TROJ_ZBOT.BXW
Cartão de pontuação de ameaças
EnigmaSoft Threat Scorecard
Os EnigmaSoft Threat Scorecards são relatórios de avaliação para diferentes ameaças de malware que foram coletadas e analisadas por nossa equipe de pesquisa. Os Scorecards de Ameaças da EnigmaSoft avaliam e classificam as ameaças usando várias métricas, incluindo fatores de risco reais e potenciais, tendências, frequência, prevalência e persistência. Os Scorecards de Ameaças da EnigmaSoft são atualizados regularmente com base em nossos dados e métricas de pesquisa e são úteis para uma ampla gama de usuários de computador, desde usuários finais que buscam soluções para remover malware de seus sistemas até especialistas em segurança que analisam ameaças.
Os Scorecards de Ameaças da EnigmaSoft exibem uma variedade de informações úteis, incluindo:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Nível de gravidade: O nível de gravidade determinado de um objeto, representado numericamente, com base em nosso processo de modelagem de risco e pesquisa, conforme explicado em nossos Critérios de Avaliação de Ameaças .
Computadores infectados: O número de casos confirmados e suspeitos de uma determinada ameaça detectada em computadores infectados conforme relatado pelo SpyHunter.
Consulte também Critérios de Avaliação de Ameaças .
| Popularity Rank: | 9,171 |
| Nível da Ameaça: | 80 % (Alto) |
| Computadores infectados: | 2,282 |
| Visto pela Primeira Vez: | July 24, 2009 |
| Visto pela Última Vez: | January 20, 2026 |
| SO (s) Afetados: | Windows |
O TROJ_ZBOT.BXW é um Trojan que usa um arquivo .lnk mal-intencionado, como técnica de inicialização. O arquivo .lnk é capaz de explorar uma vulnerabilidade do Windows. O TROJ_ZBOT.BXW se espalha via e-mails de spam, contendo arquivos .zip prejudiciais anexados. O TROJ_ZBOT.BXW coloca os detalhes de bancos online da vítima (por exemplo, senhas, nomes de usuários, etc..) sob o risco de serem roubados. O TROJ_ZBOT.BXW é um risco para a privacidade, que deve ser levado muito a serio.
Índice
Outros Nomes
15 fornecedores de segurança sinalizaram este arquivo como malicioso.
| Antivirus Vendor | Detecção |
|---|---|
| AVG | Generic7_c.BULS |
| Fortinet | W32/Bublik.AKIQ!tr |
| Ikarus | Backdoor.Win32.DarkKomet |
| AhnLab-V3 | Trojan/Win32.Jorik |
| McAfee-GW-Edition | Heuristic.BehavesLike.Win32.Suspicious-BAY.S |
| AntiVir | TR/Rogue.8877826.1 |
| Kaspersky | Trojan.Win32.Bublik.akiq |
| Avast | AutoIt:MalOb-J [Trj] |
| McAfee | Artemis!1C946EE5948C |
| AVG | Generic32.CDAA |
| Ikarus | Trojan.Win32.Spy2 |
| Kaspersky | Trojan-Dropper.Win32.Agent.hjwv |
| Fortinet | W32/Jorik_Zbot.PLC!tr |
| McAfee-GW-Edition | Heuristic.BehavesLike.Win32.ModifiedUPX.C |
| AntiVir | TR/Symmi.18703.2 |
SpyHunter detecta e remove TROJ_ZBOT.BXW
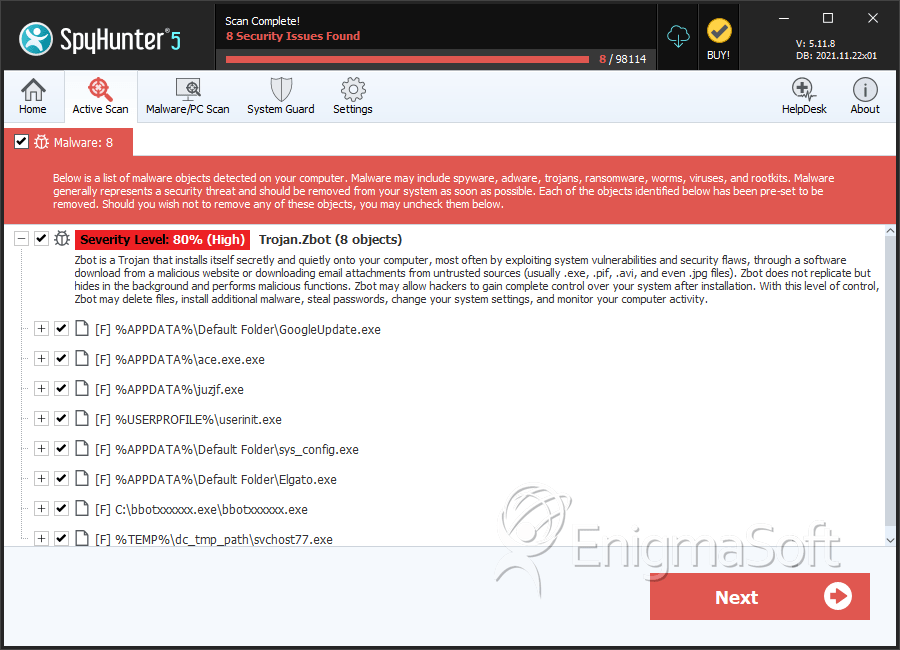
Detalhes Sobre os Arquivos do Sistema
| # | Nome do arquivo | MD5 |
Detecções
Detecções: O número de casos confirmados e suspeitos de uma determinada ameaça detectada nos computadores infectados conforme relatado pelo SpyHunter.
|
|---|---|---|---|
| 1. | GoogleUpdate.exe | de75d9858dd25f83ee666c4890367023 | 157 |
| 2. | ace.exe.exe | 2af6923df61c3800fb4957cd5163646d | 118 |
| 3. | sys_config.exe | 2c770a08cf50a31e138aa505c81a8cb4 | 40 |
| 4. | Elgato.exe | d9a57b7f55011099f22eac398f8683a3 | 20 |
| 5. | bbotxxxxxx.exe | 02d7b03f126ced200af04cafffbf4f66 | 18 |
| 6. | svchost77.exe | 4063dc3346591414467dea192e4de47d | 17 |
| 7. | server.exe | 1c946ee5948c6d23847688c7d5fb8ebd | 15 |
| 8. | Default File.exe | ce9a0cdd7f5f3a46c13e8001db1fc4b4 | 14 |
| 9. | Defcon.exe | 02dbd6164feb882e0c5fbd546ded3781 | 13 |
| 10. | wgsdgsdgdsgsd.exe | d4c60f32496ae92c5a53bda45d28937d | 9 |
| 11. | crss.exe | 733032ca6f13e38740fc4416eee0a0d4 | 9 |
| 12. | svchost.exe | 472732bcf7067db19136591db7694678 | 8 |
| 13. | _ex-08.exe | 4d9a644bb19c3d1fd158aed7830a457e | 7 |
| 14. | oshdo.dll | 267433320dc37f9369aef2aeaae68499 | 5 |
| 15. | 0.0863059484879578.exe | b3f35490864b39475bd5d8e9a12a0f08 | 3 |
| 16. | Recycle.Bin.exe | 5ed168874559f43720d9a79b20c89d9f | 3 |
| 17. | B6232F3A6E7.exe | 96cb97d9c4f61ab61cfad5a60606f242 | 3 |
| 18. | 0.2778958902928622.exe | f4f2bd07bfaf360b2ba596d134df76e3 | 2 |
| 19. | auaucdlve.exe | cab45be12136d15f2958b1ca575131b4 | 2 |
| 20. | ntos.exe | 9893493ec0578ac0194366a4e027e829 | 2 |
| 21. | MaelXpers.exe | a69349baf03c5a5f8dac25232ae55a8d | 2 |
| 22. | 9E787BEFEC0.exe | c0397b8114fb367b3ea3d1a9d5bde409 | 1 |
| 23. | dcratnewfud.exe | e7fad45a14545e19debf752ebb4c7510 | 1 |
| 24. | {14003D43-1705-1636-2800-333714001D1F}.exe | 604fdaa1fd4e335f26032fd416a5461b | 1 |
| 25. | apijcajxv.exe | 70383d5dd9b91c425b0107cf1e6c7b55 | 1 |
| 26. | dwtray.exe | aa872cb97a821e7736ba479558acfe78 | 1 |
| 27. | shortcuts.exe | 5cb5a2617939cc2428f4f24b9f56421f | 1 |
| 28. | file.exe | 0efa791652688dba9b98a058f34f3fc8 | 1 |
Detalhes sobre o Registro
URLs
TROJ_ZBOT.BXW pode chamar os seguintes URLs:
| 2sdfhs8d7fsh34d8f7s.org |
| 51qn.net |
| av4321.us |
| batmu.cn |
| clicksurfcash.net |
| crisis1s.com |
| fordearfriends.com |
| hotdomainworld.info |
| kakajz.cn |
| lilj.us |
| sfqjsf.cn |
| skp360.com |
Relatório de análise
Informação geral
| Family Name: | Trojan.Zbot |
|---|---|
| Signature status: | Self Signed |
Known Samples
Known Samples
This section lists other file samples believed to be associated with this family.|
MD5:
124371998fe68456f2512121f9cd8f6e
SHA1:
598d02f8fe185c0372190306f2f17d6fb478e38f
SHA256:
F6A9C65B034CDABB55EA3BF7AEBD116EA913FD56CB32BB4AA85C902578DFD1BA
Tamanho do Arquivo:
2.21 MB, 2207752 bytes
|
Windows Portable Executable Attributes
- File doesn't have "Rich" header
- File doesn't have exports table
- File has TLS information
- File is 32-bit executable
- File is either console or GUI application
- File is GUI application (IMAGE_SUBSYSTEM_WINDOWS_GUI)
- File is Native application (NOT .NET application)
- File is not packed
- IMAGE_FILE_DLL is not set inside PE header (Executable)
- IMAGE_FILE_EXECUTABLE_IMAGE is set inside PE header (Executable Image)
File Icons
File Icons
This section displays icon resources found within family samples. Malware often replicates icons commonly associated with legitimate software to mislead users into believing the malware is safe.Windows PE Version Information
Windows PE Version Information
This section displays values and attributes that have been set in the Windows file version information data structure for samples within this family. To mislead users, malware actors often add fake version information mimicking legitimate software.| Nome | Valor |
|---|---|
| File Description | Option MFC 응용 프로그램 |
| File Version | 1, 0, 0, 1 |
| Internal Name | Option |
| Legal Copyright | Copyright (C) 2002 |
| Original Filename | Option.EXE |
| Product Name | Option 응용 프로그램 |
| Product Version | 1, 0, 0, 1 |
Digital Signatures
Digital Signatures
This section lists digital signatures that are attached to samples within this family. When analyzing and verifying digital signatures, it is important to confirm that the signature’s root authority is a well-known and trustworthy entity and that the status of the signature is good. Malware is often signed with non-trustworthy “Self Signed” digital signatures (which can be easily created by a malware author with no verification). Malware may also be signed by legitimate signatures that have an invalid status, and by signatures from questionable root authorities with fake or misleading “Signer” names.| Signer | Root | Status |
|---|---|---|
| Game Cafe Services Inc | SSL.com Code Signing Intermediate CA ECC R2 | Self Signed |
File Traits
- x86
Block Information
Block Information
During analysis, EnigmaSoft breaks file samples into logical blocks for classification and comparison with other samples. Blocks can be used to generate malware detection rules and to group file samples into families based on shared source code, functionality and other distinguishing attributes and characteristics. This section lists a summary of this block data, as well as its classification by EnigmaSoft. A visual representation of the block data is also displayed, where available.| Total Blocks: | 8,439 |
|---|---|
| Potentially Malicious Blocks: | 2 |
| Whitelisted Blocks: | 8,402 |
| Unknown Blocks: | 35 |
Visual Map
? - Unknown Block
x - Potentially Malicious Block
Similar Families
Similar Families
This section lists other families that share similarities with this family, based on EnigmaSoft’s analysis. Many malware families are created from the same malware toolkits and use the same packing and encryption techniques but uniquely extend functionality. Similar families may also share source code, attributes, icons, subcomponents, compromised and/or invalid digital signatures, and network characteristics. Researchers leverage these similarities to rapidly and effectively triage file samples and extend malware detection rules.- Agent.AIBB
- Farfli.ZA
- Marte.L
- Rugmi.GA
- Spy.Agent.XD
Show More
- YoutubeDownloaderGuru.B
Windows API Usage
Windows API Usage
This section lists Windows API calls that are used by the samples in this family. Windows API usage analysis is a valuable tool that can help identify malicious activity, such as keylogging, security privilege escalation, data encryption, data exfiltration, interference with antivirus software, and network request manipulation.| Category | API |
|---|---|
| Anti Debug |
|
| User Data Access |
|
| Other Suspicious |
|
