| 3. | sma.exe | a606c1a82b9c5dfd36162da6d6065246 | 55 |
| 4. | smUninstall.exe | c901211cea52978e7b274351d976ff27 | 54 |
| 5. | smu.exe | 9dc24b911c9be29cb6bf7ccd78b790ac | 54 |
| 6. | updatehelper.exe | 5c4b34ae6efc873d881e76d95c8adc28 | 41 |
| 7. | smw.sys | 8a3b320da4865b775707a53d76cedd10 | 15 |
| 8. | delay.exe | 3526fa76385f858c44db17ef8a425a84 | 1 |
| 9. | setup.exe | e1b90326f328e4e5fe5b08191c049979 | 1 |
Registry Details
Directories
PUP.Goobzo may create the following directory or directories:
| %COMMONPROGRAMFILES%\Doobzo |
| %COMMONPROGRAMFILES%\Goobzo |
| %COMMONPROGRAMFILES%\Noobzo |
| %COMMONPROGRAMFILES%\Soobzo |
| %COMMONPROGRAMFILES(x86)%\Goobzo |
| %PUBLIC%\Documents\GOOBZO |
| %USERPROFILE%\AppData\LocalLow\Goobzo |
Analysis Report
General information
| Family Name: | PUP.Goobzo |
|---|---|
| Signature status: | No Signature |
Known Samples
Known Samples
This section lists other file samples believed to be associated with this family.|
MD5:
74a4c97ef962cea0dc4b4837190bb4fd
SHA1:
31a5a6e02776d9bbb1df9e0cc9c768816aeba785
SHA256:
983B7A803C7D96A4786556740C03A432AC472EC2FE54D71956E1FA85E806DB94
File Size:
1.27 MB, 1269696 bytes
|
|
MD5:
f6830f91583d97636dee8f7c48b9e8b1
SHA1:
302da210cad9626f0430e6483dc1f0eadcd6b908
SHA256:
5A134F5DA0320248ECACEE841191DA3BF1262CB9A889C31D5E7EE6361D93800D
File Size:
4.69 MB, 4693823 bytes
|
|
MD5:
1125260c57291a0375971e98fb19e4d1
SHA1:
dcdcad6e7ce46e2bbe3b8b7d9828318337e2d595
SHA256:
6B6BA2003C93D309173F2C13272966FC3633F30182921E12C10CBA541C4E43F7
File Size:
4.67 MB, 4667247 bytes
|
Windows Portable Executable Attributes
- File doesn't have "Rich" header
- File doesn't have debug information
- File doesn't have exports table
- File doesn't have relocations information
- File doesn't have security information
- File is 32-bit executable
- File is either console or GUI application
- File is GUI application (IMAGE_SUBSYSTEM_WINDOWS_GUI)
- File is Native application (NOT .NET application)
- File is not packed
Show More
- IMAGE_FILE_DLL is not set inside PE header (Executable)
- IMAGE_FILE_EXECUTABLE_IMAGE is set inside PE header (Executable Image)
File Icons
File Icons
This section displays icon resources found within family samples. Malware often replicates icons commonly associated with legitimate software to mislead users into believing the malware is safe.Windows PE Version Information
Windows PE Version Information
This section displays values and attributes that have been set in the Windows file version information data structure for samples within this family. To mislead users, malware actors often add fake version information mimicking legitimate software.| Name | Value |
|---|---|
| File Version |
|
| Product Version |
|
Files Modified
Files Modified
This section lists files that were created, modified, moved and/or deleted by samples in this family. File system activity can provide valuable insight into how malware functions on the operating system.| File | Attributes |
|---|---|
| \device\namedpipe\gmdasllogger | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\nsgb1a9.tmp\accdownload.dll | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\nsgb1aa.tmp | Synchronize,Write Attributes |
| c:\users\user\appdata\local\temp\nsha7b6.tmp\d1958.dll | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\nsha7b6.tmp\nk.lky | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\nsha7b6.tmp\setup.exe | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\nsha7b6.tmp\setup1.exe | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\nsl42be.tmp\accdownload.dll | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\nsl42bf.tmp | Synchronize,Write Attributes |
| c:\users\user\appdata\local\temp\nsqb198.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete |
Show More
| c:\users\user\appdata\local\temp\nss3938.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete |
| c:\users\user\appdata\local\temp\nss3939.tmp\d1958.dll | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\nss3939.tmp\nk.lky | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\nss3939.tmp\setup.exe | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\nss3939.tmp\setup1.exe | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\nssa7a6.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete |
| c:\users\user\appdata\local\temp\nsw42ae.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete |
| c:\users\user\appdata\local\temp\nszfa59.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete |
| c:\users\user\appdata\local\temp\nszfa69.tmp | Synchronize,Write Attributes |
| c:\users\user\appdata\local\temp\nszfa69.tmp\7f8371bf969c55b8 | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\nszfa69.tmp\7f8371bf969c55b8 | Synchronize,Write Attributes |
| c:\users\user\appdata\local\temp\nszfa69.tmp\d1989.dll | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\nszfa69.tmp\d1989.dll | Synchronize,Write Attributes |
| c:\users\user\appdata\local\temp\nszfa69.tmp\dc31a5a6e02776d9bbb1df9e0cc9c768816aeba785_0001269696 | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\nszfa69.tmp\dc31a5a6e02776d9bbb1df9e0cc9c768816aeba785_0001269696 | Synchronize,Write Attributes |
| c:\users\user\appdata\local\temp\nszfa69.tmp\nk.lky | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\nszfa69.tmp\nk.lky | Synchronize,Write Attributes |
| c:\users\user\appdata\local\temp\nszfa69.tmp\system.dll | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\nszfa69.tmp\system.dll | Synchronize,Write Attributes |
Registry Modifications
Registry Modifications
This section lists registry keys and values that were created, modified and/or deleted by samples in this family. Windows Registry activity can provide valuable insight into malware functionality. Additionally, malware often creates registry values to allow itself to automatically start and indefinitely persist after an initial infection has compromised the system.| Key::Value | Data | API Name |
|---|---|---|
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Users\Jpjjkrpe\AppData\Local\Temp\nszFA69.tmp\ | RegNtPreCreateKey |
Windows API Usage
Windows API Usage
This section lists Windows API calls that are used by the samples in this family. Windows API usage analysis is a valuable tool that can help identify malicious activity, such as keylogging, security privilege escalation, data encryption, data exfiltration, interference with antivirus software, and network request manipulation.| Category | API |
|---|---|
| Process Manipulation Evasion |
|
| Process Shell Execute |
|
| Anti Debug |
|
| User Data Access |
|
| Network Wininet |
|
| Network Winhttp |
|
| Keyboard Access |
|
Shell Command Execution
Shell Command Execution
This section lists Windows shell commands that are run by the samples in this family. Windows Shell commands are often leveraged by malware for nefarious purposes and can be used to elevate security privileges, download and launch other malware, exploit vulnerabilities, collect and exfiltrate data, and hide malicious activity.
"C:\Users\Jpjjkrpe\AppData\Local\Temp\nszFA69.tmp\DC31a5a6e02776d9bbb1df9e0cc9c768816aeba785_0001269696"
|
"C:\Users\Ejngewry\AppData\Local\Temp\nss3939.tmp\setup.exe"
|
"C:\Users\Ccpvdwdq\AppData\Local\Temp\nshA7B6.tmp\setup.exe"
|