PUP.Easy Ad Blocker
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Popularity Rank: | 1,615 |
| Threat Level: | 10 % (Normal) |
| Infected Computers: | 3,392 |
| First Seen: | July 8, 2023 |
| Last Seen: | January 27, 2026 |
| OS(es) Affected: | Windows |
Table of Contents
SpyHunter Detects & Remove PUP.Easy Ad Blocker
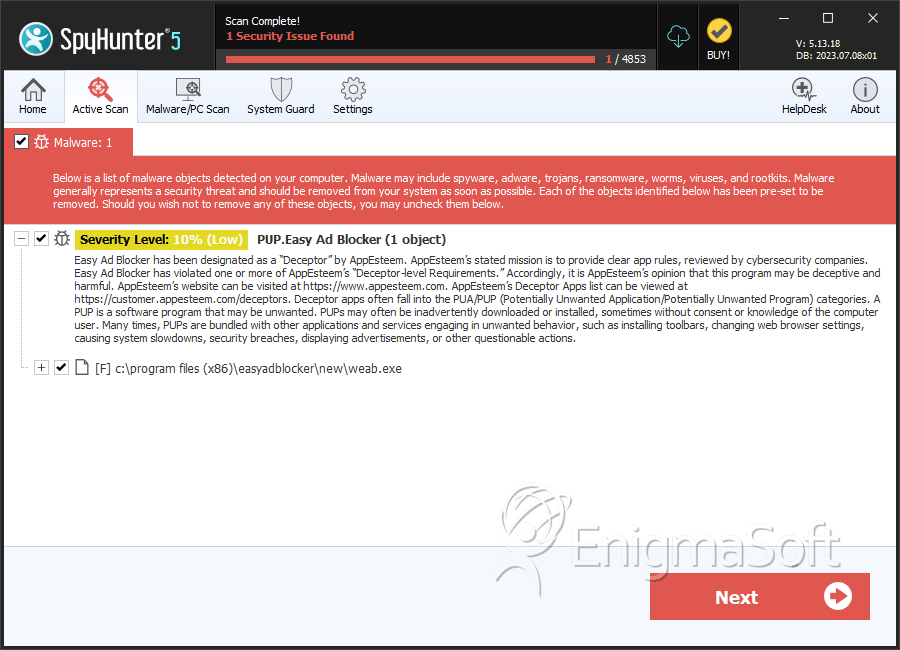
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | weab.exe | 8fb1ff7748158755ad104cfc003070fc | 423 |
| 2. | installer.exe | d1aa5fe81edb300e6ceefd29510932ec | 317 |
| 3. | $RISAB18.exe | fd62a3510ff7da8ee3c376b4685b84aa | 157 |
Analysis Report
General information
| Family Name: | PUP.Easy Ad Blocker |
|---|---|
| Signature status: | Self Signed |
Known Samples
Known Samples
This section lists other file samples believed to be associated with this family.|
MD5:
aec6c727ca5d9b1cf84288af738d3d44
SHA1:
667cae4734782771a19d01780aa0ab9af19b8852
File Size:
3.38 MB, 3377240 bytes
|
|
MD5:
5b20c00abea03df88c44cd11d0e79a92
SHA1:
a07cabab8ebd504ce01f4d8c005f69d9e3b1c27c
SHA256:
D1BF9C474F26A6E7AAF23ED6C150C57DAC5673CC61CE66FDCECF473F414DEF91
File Size:
5.86 MB, 5857088 bytes
|
|
MD5:
b60ff9cdad58e65bd1a7199961ca51a4
SHA1:
91f01a266f5064e743180e1f57c5547519381e08
SHA256:
5D81EB5B265A1AB2DDEFC41D9662E7C71EEF93E72D4A578C7CF95C37CD8AA04F
File Size:
2.65 MB, 2650264 bytes
|
|
MD5:
3e39bb5f3540c47efff1a2702736ab43
SHA1:
17bef2ff7d40be143627b263ef3e8f64b4a4d10a
SHA256:
873B3FA81DC5D8515B6E1317F2C1A4511B659DFF1BE1491A296D4D981E468752
File Size:
3.38 MB, 3377240 bytes
|
|
MD5:
e09e700657854533e66093114d73d5f9
SHA1:
ccb27432fffa81a33362b18a54ec1e013e3e5f94
SHA256:
C82CAA9F46FC532B460368E4D73B3C645232C7783194FFA44B08D43489413948
File Size:
5.86 MB, 5857136 bytes
|
Show More
|
MD5:
2e03f75f927588bf913730f79a1c09a5
SHA1:
824947364c4ce8c34769730c08625ed46e545f99
SHA256:
1ADD8CD5485AE556E1BFAC12C9490F5F786669204C7A7709A9120B5B57458C76
File Size:
3.38 MB, 3377240 bytes
|
|
MD5:
3cffe04a45bd4093f7eb0832a9c0f8ad
SHA1:
6ed2e5c191982cb7c7ad6e311ae61bd7443f7d2e
SHA256:
F69BB74A0B072656A31333C09137035A37765924A38CB58E223A951F0351CA6F
File Size:
2.65 MB, 2650336 bytes
|
|
MD5:
9e4eaf855b9a64c9068c34c158ba5522
SHA1:
8ccdb4a8cd8682cc026dada2980beb575a1b0226
SHA256:
5040A2F3C3642C577015CEABEB0875847323538A985F6F8A8A9AA3A39EDDD2B7
File Size:
5.86 MB, 5857088 bytes
|
|
MD5:
74cc680659d6da3c9efe8c79026b48e2
SHA1:
1a9d9386e4be702d8dd7232fb4c17bb6a627a483
SHA256:
6C7769F6C350C68BFEA96D2C8911DBDE7325388EC530EE9265EA3B5C8A4B360E
File Size:
3.02 MB, 3024472 bytes
|
|
MD5:
bebb51da42349b00f0ef42b708fe9faa
SHA1:
2a4e951fe85118df7231dd447baaa4e7c4c7f9d5
SHA256:
04B81728712981E1B9BEB2EC322557453F07EB14B531F460809DD978C3A550F9
File Size:
2.65 MB, 2650440 bytes
|
|
MD5:
20b6759093b8bbbd8224af32792b1f5f
SHA1:
db35277f19b7b2617d53115a8b88ddaaa984cfc4
SHA256:
C105B4DD09A07AE42B7060899F2C0D8395D3C3104E5131B28C643D42F0CECBC0
File Size:
2.65 MB, 2650192 bytes
|
|
MD5:
15ca8b53c075876f4d20393c49b38748
SHA1:
b7a9f7270ff6aae6878bb412b0c8b4ac255b2750
SHA256:
812DE76A367DBF4B2C7D6CB7B0C2735CA750041D491682D7F9A8586FF6A2AF5B
File Size:
2.66 MB, 2660965 bytes
|
|
MD5:
67826e0965cef8309586d00b1bb629f7
SHA1:
822d2bc83012273c7db705d1b5ff34ec410177ad
SHA256:
B0965826CC14BB0C7DEA0184E8D24BEE1DFDD5614911F8BCDF61C671B0DC961B
File Size:
2.65 MB, 2650064 bytes
|
|
MD5:
43ec49ae47f5b7986693b8b1d6b0c647
SHA1:
6777c95eb5674d319688ce0829353536d800f540
SHA256:
A286D5C14C3F7DCF71A7EDDA522925168EDEC38965A655A74FD62C4BDAEFB062
File Size:
2.79 MB, 2788806 bytes
|
|
MD5:
2d610497dba16a2d8d57d199105b172f
SHA1:
66c23281138bfd23fa10ca7e273cd211996388aa
SHA256:
E47D662C2F90235CA8435D9D531E2D5F280091193D763A02E958D69F402C6DC0
File Size:
2.86 MB, 2862220 bytes
|
|
MD5:
e667f3049898ff618cea3970239c7ec4
SHA1:
0c78d7d344ae2f84e6bc604addb6b634d51e36fb
SHA256:
D42D524F6F3A7DD059C8199D32541689F914B0BAD7B378C313DD7DEDEC0A877A
File Size:
2.52 MB, 2521184 bytes
|
Windows Portable Executable Attributes
- File doesn't have "Rich" header
- File doesn't have debug information
- File doesn't have exports table
- File doesn't have relocations information
- File doesn't have security information
- File has exports table
- File has TLS information
- File is 32-bit executable
- File is either console or GUI application
- File is GUI application (IMAGE_SUBSYSTEM_WINDOWS_GUI)
Show More
- File is Native application (NOT .NET application)
- File is not packed
- IMAGE_FILE_DLL is not set inside PE header (Executable)
- IMAGE_FILE_EXECUTABLE_IMAGE is set inside PE header (Executable Image)
File Icons
File Icons
This section displays icon resources found within family samples. Malware often replicates icons commonly associated with legitimate software to mislead users into believing the malware is safe.Windows PE Version Information
Windows PE Version Information
This section displays values and attributes that have been set in the Windows file version information data structure for samples within this family. To mislead users, malware actors often add fake version information mimicking legitimate software.| Name | Value |
|---|---|
| Comments | This installation was built with Inno Setup. |
| File Description |
|
| File Version |
|
| Internal Name | TJprojMain |
| Original Filename | TJprojMain.exe |
| Product Name |
|
| Product Version |
|
Digital Signatures
Digital Signatures
This section lists digital signatures that are attached to samples within this family. When analyzing and verifying digital signatures, it is important to confirm that the signature’s root authority is a well-known and trustworthy entity and that the status of the signature is good. Malware is often signed with non-trustworthy “Self Signed” digital signatures (which can be easily created by a malware author with no verification). Malware may also be signed by legitimate signatures that have an invalid status, and by signatures from questionable root authorities with fake or misleading “Signer” names.| Signer | Root | Status |
|---|---|---|
| INNOVA MEDIA internetne storitve d.o.o. | GlobalSign GCC R45 EV CodeSigning CA 2020 | Self Signed |
Block Information
Block Information
During analysis, EnigmaSoft breaks file samples into logical blocks for classification and comparison with other samples. Blocks can be used to generate malware detection rules and to group file samples into families based on shared source code, functionality and other distinguishing attributes and characteristics. This section lists a summary of this block data, as well as its classification by EnigmaSoft. A visual representation of the block data is also displayed, where available.Similar Families
Similar Families
This section lists other families that share similarities with this family, based on EnigmaSoft’s analysis. Many malware families are created from the same malware toolkits and use the same packing and encryption techniques but uniquely extend functionality. Similar families may also share source code, attributes, icons, subcomponents, compromised and/or invalid digital signatures, and network characteristics. Researchers leverage these similarities to rapidly and effectively triage file samples and extend malware detection rules.- Agent.FDD
- Banker.LH
- Banker.R
- Injector.AK
- Lumma.GFD
Show More
- Ousaban.V
- Rugmi.IA
- Sheloader.A
- Stealer.KF
Files Modified
Files Modified
This section lists files that were created, modified, moved and/or deleted by samples in this family. File system activity can provide valuable insight into how malware functions on the operating system.| File | Attributes |
|---|---|
| c:\users\user\appdata\local\temp\is-3r2bb.tmp\ccb27432fffa81a33362b18a54ec1e013e3e5f94_0005857136.tmp | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\is-4d0s7.tmp\db35277f19b7b2617d53115a8b88ddaaa984cfc4_0002650192.tmp | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\is-d6550.tmp\6ed2e5c191982cb7c7ad6e311ae61bd7443f7d2e_0002650336.tmp | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\is-eiahq.tmp\822d2bc83012273c7db705d1b5ff34ec410177ad_0002650064.tmp | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\is-f4ita.tmp\a07cabab8ebd504ce01f4d8c005f69d9e3b1c27c_0005857088.tmp | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\is-jeveo.tmp\2a4e951fe85118df7231dd447baaa4e7c4c7f9d5_0002650440.tmp | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\is-n43dc.tmp\91f01a266f5064e743180e1f57c5547519381e08_0002650264.tmp | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\is-q6nga.tmp\0c78d7d344ae2f84e6bc604addb6b634d51e36fb_0002521184.tmp | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\is-ski9f.tmp\8ccdb4a8cd8682cc026dada2980beb575a1b0226_0005857088.tmp | Generic Write,Read Attributes |
Windows API Usage
Windows API Usage
This section lists Windows API calls that are used by the samples in this family. Windows API usage analysis is a valuable tool that can help identify malicious activity, such as keylogging, security privilege escalation, data encryption, data exfiltration, interference with antivirus software, and network request manipulation.| Category | API |
|---|---|
| User Data Access |
|
| Process Shell Execute |
|
| Process Manipulation Evasion |
|
| Other Suspicious |
|
Shell Command Execution
Shell Command Execution
This section lists Windows shell commands that are run by the samples in this family. Windows Shell commands are often leveraged by malware for nefarious purposes and can be used to elevate security privileges, download and launch other malware, exploit vulnerabilities, collect and exfiltrate data, and hide malicious activity.
"C:\Users\Ygnyfxct\AppData\Local\Temp\is-F4ITA.tmp\a07cabab8ebd504ce01f4d8c005f69d9e3b1c27c_0005857088.tmp" /SL5="$5005E,4807120,845824,c:\users\user\downloads\a07cabab8ebd504ce01f4d8c005f69d9e3b1c27c_0005857088"
|
"C:\Users\Vejodllr\AppData\Local\Temp\is-N43DC.tmp\91f01a266f5064e743180e1f57c5547519381e08_0002650264.tmp" /SL5="$1025C,1598636,845824,c:\users\user\downloads\91f01a266f5064e743180e1f57c5547519381e08_0002650264"
|
"C:\Users\Xqbuogfc\AppData\Local\Temp\is-3R2BB.tmp\ccb27432fffa81a33362b18a54ec1e013e3e5f94_0005857136.tmp" /SL5="$30142,4807120,845824,c:\users\user\downloads\ccb27432fffa81a33362b18a54ec1e013e3e5f94_0005857136"
|
"C:\Users\Mrenzbdr\AppData\Local\Temp\is-D6550.tmp\6ed2e5c191982cb7c7ad6e311ae61bd7443f7d2e_0002650336.tmp" /SL5="$3013E,1598636,845824,c:\users\user\downloads\6ed2e5c191982cb7c7ad6e311ae61bd7443f7d2e_0002650336"
|
"C:\Users\Hjelfugl\AppData\Local\Temp\is-SKI9F.tmp\8ccdb4a8cd8682cc026dada2980beb575a1b0226_0005857088.tmp" /SL5="$60052,4807120,845824,c:\users\user\downloads\8ccdb4a8cd8682cc026dada2980beb575a1b0226_0005857088"
|
Show More
"C:\Users\Bzwuslgb\AppData\Local\Temp\is-JEVEO.tmp\2a4e951fe85118df7231dd447baaa4e7c4c7f9d5_0002650440.tmp" /SL5="$1D07D2,1598767,845824,c:\users\user\downloads\2a4e951fe85118df7231dd447baaa4e7c4c7f9d5_0002650440"
|
"C:\Users\Githwazy\AppData\Local\Temp\is-4D0S7.tmp\db35277f19b7b2617d53115a8b88ddaaa984cfc4_0002650192.tmp" /SL5="$22028A,1598543,845824,c:\users\user\downloads\db35277f19b7b2617d53115a8b88ddaaa984cfc4_0002650192"
|
"C:\Users\Wimrlkpo\AppData\Local\Temp\is-EIAHQ.tmp\822d2bc83012273c7db705d1b5ff34ec410177ad_0002650064.tmp" /SL5="$3032A,1598543,845824,c:\users\user\downloads\822d2bc83012273c7db705d1b5ff34ec410177ad_0002650064"
|
"C:\Users\Okdqdhwl\AppData\Local\Temp\is-Q6NGA.tmp\0c78d7d344ae2f84e6bc604addb6b634d51e36fb_0002521184.tmp" /SL5="$6017C,1584344,832512,c:\users\user\downloads\0c78d7d344ae2f84e6bc604addb6b634d51e36fb_0002521184"
|