Conficker
Cartão de pontuação de ameaças
EnigmaSoft Threat Scorecard
Os EnigmaSoft Threat Scorecards são relatórios de avaliação para diferentes ameaças de malware que foram coletadas e analisadas por nossa equipe de pesquisa. Os Scorecards de Ameaças da EnigmaSoft avaliam e classificam as ameaças usando várias métricas, incluindo fatores de risco reais e potenciais, tendências, frequência, prevalência e persistência. Os Scorecards de Ameaças da EnigmaSoft são atualizados regularmente com base em nossos dados e métricas de pesquisa e são úteis para uma ampla gama de usuários de computador, desde usuários finais que buscam soluções para remover malware de seus sistemas até especialistas em segurança que analisam ameaças.
Os Scorecards de Ameaças da EnigmaSoft exibem uma variedade de informações úteis, incluindo:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Nível de gravidade: O nível de gravidade determinado de um objeto, representado numericamente, com base em nosso processo de modelagem de risco e pesquisa, conforme explicado em nossos Critérios de Avaliação de Ameaças .
Computadores infectados: O número de casos confirmados e suspeitos de uma determinada ameaça detectada em computadores infectados conforme relatado pelo SpyHunter.
Consulte também Critérios de Avaliação de Ameaças .
| Popularity Rank: | 14,934 |
| Nível da Ameaça: | 90 % (Alto) |
| Computadores infectados: | 49 |
| Visto pela Primeira Vez: | July 24, 2009 |
| Visto pela Última Vez: | September 24, 2025 |
| SO (s) Afetados: | Windows |
O Conficker, também conhecido como W32/Conficker.worm, Win32/Conficker.A, W32.Downadup, Downadup e Kido, é um worm que explora as falhas que existem na vulnerabilidade MS08-067 do Windows. Quando o Conficker infecta o seu PC, ele pode impedi-lo de acessar sites de segurança e desativa certos serviços do sistema do Windows, tais como o Windows Security Center, o Error Reporting e o Windows Defender. O perigo do Conficker é sua capacidade de se espalhar para outros computadores vulneráveis, através de redes compartilhadas. Se um computador da rede estiver infectado, então ele poderá se espalhar para os outros computadores nessa rede. A Microsoft lançou uma correção para essa vulnerabilidade do Windows.
É imprescindível que você baixe a última correção liberada pela Atualizações do Windows da Microsoft. Além disso, como o Conficker usa nomes de arquivo aleatórios, para impedir ser fácilmente detectado, o melhor é usar um software anti-vírus ou anti-spyware, que vai permitir que você escaneie todo o seu computador, em vez de tentar apagar manualmente os arquivos do Conficker.
Índice
SpyHunter detecta e remove Conficker
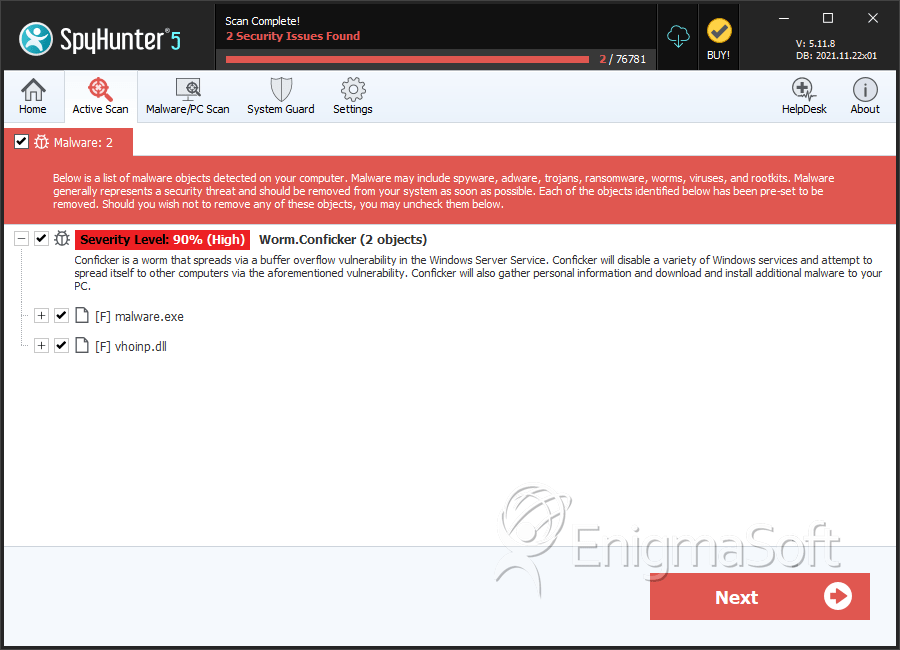
Detalhes Sobre os Arquivos do Sistema
| # | Nome do arquivo | MD5 |
Detecções
Detecções: O número de casos confirmados e suspeitos de uma determinada ameaça detectada nos computadores infectados conforme relatado pelo SpyHunter.
|
|---|---|---|---|
| 1. | malware.exe | 09edf06953b56ee6a8cb6823cb3b2996 | 0 |
| 2. | vhoinp.dll | e80c7cb77020f9326e15b3a0fb298045 | 0 |
Relatório de análise
Informação geral
| Family Name: | Worm.Conficker |
|---|---|
| Signature status: | No Signature |
Known Samples
Known Samples
This section lists other file samples believed to be associated with this family.|
MD5:
2c2c5fdcfd368151b6c0e090c53aa300
SHA1:
8c981285d9caa0c5d6285b980377e4721f26e7a0
SHA256:
66BEE08996C38F985AE00BA02DDB0BDDB4A3ADC062334B90D0E6F9DC1ECBB337
Tamanho do Arquivo:
2.09 MB, 2093056 bytes
|
Windows Portable Executable Attributes
- File doesn't have "Rich" header
- File doesn't have debug information
- File doesn't have security information
- File has exports table
- File is 32-bit executable
- File is either console or GUI application
- File is GUI application (IMAGE_SUBSYSTEM_WINDOWS_GUI)
- File is Native application (NOT .NET application)
- File is not packed
- IMAGE_FILE_DLL is not set inside PE header (Executable)
Show More
- IMAGE_FILE_EXECUTABLE_IMAGE is set inside PE header (Executable Image)
Windows PE Version Information
Windows PE Version Information
This section displays values and attributes that have been set in the Windows file version information data structure for samples within this family. To mislead users, malware actors often add fake version information mimicking legitimate software.| Nome | Valor |
|---|---|
| Company Name | Itesoft |
| Compile Date | vendredi 28 janvier 2005 17:18 |
| File Description | Itesoft.FreeMind Component |
| File Version | 1.9.5.508 |
| Internal Name | FMEntity |
| Legal Copyright | Copyright © ITESOFT SA |
| Legal Trademarks | ITESOFT.FreeMind and ITESOFT.Invoices are registered trademarks of ITESOFT SA. |
| Original Filename | IT_FMEntity.dll |
| Product Name | Itesoft FreeMind |
| Product Version | 1.9 |
File Traits
- dll
- HighEntropy
- imgui
- VirtualQueryEx
- WriteProcessMemory
- x86
Block Information
Block Information
During analysis, EnigmaSoft breaks file samples into logical blocks for classification and comparison with other samples. Blocks can be used to generate malware detection rules and to group file samples into families based on shared source code, functionality and other distinguishing attributes and characteristics. This section lists a summary of this block data, as well as its classification by EnigmaSoft. A visual representation of the block data is also displayed, where available.| Total Blocks: | 7,335 |
|---|---|
| Potentially Malicious Blocks: | 184 |
| Whitelisted Blocks: | 5,837 |
| Unknown Blocks: | 1,314 |
Visual Map
? - Unknown Block
x - Potentially Malicious Block
Windows API Usage
Windows API Usage
This section lists Windows API calls that are used by the samples in this family. Windows API usage analysis is a valuable tool that can help identify malicious activity, such as keylogging, security privilege escalation, data encryption, data exfiltration, interference with antivirus software, and network request manipulation.| Category | API |
|---|---|
| Syscall Use |
Show More
|
| Process Shell Execute |
|
| Anti Debug |
|
Shell Command Execution
Shell Command Execution
This section lists Windows shell commands that are run by the samples in this family. Windows Shell commands are often leveraged by malware for nefarious purposes and can be used to elevate security privileges, download and launch other malware, exploit vulnerabilities, collect and exfiltrate data, and hide malicious activity.
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\8c981285d9caa0c5d6285b980377e4721f26e7a0_0002093056.,LiQMAxHB
|