PUP.2345.com
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Popularity Rank: | 2,005 |
| Threat Level: | 10 % (Normal) |
| Infected Computers: | 122,998 |
| First Seen: | July 13, 2015 |
| Last Seen: | January 31, 2026 |
| OS(es) Affected: | Windows |
Table of Contents
SpyHunter Detects & Remove PUP.2345.com
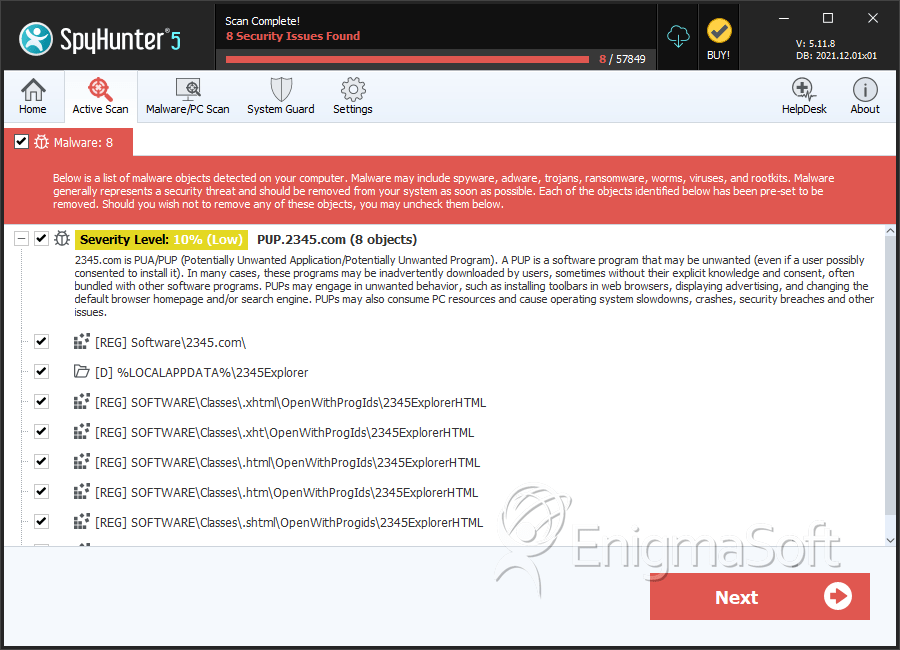
Registry Details
Directories
PUP.2345.com may create the following directory or directories:
| %APPDATA%\2345Explorer |
| %APPDATA%\2345Pic |
| %APPDATA%\Shield_2345Explorer |
| %LOCALAPPDATA%\2345Explorer |
| %PROGRAMFILES%\2345Soft\2345Explorer |
| %PROGRAMFILES%\2345Soft\2345Pic |
| %PROGRAMFILES(x86)%\2345Soft\2345Explorer |
| %PROGRAMFILES(x86)%\2345Soft\2345Pic |
| %TEMP%\2345Explorer |
| %appdata%\softmgr_2345 |
Analysis Report
General information
| Family Name: | PUP.2345.com |
|---|---|
| Signature status: | Modified signature |
Known Samples
Known Samples
This section lists other file samples believed to be associated with this family.|
MD5:
8bbc9928aa2e6bcc3fbcbc1a445fa0d7
SHA1:
d226a5ea3aa41c628cff31297b7b60a1175f2797
File Size:
2.53 MB, 2530072 bytes
|
|
MD5:
f2d1d09971f8fad5922d5de4c7567332
SHA1:
941f2ef8ae5ea83d0faacaa77f72db02eb7b0b31
File Size:
5.26 MB, 5264680 bytes
|
|
MD5:
473a984cd9306bf095ac67cc7fab375b
SHA1:
6a77f3fd80f2b465636bb74aeb1c0687a966bd02
SHA256:
7348543EE8299A5C09B455B0C30232332F641792738A863E7BAB70C9640C255E
File Size:
4.55 MB, 4552896 bytes
|
|
MD5:
da97896ce72ad9e8d327d2c2a8f4f3b5
SHA1:
4c684e5c848233b0deb2de0dd33b891955f2d330
SHA256:
74FB5F6D3B30FF33077B6A6D92FF6F873C2ECDFDDA163A27EED75365003CE023
File Size:
1.14 MB, 1142488 bytes
|
|
MD5:
8e7871ad233b88745ada7a1763c1c581
SHA1:
81762b51fb2676f6b53d69e0c5b0d744fb4575df
SHA256:
3BD4EB43419FF7B65B9F28351D3357E0033EBE229EC629056A9AD7777AA897CD
File Size:
210.62 KB, 210616 bytes
|
Show More
|
MD5:
7ff366f5f7982e21084d085df2650d6b
SHA1:
f1e4015789afa7b457d3f6e757113b2da8718fe0
SHA256:
CE47AA057441008315AFD445F9BD355CD943A8BD602EB8952912590C33B3ECB5
File Size:
5.26 MB, 5264568 bytes
|
|
MD5:
5e61087e84607131582313cbbd3853ec
SHA1:
131a278d8a1e276e654f1a53ddebaae6e0396ac1
SHA256:
D8DBD1E1ED43614C2336A23D1CD39AC78511CBD8406516EA01DC2475702CD844
File Size:
4.13 MB, 4132568 bytes
|
|
MD5:
48f468f8a2531e997ab50e9c2834ad39
SHA1:
f96f13b3f4e592cd3b7e046f64bbd3c6fc3ccc48
SHA256:
F91F89B463074E028B8D0F851A24DF6DDF5EC5971418423073E09C3CB8C5D0C1
File Size:
2.96 MB, 2957624 bytes
|
|
MD5:
5e9792de539a74f1f2b99c14411676ca
SHA1:
4e54a50e80ef48a515a43c5467da73c21208c4a9
SHA256:
82F76D0C8A1C02CDD011E5A09453C59C35FBD878D742950D159BC41E3ED26113
File Size:
2.53 MB, 2530200 bytes
|
|
MD5:
38dab1f94d4de2bf0d461cee5f0adf44
SHA1:
a88be403dbe227cdd99a84c0945565687a369596
SHA256:
092E1E86171486724DC034344B28FD99FE9CEFAD5B8FECE9A381B16A4B060354
File Size:
1.19 MB, 1190296 bytes
|
|
MD5:
6c1956c5256732581acc4c68301910a0
SHA1:
5800ba5410db37b0497d948fcb946bbc9abac497
SHA256:
98A2C2B1C245DC3F0484225289211F4BFFCD91FF27B87F78C4B37A2947967BCC
File Size:
210.74 KB, 210736 bytes
|
|
MD5:
876dfb723199b071b11f333cc51b5f5a
SHA1:
1d1cb51e2a334cd74a02d94d2adc76051ece7149
SHA256:
4E5A6D9F8AC7FEBFC949F4669DF4D51C6461068BDA26841B4A4E240D087AADC1
File Size:
2.53 MB, 2530200 bytes
|
|
MD5:
9da400b213a462fa77ed0694a9db8e40
SHA1:
4d7e6e710e7309f8c6c4f0c9c9c9dc6bc2424fe8
SHA256:
BC9865BEA3BF1BF4F8549C4D6FC4B87EB7FF9F5CBEA4742789AE47D4F45A43A9
File Size:
1.97 MB, 1966080 bytes
|
|
MD5:
f819428ce3071815353b6327e4c9c131
SHA1:
7886d54707f9402edd7b2826cdbe2f1f7196f577
SHA256:
A9A925943B2786B728561C7F57D6039A64FE6B07A6A2418C77ACF585D6AAC5BD
File Size:
1.19 MB, 1190296 bytes
|
|
MD5:
bf0514afc9743041b4e5cd11a75916f8
SHA1:
89a7bb0649f37563454ec941d9bf6b9c9a97b035
SHA256:
4851687900F8A94FA161106E53EA72064FEBE2363FF4D2D51BDC548B9CC88A24
File Size:
2.53 MB, 2530200 bytes
|
Windows Portable Executable Attributes
- File doesn't have "Rich" header
- File doesn't have debug information
- File doesn't have exports table
- File doesn't have relocations information
- File doesn't have security information
- File has exports table
- File has TLS information
- File is 32-bit executable
- File is console application (IMAGE_SUBSYSTEM_WINDOWS_CUI)
- File is either console or GUI application
Show More
- File is GUI application (IMAGE_SUBSYSTEM_WINDOWS_GUI)
- File is Native application (NOT .NET application)
- File is not packed
- IMAGE_FILE_DLL is not set inside PE header (Executable)
- IMAGE_FILE_EXECUTABLE_IMAGE is set inside PE header (Executable Image)
File Icons
File Icons
This section displays icon resources found within family samples. Malware often replicates icons commonly associated with legitimate software to mislead users into believing the malware is safe.Windows PE Version Information
Windows PE Version Information
This section displays values and attributes that have been set in the Windows file version information data structure for samples within this family. To mislead users, malware actors often add fake version information mimicking legitimate software.| Name | Value |
|---|---|
| Comments |
|
| Company Name |
|
| File Description |
|
| File Version |
Show More
|
| Internal Name |
|
| Legal Copyright |
|
| Original Filename |
|
| Private Build |
|
| Product Name |
|
| Product Version |
Show More
|
| Special Build |
|
Digital Signatures
Digital Signatures
This section lists digital signatures that are attached to samples within this family. When analyzing and verifying digital signatures, it is important to confirm that the signature’s root authority is a well-known and trustworthy entity and that the status of the signature is good. Malware is often signed with non-trustworthy “Self Signed” digital signatures (which can be easily created by a malware author with no verification). Malware may also be signed by legitimate signatures that have an invalid status, and by signatures from questionable root authorities with fake or misleading “Signer” names.| Signer | Root | Status |
|---|---|---|
| Shanghai 2345 Mobile Technology Co., Ltd. | DigiCert Trusted G4 Code Signing RSA4096 SHA384 2021 CA1 | Self Signed |
| Shanghai 2345 Mobile Technology Co., Ltd. | DigiCert Trusted Root G4 | Root Not Trusted |
Block Information
Block Information
During analysis, EnigmaSoft breaks file samples into logical blocks for classification and comparison with other samples. Blocks can be used to generate malware detection rules and to group file samples into families based on shared source code, functionality and other distinguishing attributes and characteristics. This section lists a summary of this block data, as well as its classification by EnigmaSoft. A visual representation of the block data is also displayed, where available.| Total Blocks: | 7,083 |
|---|---|
| Potentially Malicious Blocks: | 187 |
| Whitelisted Blocks: | 3,794 |
| Unknown Blocks: | 3,102 |
Visual Map
? - Unknown Block
x - Potentially Malicious Block
Files Modified
Files Modified
This section lists files that were created, modified, moved and/or deleted by samples in this family. File system activity can provide valuable insight into how malware functions on the operating system.| File | Attributes |
|---|---|
| c:\users\user\appdata\local\temp\nse3909.tmp\fileinfo.dll | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\nse3909.tmp\rcwidgetpluginuninstall.dll | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\nsi37ee.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete |
| c:\users\user\appdata\local\temp\nso38f8.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete |
| c:\users\user\appdata\local\temp\~nsua.tmp\un_a.exe | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete,LEFT 262144 |
| c:\users\user\appdata\local\temp\~nsua.tmp\un_a.exe.p | Generic Write,Read Attributes |
Registry Modifications
Registry Modifications
This section lists registry keys and values that were created, modified and/or deleted by samples in this family. Windows Registry activity can provide valuable insight into malware functionality. Additionally, malware often creates registry values to allow itself to automatically start and indefinitely persist after an initial infection has compromised the system.| Key::Value | Data | API Name |
|---|---|---|
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Users\Lgbqyhzy\AppData\Local\Temp\~nsuA.tmp\Un_A.exe | RegNtPreCreateKey |
| HKCU\local settings\software\microsoft\windows\shell\muicache::c:\users\lgbqyhzy\appdata\local\temp\~nsua.tmp\un_a.exe | 好压万能压缩 v1.1 安装程序 | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Users\Lgbqyhzy\AppData\Local\Temp\~nsuA.tmp\Un_A.exe��\??\C:\Users\Lgbqyhzy\AppData\Local\Temp\~nsuA.tmp\Un_A.exe.p | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Users\Lgbqyhzy\AppData\Local\Temp\~nsuA.tmp\Un_A.exe��\??\C:\Users\Lgbqyhzy\AppData\Local\Temp\~nsuA.tmp\Un_A.exe.p��\??\ | RegNtPreCreateKey |
Windows API Usage
Windows API Usage
This section lists Windows API calls that are used by the samples in this family. Windows API usage analysis is a valuable tool that can help identify malicious activity, such as keylogging, security privilege escalation, data encryption, data exfiltration, interference with antivirus software, and network request manipulation.| Category | API |
|---|---|
| Service Control |
|
| Network Wininet |
|
| Anti Debug |
|
| Network Winhttp |
|
| Syscall Use |
Show More
|
| Process Shell Execute |
|
| User Data Access |
|
| Process Manipulation Evasion |
|
Shell Command Execution
Shell Command Execution
This section lists Windows shell commands that are run by the samples in this family. Windows Shell commands are often leveraged by malware for nefarious purposes and can be used to elevate security privileges, download and launch other malware, exploit vulnerabilities, collect and exfiltrate data, and hide malicious activity.
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\6a77f3fd80f2b465636bb74aeb1c0687a966bd02_0004552896.,LiQMAxHB
|
"C:\Users\Lgbqyhzy\AppData\Local\Temp\~nsuA.tmp\Un_A.exe" _?=c:\users\user\downloads\
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\f96f13b3f4e592cd3b7e046f64bbd3c6fc3ccc48_0002957624.,LiQMAxHB
|
