PC Protector Plus
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Popularity Rank: | 14,443 |
| Threat Level: | 10 % (Normal) |
| Infected Computers: | 1,875 |
| First Seen: | December 21, 2015 |
| Last Seen: | December 12, 2025 |
| OS(es) Affected: | Windows |
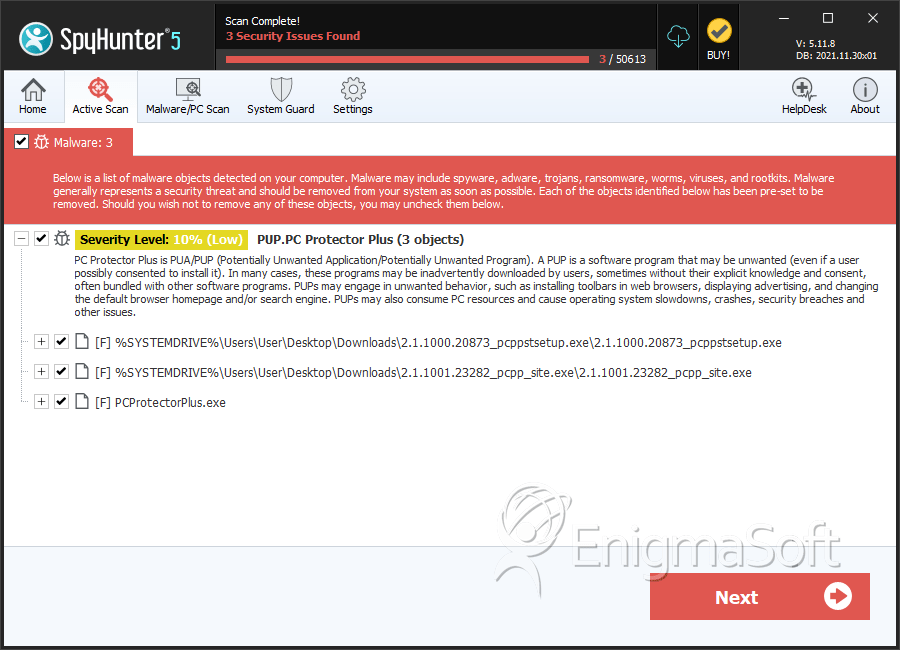
The PC Protector Plus anti-spyware tool by Jawego Partners LLC is advertised to provide a 360-degree protection against cyber threats. PC Protector Plus can be installed on all versions of Windows since Windows 7. The PC Protector Plus tool is available for free download on Pcprotectorplus.com and may arrive on your computer bundled with riskware like Shopping Helper Smartbar and TotalDatingGuide. You might want that the PC Protector Plus tool is perceived as a Potentially Unwanted Program (PUP) with adware capabilities that may collect data like your Internet history and bookmarks to create a unique advertising ID and show promotional materials in your default Internet browser.
The PC Protector Plus is supposed to be a protective layer for your system that is centered around your browser and checks for bad links and site reputation. You should note that the PC Protector Plus may uninstall your adblocker automatically. Moreover, the customer support on 844-944-0918 that is provided in the user interface of PC Protector Plus is associated with financial fraud related to governmental loans and lottery hoaxes. Security authorities report that the engine of the PC Protector Plus does not perform well and may detect safe programs to be hazardous as well as display fake detections to encourage users to subscribe to a premium plan. The premium version of PC Protector Plus is offered to users for $39.95, which is for the activation of all features of the engine inside PC Protector Plus. You will need to pay another $19.95 to benefit from 24/7 customer support that is associated with financial fraud.
Computer users are not advised to invest their money and trust in the PC Protector Plus program that may cause system errors and lacks advanced protection to halt modern cyber threats like Aldi Bot and Bladabindi. PC Protector Plus may show pop-up windows on your desktop to invite you to purchase its full version and other programs that run at the time. You can use a reputable anti-malware solution to delete the PC Protector Plus and avoid security problems that may stem from its activities.
Table of Contents
SpyHunter Detects & Remove PC Protector Plus
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | 2.1.1000.20873_pcppstsetup.exe | 0559f40e3a4f3dbfb1a9bfafb3e572f3 | 817 |
| 2. | 2.1.1001.23282_pcpp_site.exe | 7149ddedbff7ebb5f9b0e0105ccdef6c | 24 |
| 3. | PCProtectorPlus.exe | 89a53497848fea4ddb8532df604c6673 | 0 |
Analysis Report
General information
| Family Name: | PUP.PC Protector Plus |
|---|---|
| Signature status: | Self Signed |
Known Samples
Known Samples
This section lists other file samples believed to be associated with this family.|
MD5:
cb1d454b7dfaaa600b25d4b584925f37
SHA1:
fc97e1e9d728d8c286f2baf4bc87a49c0a57d48a
SHA256:
FEF0692621CA3F1617B79B7ECD8E8672980566C97344665274D9E04A6274792A
File Size:
4.04 MB, 4039384 bytes
|
|
MD5:
54bf1b06539e44264f71f933a82b8d55
SHA1:
6e2326054dd17e1319dce8b1ac3f3d2c8cc674f7
SHA256:
4AC5525F46153AACD841D0716D26B119034965C3B2AB00388B85C1B9901B7CC8
File Size:
157.62 KB, 157624 bytes
|
Windows Portable Executable Attributes
- File doesn't have "Rich" header
- File doesn't have debug information
- File doesn't have exports table
- File doesn't have relocations information
- File has exports table
- File has TLS information
- File is 32-bit executable
- File is either console or GUI application
- File is GUI application (IMAGE_SUBSYSTEM_WINDOWS_GUI)
- File is Native application (NOT .NET application)
Show More
- File is not packed
- IMAGE_FILE_DLL is not set inside PE header (Executable)
- IMAGE_FILE_EXECUTABLE_IMAGE is set inside PE header (Executable Image)
File Icons
File Icons
This section displays icon resources found within family samples. Malware often replicates icons commonly associated with legitimate software to mislead users into believing the malware is safe.Windows PE Version Information
Windows PE Version Information
This section displays values and attributes that have been set in the Windows file version information data structure for samples within this family. To mislead users, malware actors often add fake version information mimicking legitimate software.| Name | Value |
|---|---|
| Comments |
|
| Company Name |
|
| File Description |
|
| File Version |
|
| Internal Name | isxdl |
| Legal Copyright |
|
| Original Filename | isxdl.dll |
| Product Name |
|
| Product Version |
|
Digital Signatures
Digital Signatures
This section lists digital signatures that are attached to samples within this family. When analyzing and verifying digital signatures, it is important to confirm that the signature’s root authority is a well-known and trustworthy entity and that the status of the signature is good. Malware is often signed with non-trustworthy “Self Signed” digital signatures (which can be easily created by a malware author with no verification). Malware may also be signed by legitimate signatures that have an invalid status, and by signatures from questionable root authorities with fake or misleading “Signer” names.| Signer | Root | Status |
|---|---|---|
| WIN TUNEUP SOFTWARE LLP | Symantec Class 3 SHA256 Code Signing CA | Self Signed |
Block Information
Block Information
During analysis, EnigmaSoft breaks file samples into logical blocks for classification and comparison with other samples. Blocks can be used to generate malware detection rules and to group file samples into families based on shared source code, functionality and other distinguishing attributes and characteristics. This section lists a summary of this block data, as well as its classification by EnigmaSoft. A visual representation of the block data is also displayed, where available.| Total Blocks: | 620 |
|---|---|
| Potentially Malicious Blocks: | 40 |
| Whitelisted Blocks: | 580 |
| Unknown Blocks: | 0 |
Visual Map
? - Unknown Block
x - Potentially Malicious Block
Files Modified
Files Modified
This section lists files that were created, modified, moved and/or deleted by samples in this family. File system activity can provide valuable insight into how malware functions on the operating system.| File | Attributes |
|---|---|
| c:\users\user\appdata\local\temp\is-ksife.tmp\fc97e1e9d728d8c286f2baf4bc87a49c0a57d48a_0004039384.tmp | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\is-rf7uu.tmp\_isetup\_iscrypt.dll | Generic Read,Write Data,Write Attributes,Write extended,Append data |
| c:\users\user\appdata\local\temp\is-rf7uu.tmp\_isetup\_setup64.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data |
| c:\users\user\appdata\local\temp\is-rf7uu.tmp\_isetup\_shfoldr.dll | Generic Read,Write Data,Write Attributes,Write extended,Append data |
Registry Modifications
Registry Modifications
This section lists registry keys and values that were created, modified and/or deleted by samples in this family. Windows Registry activity can provide valuable insight into malware functionality. Additionally, malware often creates registry values to allow itself to automatically start and indefinitely persist after an initial infection has compromised the system.| Key::Value | Data | API Name |
|---|---|---|
| HKLM\software\classes\jscript:: | JScript Language | RegNtPreCreateKey |
| HKLM\software\classes\jscript\clsid:: | {f414c260-6ac0-11cf-b6d1-00aa00bbbb58} | RegNtPreCreateKey |
| HKLM\software\classes\livescript:: | JScript Language | RegNtPreCreateKey |
| HKLM\software\classes\livescript\clsid:: | {f414c260-6ac0-11cf-b6d1-00aa00bbbb58} | RegNtPreCreateKey |
| HKLM\software\classes\javascript:: | JScript Language | RegNtPreCreateKey |
| HKLM\software\classes\javascript\clsid:: | {f414c260-6ac0-11cf-b6d1-00aa00bbbb58} | RegNtPreCreateKey |
| HKLM\software\classes\javascript1.1:: | JScript Language | RegNtPreCreateKey |
| HKLM\software\classes\javascript1.1\clsid:: | {f414c260-6ac0-11cf-b6d1-00aa00bbbb58} | RegNtPreCreateKey |
| HKLM\software\classes\javascript1.2:: | JScript Language | RegNtPreCreateKey |
| HKLM\software\classes\javascript1.2\clsid:: | {f414c260-6ac0-11cf-b6d1-00aa00bbbb58} | RegNtPreCreateKey |
Show More
| HKLM\software\classes\javascript1.3:: | JScript Language | RegNtPreCreateKey |
| HKLM\software\classes\javascript1.3\clsid:: | {f414c260-6ac0-11cf-b6d1-00aa00bbbb58} | RegNtPreCreateKey |
| HKLM\software\classes\ecmascript:: | JScript Language | RegNtPreCreateKey |
| HKLM\software\classes\ecmascript\clsid:: | {f414c260-6ac0-11cf-b6d1-00aa00bbbb58} | RegNtPreCreateKey |
| HKLM\software\classes\wow6432node\clsid\{f414c260-6ac0-11cf-b6d1-00aa00bbbb58}:: | JScript Language | RegNtPreCreateKey |
| HKLM\software\classes\wow6432node\clsid\{f414c260-6ac0-11cf-b6d1-00aa00bbbb58}\progid:: | JScript | RegNtPreCreateKey |
| HKLM\software\classes\wow6432node\clsid\{f414c260-6ac0-11cf-b6d1-00aa00bbbb58}\inprocserver32:: | C:\WINDOWS\SysWow64\jscript.dll | RegNtPreCreateKey |
| HKLM\software\classes\wow6432node\clsid\{f414c260-6ac0-11cf-b6d1-00aa00bbbb58}\inprocserver32::threadingmodel | Both | RegNtPreCreateKey |
| HKLM\software\classes\jscript author:: | JScript Language Authoring | RegNtPreCreateKey |
| HKLM\software\classes\jscript author\clsid:: | {f414c261-6ac0-11cf-b6d1-00aa00bbbb58} | RegNtPreCreateKey |
| HKLM\software\classes\jscript.compact author:: | JScript Language Authoring | RegNtPreCreateKey |
| HKLM\software\classes\jscript.compact author\clsid:: | {f414c261-6ac0-11cf-b6d1-00aa00bbbb58} | RegNtPreCreateKey |
| HKLM\software\classes\livescript author:: | JScript Language Authoring | RegNtPreCreateKey |
| HKLM\software\classes\livescript author\clsid:: | {f414c261-6ac0-11cf-b6d1-00aa00bbbb58} | RegNtPreCreateKey |
| HKLM\software\classes\javascript author:: | JScript Language Authoring | RegNtPreCreateKey |
| HKLM\software\classes\javascript author\clsid:: | {f414c261-6ac0-11cf-b6d1-00aa00bbbb58} | RegNtPreCreateKey |
| HKLM\software\classes\javascript1.1 author:: | JScript Language Authoring | RegNtPreCreateKey |
| HKLM\software\classes\javascript1.1 author\clsid:: | {f414c261-6ac0-11cf-b6d1-00aa00bbbb58} | RegNtPreCreateKey |
| HKLM\software\classes\javascript1.2 authorjavascript1.3 author:: | JScript Language Authoring | RegNtPreCreateKey |
| HKLM\software\classes\javascript1.2 authorjavascript1.3 author\clsid:: | {f414c261-6ac0-11cf-b6d1-00aa00bbbb58} | RegNtPreCreateKey |
| HKLM\software\classes\ecmascript author:: | JScript Language Authoring | RegNtPreCreateKey |
| HKLM\software\classes\ecmascript author\clsid:: | {f414c261-6ac0-11cf-b6d1-00aa00bbbb58} | RegNtPreCreateKey |
| HKLM\software\classes\wow6432node\clsid\{f414c261-6ac0-11cf-b6d1-00aa00bbbb58}:: | JScript Language Authoring | RegNtPreCreateKey |
| HKLM\software\classes\wow6432node\clsid\{f414c261-6ac0-11cf-b6d1-00aa00bbbb58}\progid:: | JScript Author | RegNtPreCreateKey |
| HKLM\software\classes\wow6432node\clsid\{f414c261-6ac0-11cf-b6d1-00aa00bbbb58}\inprocserver32:: | C:\WINDOWS\SysWow64\jscript.dll | RegNtPreCreateKey |
| HKLM\software\classes\wow6432node\clsid\{f414c261-6ac0-11cf-b6d1-00aa00bbbb58}\inprocserver32::threadingmodel | Both | RegNtPreCreateKey |
| HKLM\software\classes\jscript.encode:: | JScript Language Encoding | RegNtPreCreateKey |
| HKLM\software\classes\jscript.encode\clsid:: | {f414c262-6ac0-11cf-b6d1-00aa00bbbb58} | RegNtPreCreateKey |
| HKLM\software\classes\wow6432node\clsid\{f414c262-6ac0-11cf-b6d1-00aa00bbbb58}:: | JScript Language Encoding | RegNtPreCreateKey |
| HKLM\software\classes\wow6432node\clsid\{f414c262-6ac0-11cf-b6d1-00aa00bbbb58}\progid:: | JScript.Encode | RegNtPreCreateKey |
| HKLM\software\classes\wow6432node\clsid\{f414c262-6ac0-11cf-b6d1-00aa00bbbb58}\inprocserver32:: | C:\WINDOWS\SysWow64\jscript.dll | RegNtPreCreateKey |
| HKLM\software\classes\wow6432node\clsid\{f414c262-6ac0-11cf-b6d1-00aa00bbbb58}\inprocserver32::threadingmodel | Both | RegNtPreCreateKey |
| HKLM\software\classes\jscript.compact:: | JScript Compact Profile (ECMA 327) | RegNtPreCreateKey |
| HKLM\software\classes\jscript.compact\clsid:: | {cc5bbec3-db4a-4bed-828d-08d78ee3e1ed} | RegNtPreCreateKey |
| HKLM\software\classes\wow6432node\clsid\{cc5bbec3-db4a-4bed-828d-08d78ee3e1ed}:: | JScript Compact Profile (ECMA 327) | RegNtPreCreateKey |
| HKLM\software\classes\wow6432node\clsid\{cc5bbec3-db4a-4bed-828d-08d78ee3e1ed}\progid:: | JScript.Compact | RegNtPreCreateKey |
| HKLM\software\classes\wow6432node\clsid\{cc5bbec3-db4a-4bed-828d-08d78ee3e1ed}\inprocserver32:: | C:\WINDOWS\SysWow64\jscript.dll | RegNtPreCreateKey |
| HKLM\software\classes\wow6432node\clsid\{cc5bbec3-db4a-4bed-828d-08d78ee3e1ed}\inprocserver32::threadingmodel | Both | RegNtPreCreateKey |
| HKLM\software\wow6432node\pc purifier::telno | (844) 763-5836 | RegNtPreCreateKey |
| HKLM\software\wow6432node\pc purifier::telnofr | 01.76.54.27.59 | RegNtPreCreateKey |
| HKLM\software\wow6432node\pc purifier::telnode | (800) 180-6512 | RegNtPreCreateKey |
| HKLM\software\wow6432node\pc purifier::telnojp | 03-5050-1410 | RegNtPreCreateKey |
| HKLM\software\wow6432node\pc purifier::showexitpage | RegNtPreCreateKey |
Windows API Usage
Windows API Usage
This section lists Windows API calls that are used by the samples in this family. Windows API usage analysis is a valuable tool that can help identify malicious activity, such as keylogging, security privilege escalation, data encryption, data exfiltration, interference with antivirus software, and network request manipulation.| Category | API |
|---|---|
| Process Shell Execute |
|
| User Data Access |
|
| Keyboard Access |
|
| Network Urlomon |
|
| Syscall Use |
Show More
|
| Process Manipulation Evasion |
|
| Anti Debug |
|
Shell Command Execution
Shell Command Execution
This section lists Windows shell commands that are run by the samples in this family. Windows Shell commands are often leveraged by malware for nefarious purposes and can be used to elevate security privileges, download and launch other malware, exploit vulnerabilities, collect and exfiltrate data, and hide malicious activity.
"C:\Users\Nakwpubg\AppData\Local\Temp\is-KSIFE.tmp\fc97e1e9d728d8c286f2baf4bc87a49c0a57d48a_0004039384.tmp" /SL5="$301DC,3550518,148992,c:\users\user\downloads\fc97e1e9d728d8c286f2baf4bc87a49c0a57d48a_0004039384"
|
"C:\WINDOWS\system32\regsvr32.exe" /s "C:\WINDOWS\system32\jscript.dll"
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\6e2326054dd17e1319dce8b1ac3f3d2c8cc674f7_0000157624.,LiQMAxHB
|
