PC Accelerate Pro
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Popularity Rank: | 229 |
| Threat Level: | 10 % (Normal) |
| Infected Computers: | 614,848 |
| First Seen: | October 13, 2015 |
| Last Seen: | January 29, 2026 |
| OS(es) Affected: | Windows |
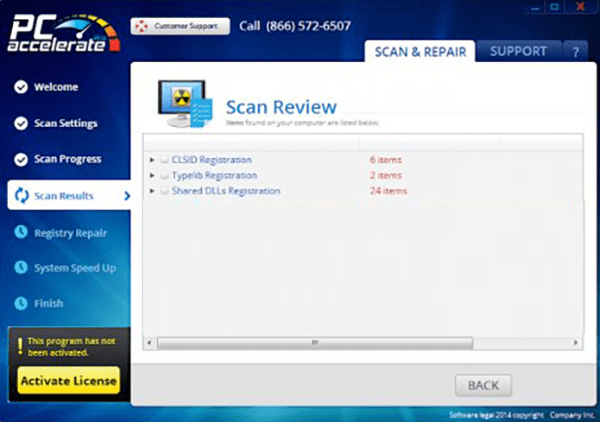
PC Accelerate Pro Image
The PC Accelerate Pro software is developed by Installer Technology Co., is published by DisplayTime Software, and may arrive on your PC via free software packages. The PC Accelerate Pro software is promoted on Pcacceleratepro.com to be a viable alternative to the system tools you can find built-into Windows. The PC Accelerate Pro program may claim to be a powerful system optimization utility that can prevent disk fragmentation and slow performance, as well as delete your traces on the Internet. Many users may be interested in taking advantage of the trial period of two weeks that Installer Technology Co. provides with the PC Accelerate Pro software. However, the behavior of the PC Accelerate Pro program shares many similarities with rogue system managers like Smart PC Cleaner and Windows Accelerator Pro and is perceived as a Potentially Unwanted Program (PUP). The main executable of the PC Accelerate Pro software may be detected as PUP.PC Accelerate Pro and PUP.DisplayTimeSoftware.
The trial period of PC Accelerate Pro allows users to make manual scans and clean their browser cache and search history. Users may perform 'deep scans' with the PC Accelerate Pro software and find hundreds of problems in their Windows Registry that may be repaired with the PRO version of PC Accelerate Pro. Computer experts alert that the PC Accelerate Pro software may not provide accurate information about the problems of your system and show critical error messages to incite you to pay up to $100 for a license that would unlock the PRO functionality. The PC Accelerate Pro program may run as a system driver and be listed in the MSCONFIG tools as a startup service. Contrary to what the PC Accelerate Pro app is advertised to do, it may slow down your PC and make you open your wallet deliberately. Additionally, the PC Accelerate Pro app may perform scans of your running service and prevent you from opening programs for more than five minutes every time you turn on your computer. You should use an anti-spyware tool to delete all files related to the PC Accelerate Pro software and Registry keys it may have left behind.
Table of Contents
SpyHunter Detects & Remove PC Accelerate Pro
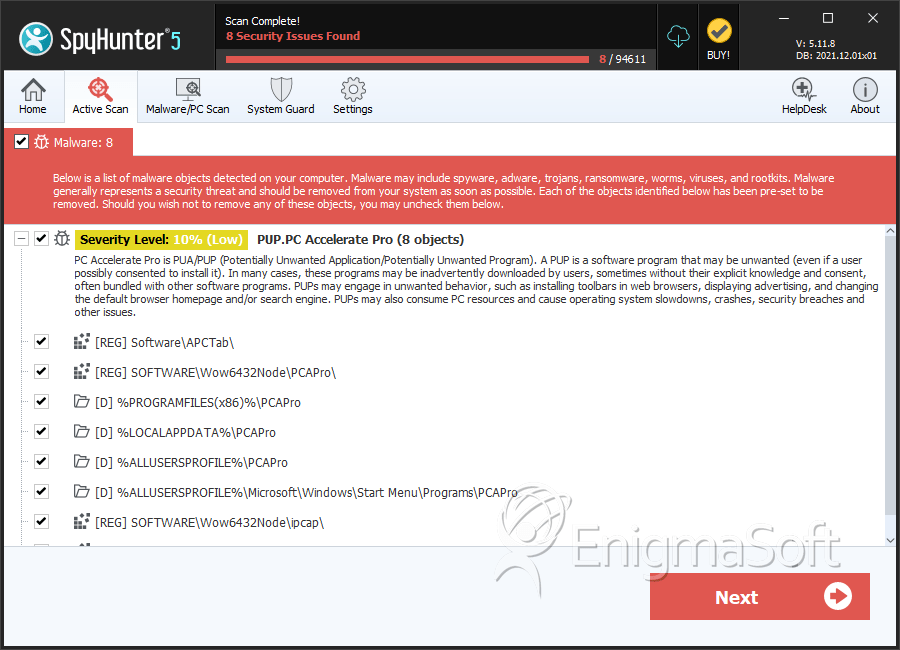
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | PCAcceleratePro.exe | 47f364ecc161cc1c89c3b77409b99719 | 11 |
| 2. | MultiSpeedUp.exe | 988fef29b3eb27587b0c277aaf2c9bf2 | 8 |
| 3. | file.exe | 46758f6cda8caa0d60f89dcc710674f5 | 7 |
| 4. | setup.exe | d7fcf737ebd79f4fbd1a3345ddf7f192 | 5 |
| 5. | PC Accelerate [1].exe | de6318700e4cdda86bd6dd5c19a90599 | 3 |
| 6. | PC Accelerate Pro.exe | 8dae6430be40b94fe55b58241314fb1a | 2 |
| 7. | PC Accelerate [3].exe | af195ec67deba4e7864863cc17c40e31 | 1 |
| 8. | PC Accelerate [2].exe | 1f0a989d0353d15c984759aeef15e721 | 0 |
Registry Details
Directories
PC Accelerate Pro may create the following directory or directories:
| %ALLUSERSPROFILE%\AffairsSpeedup |
| %ALLUSERSPROFILE%\AnswerPCAP |
| %ALLUSERSPROFILE%\Application Data\PC Accelerate Pro |
| %ALLUSERSPROFILE%\Application Data\PCAcceleratePro |
| %ALLUSERSPROFILE%\AweAPCP |
| %ALLUSERSPROFILE%\BrarvaSpeedup |
| %ALLUSERSPROFILE%\CaringSpeedUp |
| %ALLUSERSPROFILE%\ChronoSpeedup |
| %ALLUSERSPROFILE%\DreamOfPcSpeedup |
| %ALLUSERSPROFILE%\FastPCProf |
| %ALLUSERSPROFILE%\KruSpeedup |
| %ALLUSERSPROFILE%\LittleSpeedup |
| %ALLUSERSPROFILE%\MBAffairsSpeedup |
| %ALLUSERSPROFILE%\MBClientPCSpeedup |
| %ALLUSERSPROFILE%\MBOnrymSpeedup |
| %ALLUSERSPROFILE%\MarSpeedp |
| %ALLUSERSPROFILE%\Microsoft\Windows\Start Menu\Programs\PCAPro |
| %ALLUSERSPROFILE%\Microsoft\Windows\Start Menu\Programs\PCAcceleratePro |
| %ALLUSERSPROFILE%\Microsoft\Windows\Start Menu\Programs\ipcap |
| %ALLUSERSPROFILE%\Microsoft\Windows\Start Menu\Programs\miapcp |
| %ALLUSERSPROFILE%\OnrymSpeedup |
| %ALLUSERSPROFILE%\PC Accelerate Pro |
| %ALLUSERSPROFILE%\PC!Accelerate!Pro |
| %ALLUSERSPROFILE%\PCAP |
| %ALLUSERSPROFILE%\PCAPro |
| %ALLUSERSPROFILE%\PCAcceleratePro |
| %ALLUSERSPROFILE%\ProAccelerationOfPC |
| %ALLUSERSPROFILE%\SilverSpeedup |
| %ALLUSERSPROFILE%\Start Menu\Programs\PCAcceleratePro |
| %ALLUSERSPROFILE%\TickTackSpeedup |
| %ALLUSERSPROFILE%\TriocySpeedup |
| %ALLUSERSPROFILE%\TsapriSpeedup |
| %ALLUSERSPROFILE%\TsapriSpeedupit |
| %ALLUSERSPROFILE%\WatchingSpeedup |
| %ALLUSERSPROFILE%\YixSpeedup |
| %ALLUSERSPROFILE%\bokangspeedup |
| %ALLUSERSPROFILE%\bpcapq |
| %ALLUSERSPROFILE%\clientpcspeedup |
| %ALLUSERSPROFILE%\estimatespeedup |
| %ALLUSERSPROFILE%\heavenpcap |
| %ALLUSERSPROFILE%\ineffablepcap |
| %ALLUSERSPROFILE%\ipcap |
| %ALLUSERSPROFILE%\iqpcap |
| %ALLUSERSPROFILE%\limitedpcap |
| %ALLUSERSPROFILE%\miapcp |
| %ALLUSERSPROFILE%\numidapcap |
| %ALLUSERSPROFILE%\pcapcp |
| %ALLUSERSPROFILE%\plazypcap |
| %ALLUSERSPROFILE%\qtpcap |
| %ALLUSERSPROFILE%\usualspcap |
| %ALLUSERSPROFILE%\vemopcap |
| %APPDATA%\Microsoft\Windows\Start Menu\Programs\PCAcceleratePro |
| %APPDATA%\PC Accelerate Pro |
| %APPDATA%\PCAccPro |
| %APPDATA%\PCAcceleratePro |
| %LOCALAPPDATA%\AnswerPCAP |
| %LOCALAPPDATA%\AweAPCP |
| %LOCALAPPDATA%\CaringSpeedUp |
| %LOCALAPPDATA%\DreamOfPcSpeedup |
| %LOCALAPPDATA%\FAPCPro |
| %LOCALAPPDATA%\FastPCProf |
| %LOCALAPPDATA%\KruSpeedup |
| %LOCALAPPDATA%\LittleSpeedup |
| %LOCALAPPDATA%\MBAffairsSpeedup |
| %LOCALAPPDATA%\MBClientPCSpeedup |
| %LOCALAPPDATA%\MBOnrymSpeedup |
| %LOCALAPPDATA%\MarSpeedp |
| %LOCALAPPDATA%\OnrymSpeedup |
| %LOCALAPPDATA%\PC Accelerate Pro |
| %LOCALAPPDATA%\PC!Accelerate!Pro |
| %LOCALAPPDATA%\PCAP |
| %LOCALAPPDATA%\PCAPro |
| %LOCALAPPDATA%\PCAccelerateP |
| %LOCALAPPDATA%\PCAcceleratePro |
| %LOCALAPPDATA%\ProAccelerationOfPC |
| %LOCALAPPDATA%\SilverSpeedup |
| %LOCALAPPDATA%\TickTackSpeedup |
| %LOCALAPPDATA%\TriocySpeedup |
| %LOCALAPPDATA%\TsapriSpeedup |
| %LOCALAPPDATA%\TsapriSpeedupit |
| %LOCALAPPDATA%\WatchingSpeedup |
| %LOCALAPPDATA%\bokangspeedup |
| %LOCALAPPDATA%\bpcapq |
| %LOCALAPPDATA%\clientpcspeedup |
| %LOCALAPPDATA%\estimatespeedup |
| %LOCALAPPDATA%\heavenpcap |
| %LOCALAPPDATA%\ineffablepcap |
| %LOCALAPPDATA%\ipcap |
| %LOCALAPPDATA%\iqpcap |
| %LOCALAPPDATA%\iqpcap_dfolder |
| %LOCALAPPDATA%\limitedpcap |
| %LOCALAPPDATA%\miapcp |
| %LOCALAPPDATA%\numidapcap |
| %LOCALAPPDATA%\pcapcp |
| %LOCALAPPDATA%\plazypcap |
| %LOCALAPPDATA%\usualspcap |
| %LOCALAPPDATA%\vemopcap |
| %LOCALAPPDATA%\xpcap |
| %LOCALPPADATA%\qtpcap |
| %LOCALPPADATA%\qtpcap_dfolder |
| %PROGRAMFILES%\AnswerPCAP |
| %PROGRAMFILES%\AweAPCP |
| %PROGRAMFILES%\CaringSpeedUp |
| %PROGRAMFILES%\DreamOfPcSpeedup |
| %PROGRAMFILES%\FAPCPro |
| %PROGRAMFILES%\FastPCProf |
| %PROGRAMFILES%\Installer_P.C.A.P |
| %PROGRAMFILES%\KruSpeedup |
| %PROGRAMFILES%\LittleSpeedup |
| %PROGRAMFILES%\MBAffairsSpeedup |
| %PROGRAMFILES%\MBClientPCSpeedup |
| %PROGRAMFILES%\MBOnrymSpeedup |
| %PROGRAMFILES%\MarSpeedp |
| %PROGRAMFILES%\MirxayzarAPCP |
| %PROGRAMFILES%\MultiSpeedUp |
| %PROGRAMFILES%\PC!Accelerate!Pro |
| %PROGRAMFILES%\PCAP |
| %PROGRAMFILES%\PCAPDownloader |
| %PROGRAMFILES%\PCAccPro |
| %PROGRAMFILES%\PCAccelerateP |
| %PROGRAMFILES%\PCAcceleratePro |
| %PROGRAMFILES%\ProAccelerationOfPC |
| %PROGRAMFILES%\RedSpeedup |
| %PROGRAMFILES%\SilverSpeedup |
| %PROGRAMFILES%\TickTackSpeedup |
| %PROGRAMFILES%\TsapriSpeedup |
| %PROGRAMFILES%\TsapriSpeedupit |
| %PROGRAMFILES%\WatchingSpeedup |
| %PROGRAMFILES%\acceleratepcpro |
| %PROGRAMFILES%\bokangspeedup |
| %PROGRAMFILES%\bpcapq |
| %PROGRAMFILES%\clientpcspeedup |
| %PROGRAMFILES%\heavenpcap |
| %PROGRAMFILES%\ineffablepcap |
| %PROGRAMFILES%\ipcap |
| %PROGRAMFILES%\iqpcap |
| %PROGRAMFILES%\limitedpcap |
| %PROGRAMFILES%\miapcp |
| %PROGRAMFILES%\numidapcap |
| %PROGRAMFILES%\pcapcp |
| %PROGRAMFILES%\plazypcap |
| %PROGRAMFILES%\qtpcap |
| %PROGRAMFILES%\usualspcap |
| %PROGRAMFILES%\vemopcap |
| %PROGRAMFILES%\xpcap |
| %PROGRAMFILES(x86)%\FAPCPro |
| %PROGRAMFILES(x86)%\Installer_P.C.A.P |
| %PROGRAMFILES(x86)%\PC!Accelerate!Pro |
| %PROGRAMFILES(x86)%\PCAP |
| %PROGRAMFILES(x86)%\PCAPDownloader |
| %PROGRAMFILES(x86)%\PCAPro |
| %PROGRAMFILES(x86)%\PCAccPro |
| %PROGRAMFILES(x86)%\PCAccelerateP |
| %PROGRAMFILES(x86)%\PCAcceleratePro |
| %PROGRAMFILES(x86)%\TsapriSpeedupit |
| %PROGRAMFILES(x86)%\acceleratepcpro |
| %PROGRAMFILES(x86)%\bokangspeedup |
| %PROGRAMFILES(x86)%\bpcapq |
| %PROGRAMFILES(x86)%\heavenpcap |
| %PROGRAMFILES(x86)%\ineffablepcap |
| %PROGRAMFILES(x86)%\ipcap |
| %PROGRAMFILES(x86)%\iqpcap |
| %PROGRAMFILES(x86)%\limitedpcap |
| %PROGRAMFILES(x86)%\miapcp |
| %PROGRAMFILES(x86)%\numidapcap |
| %PROGRAMFILES(x86)%\pcapcp |
| %PROGRAMFILES(x86)%\plazypcap |
| %PROGRAMFILES(x86)%\qtpcap |
| %PROGRAMFILES(x86)%\usualspcap |
| %PROGRAMFILES(x86)%\vemopcap |
| %PROGRAMFILES(x86)%\xpcap |
| %ProgramFiles%\TrouqrinSpeedup |
| %UserProfile%\Local Settings\Application Data\PC Accelerate Pro |
| %allusersprofile%\xpcap |
| %localappdata%\RedSpeedup |
| %programfiles%\EstimateSpeedUp |
Analysis Report
General information
| Family Name: | PUP.PC Accelerate Pro |
|---|---|
| Signature status: | Root Not Trusted |
Known Samples
Known Samples
This section lists other file samples believed to be associated with this family.|
MD5:
933868694e5636c8da5f1ee9e2696825
SHA1:
7b2a2ca22d44d00f1fa29b3d27133218d9c76171
File Size:
314.39 KB, 314392 bytes
|
|
MD5:
75963ece52fad8b63497240cadfb91c8
SHA1:
340fd8a692dc15431f727414113ad44d2ee7f89c
File Size:
7.64 MB, 7643136 bytes
|
|
MD5:
d9e678a06add7be1a5514cccdf9b0746
SHA1:
013ef8c5b8ae67f1b9fb78207fd31fa7b27e8eb6
File Size:
92.30 KB, 92304 bytes
|
|
MD5:
1d66785aa4d874e44b5eb86bf43019a1
SHA1:
f8088a5d663f3a5f6614186007e44cf50442bb89
SHA256:
D266566780E3E8E5A73AD858ADB6ECD3C07C4DE0F8704911E374D29FCEA54961
File Size:
2.76 MB, 2760704 bytes
|
|
MD5:
79e68bbdafbbae23784865a4492345b8
SHA1:
2ea6c2c11c8b4dbe7c5c515010cfe7c98b67ff21
SHA256:
FDF5A8A9E226A1927C545F920F445879972C6E1F0A41C96F8080E917DDE72D80
File Size:
2.43 MB, 2425112 bytes
|
Show More
|
MD5:
8d9d52642e581c199b9481e00d130595
SHA1:
893f67e07d90852faadd1b876e05e57553df08ad
SHA256:
FFDFC1B7CB95D2E991AA80AF65140A0DF129955D1E789A491216279FE9ED790A
File Size:
109.57 KB, 109568 bytes
|
|
MD5:
d1060f74183bf639fcc385221c850c11
SHA1:
25ca537ce16208c830a557a5f43e4d2022f77a78
SHA256:
ED5A438FEAD3AF1A2B9551B424A0450A275C2935D05063CACAA1DD33A3D2A65C
File Size:
9.74 MB, 9740288 bytes
|
|
MD5:
5258c0d0012089b93079869bf2993af2
SHA1:
20e5aa6acaefa71755ea710ff5f3ab878c37fb64
SHA256:
1537E06290F5A41F1635A29DF4BBF29B7C992F168AFD9574B09F9057B4AD2A32
File Size:
92.30 KB, 92296 bytes
|
|
MD5:
e4a8ee39021906bc42a9143a8ffd2a21
SHA1:
8a290881ec3d16e9b12e06d0c4fc825ba6c1325e
SHA256:
383E99447DD6B4CA8BB82D0EB11811E8E01100D8730CDAB52AF03CE199211B02
File Size:
205.26 KB, 205256 bytes
|
|
MD5:
82fba38bb036f5a638f83328528cd839
SHA1:
1fd6499ec3f028a49f6529d05401e8739cd25ba3
SHA256:
69B782E640B2D25FEA94E7E70A2297669D29222B6446A63C8E7EAE64C39EB6C2
File Size:
109.57 KB, 109568 bytes
|
|
MD5:
1c7ca0eb06e9e472d603cd00c19f0c17
SHA1:
b94610cb5233f9f22576fa63300863b03daf334d
SHA256:
D3C1568A1BC9AF434A4A6F3D27CC7E41C8A6DE113CB9145BEC542C38E40D6418
File Size:
9.15 MB, 9147496 bytes
|
|
MD5:
445ab9ee19b15df90a4a9d5ca5226a1c
SHA1:
74970bcdf2209985c410c08c0ad059df50d6426d
SHA256:
E09566F5D9D989A0987E6274483A132CADF5A06B0E2C19F77669BA2563461CB9
File Size:
432.80 KB, 432800 bytes
|
|
MD5:
01c95f3150f21c1c07143fd9fe47997f
SHA1:
c5cd8e8f85a462d02e9d4a455233e7058bc9a604
SHA256:
766AD553AC831047771473D86B505A829C5FDF8960ED2489A6EDFCA09B2D9A92
File Size:
366.40 KB, 366400 bytes
|
|
MD5:
8072c8021dd250395221ee8833886a02
SHA1:
341914b513f79e6cf4a3ea465c53a3ecb6522015
SHA256:
A0FDD3223194727A1E527212A003080115CF797F5AE9D98B3BBC6DEA3B8A3012
File Size:
69.12 KB, 69120 bytes
|
|
MD5:
d612d646b4dec7d97348296e6c537d18
SHA1:
aae5ab0c4583e8497911ea0df3d357cd06a97969
SHA256:
97688B4BEFD5D36C1235E6F27BA8644B42A8702F9BC3A01626C0871DCA82434B
File Size:
66.05 KB, 66048 bytes
|
|
MD5:
a7fc5b2aa571ef9ec1ec8bc0c0a0d4f9
SHA1:
0227789f8c538bedf05b67cbcf1efb6648450211
SHA256:
D01A5007FA9D13231E7555BEAD8F0259CE8D24D50F66062BB4B40B215BC11C90
File Size:
4.71 MB, 4710400 bytes
|
|
MD5:
c05f4c8bf82e5df1281474830af806e0
SHA1:
b18bcda223bdeb0c7126fb43cc4aa2058702de1f
SHA256:
236E5A53D1E5DFCAA4601F8DDF23849140B859A78900248DAB8298A04256D025
File Size:
5.19 MB, 5193728 bytes
|
|
MD5:
515d49402dcf8cf4f6a99d3bbdec1a41
SHA1:
d285b5310be73b5d558b29f9131dae23647ed623
SHA256:
D06E54517AAE310F9CA765F21BC75A59C173E19ED1F842706EBD74D561A30A8C
File Size:
2.33 MB, 2325320 bytes
|
|
MD5:
98ef9fbd557d5b4bfd531e90205b98b9
SHA1:
31944df66ff9cabf53fa73c266d6fbb18e1923b6
SHA256:
2A02489122E892FD09DF45602254565728FBB1BA6064331870A34E61D2ABD711
File Size:
2.98 MB, 2975760 bytes
|
|
MD5:
a5cd2ca8262898ae400ac913c8a55317
SHA1:
cd65e6c258ce44e174609a82e18c6d4232089fed
SHA256:
74EE3A887CFCF2650811C0EB8D836C72F135EFE54F194D50BBC311526811EA34
File Size:
92.30 KB, 92304 bytes
|
|
MD5:
c2bb451df5e86489f5760301e8c5876a
SHA1:
2a58f5740d1620cbdad0e4211375a1004ebe7977
SHA256:
08D961C6CF8756C28227ECFB9E9253C3B0B112E6DF1DAAEBD04A426B8AA694F7
File Size:
485.08 KB, 485080 bytes
|
|
MD5:
62fbc7a717a7ae12bab8d4a7143c0fa3
SHA1:
da1fb90a4ea1b5db2b94caf32aa49876d79fdf09
SHA256:
D4142839BB801E16D22D9AA554F292EDE219433F8579BBE9A92B6158601F8CBD
File Size:
346.59 KB, 346592 bytes
|
|
MD5:
3182718c57d21917457cec02d892d321
SHA1:
415dfead14be7570884dabf9d7dd0fcb4205c394
SHA256:
7A9A55AEECA466684DC642FB13ECD66F33707DEBAF510B65E11E09D719E962D0
File Size:
17.41 KB, 17408 bytes
|
|
MD5:
4f9743d66202d6b2c83425c7cc2b22e6
SHA1:
1fb292bd5ce71566f92d8426a125b7a04e540db4
SHA256:
99F343DFF27E7E8A6E1697C285DC2658509C6DE12BA8FF27F33A7ECA205EACD7
File Size:
2.60 MB, 2596864 bytes
|
|
MD5:
99b6c90b9375671bbfa3390ffb9b67b1
SHA1:
7b1a2578c668802a37805a5fd819d4df6555d818
SHA256:
3796D4DA73AC92B36139F2AB516DA49A8EBB01F7C85B7DCE90641DB6BB9FA2F0
File Size:
3.81 MB, 3809280 bytes
|
|
MD5:
01c8a6af6efc97898d83b69b36166475
SHA1:
c37d029b657450544dbb8b8596b8e12bdfb32625
SHA256:
814B403322BD310259DE899B5EC77F312060004A9DC023FB133CDF76D78CA848
File Size:
1.73 MB, 1733112 bytes
|
|
MD5:
79eda0ae5d15c15176ada3d17043035e
SHA1:
dd83d8feb3fdaa3edc7d2e7f9781efa80c12b407
SHA256:
9399E3C80E2775B8DF437E0EFEA3AB51CED84FE8F87BF66ED7346FFD0B2E773F
File Size:
346.39 KB, 346392 bytes
|
|
MD5:
b8d4fcbc4fc50c927cc71cb4cd6532f4
SHA1:
525733d13ffed1cd0daf4a139a0a7aa23df6129d
SHA256:
F8FD9F44CEDDB8A789530D12A470BCFAB97EFF0058A1F71E10C1D81FC6C0ACE8
File Size:
95.06 KB, 95064 bytes
|
|
MD5:
28a32135c8cefa2ea59784629f6af4b4
SHA1:
fe553e18379b451436cb34d70deeb56bdcc13209
SHA256:
045D8F332216019927108E7D3F137B19796526975EC2D2D965507D210E3DC83E
File Size:
435.40 KB, 435400 bytes
|
|
MD5:
d5f03cf44deb8ce18d858c0e5dcfdc22
SHA1:
837a3d8023ec98beee90825dfd4783c09b9766b9
SHA256:
B49A033B6D8A8AAD51B983FF585D8032564D29503033288CD1455393C4A2B7D0
File Size:
92.30 KB, 92304 bytes
|
|
MD5:
d54a95d8f6a27402f012711a40fb9afe
SHA1:
ec8c1d0aca379e267bb66a479df1b10858e4c462
SHA256:
39395578FDD0E20BFE0FDBE7F2189D87A4543FAB2AF1D126511E03EF4075264C
File Size:
69.12 KB, 69120 bytes
|
|
MD5:
51c58b27adecd7c9f19a54281a20d104
SHA1:
c4e2ea846f9231d7dbd2fe64c84735b29cc7d311
SHA256:
3F2CE1AB7DC5FEF3BBBFE51462061229FEC495B8B0B498AB622B2FFC9D7FF866
File Size:
4.10 MB, 4096000 bytes
|
Windows Portable Executable Attributes
- File doesn't have "Rich" header
- File doesn't have debug information
- File doesn't have exports table
- File doesn't have relocations information
- File doesn't have security information
- File has exports table
- File has TLS information
- File is 32-bit executable
- File is 64-bit executable
- File is console application (IMAGE_SUBSYSTEM_WINDOWS_CUI)
Show More
- File is either console or GUI application
- File is GUI application (IMAGE_SUBSYSTEM_WINDOWS_GUI)
- File is Native application (NOT .NET application)
- File is not packed
- IMAGE_FILE_DLL is not set inside PE header (Executable)
- IMAGE_FILE_EXECUTABLE_IMAGE is set inside PE header (Executable Image)
File Icons
File Icons
This section displays icon resources found within family samples. Malware often replicates icons commonly associated with legitimate software to mislead users into believing the malware is safe.Show More
Windows PE Version Information
Windows PE Version Information
This section displays values and attributes that have been set in the Windows file version information data structure for samples within this family. To mislead users, malware actors often add fake version information mimicking legitimate software.| Name | Value |
|---|---|
| Company Name |
|
| File Description |
Show More
|
| File Version |
|
| Internal Name |
Show More
|
| Legal Copyright |
Show More
|
| Legal Trademarks | Prime Quinta Update Software - Ragunathan Limited |
| Original Filename |
Show More
|
| Product Name |
Show More
|
| Product Version |
|
Digital Signatures
Digital Signatures
This section lists digital signatures that are attached to samples within this family. When analyzing and verifying digital signatures, it is important to confirm that the signature’s root authority is a well-known and trustworthy entity and that the status of the signature is good. Malware is often signed with non-trustworthy “Self Signed” digital signatures (which can be easily created by a malware author with no verification). Malware may also be signed by legitimate signatures that have an invalid status, and by signatures from questionable root authorities with fake or misleading “Signer” names.| Signer | Root | Status |
|---|---|---|
| AlorSoftInc | AlorSoftInc | Root Not Trusted |
| AweAPCPOptima | AweAPCPOptima | Root Not Trusted |
| PC Accelerate Sales Inc | COMODO RSA Code Signing CA | Self Signed |
| RAGUNATHAN LIMITED | COMODO RSA Code Signing CA | Self Signed |
| ClientPCSpeedupCorp | ClientPCSpeedupCorp | Root Not Trusted |
Show More
| DIGI MICROSERVICE LIMITED | DigiCert EV Code Signing CA (SHA2) | Self Signed |
| DinyiAPCPGroup | DinyiAPCPGroup | Self Signed |
| EpiphanyAPCPComp | EpiphanyAPCPComp | Root Not Trusted |
| KusushiSpeedupSoft | KusushiSpeedupSoft | Root Not Trusted |
| RoomyJigsaw | RoomyJigsaw | Self Signed |
| SentrySpeedupInc | SentrySpeedupInc | Root Not Trusted |
| SmartAPCPFirm | SmartAPCPFirm | Root Not Trusted |
| Sanem Application Tools Limited | USERTrust RSA Certification Authority | Root Not Trusted |
File Traits
- dll
- Installer Manifest
- Installer Version
- nosig nsis
- Nullsoft Installer
- x86
Block Information
Block Information
During analysis, EnigmaSoft breaks file samples into logical blocks for classification and comparison with other samples. Blocks can be used to generate malware detection rules and to group file samples into families based on shared source code, functionality and other distinguishing attributes and characteristics. This section lists a summary of this block data, as well as its classification by EnigmaSoft. A visual representation of the block data is also displayed, where available.Similar Families
Similar Families
This section lists other families that share similarities with this family, based on EnigmaSoft’s analysis. Many malware families are created from the same malware toolkits and use the same packing and encryption techniques but uniquely extend functionality. Similar families may also share source code, attributes, icons, subcomponents, compromised and/or invalid digital signatures, and network characteristics. Researchers leverage these similarities to rapidly and effectively triage file samples and extend malware detection rules.- Agent.MX
- BadJoke.JB
- BadJoke.XA
- Chuyun.A
- ConvertAd.D
Show More
- Downloader.Agent.EG
- Elex.DBA
- Farfli.AB
- Farfli.TB
- Filecoder.GYT
- KeyLogger.CF
- KillMBR.XE
- Kryptik.HFH
- Kryptik.LFB
- Lumma.DA
- OpenSUpdater.L
- OpenSUpdater.MC
- Perion.C
- Quasar.U
- Socelars.AD
- Stealer.KF
- Superweb.B
- Superweb.CA
- Trojan.Filecoder.Gen.C
Files Modified
Files Modified
This section lists files that were created, modified, moved and/or deleted by samples in this family. File system activity can provide valuable insight into how malware functions on the operating system.| File | Attributes |
|---|---|
| c:\program files (x86)\ithelper\config.json | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\nsfb896.tmp | Synchronize,Write Attributes |
| c:\users\user\appdata\local\temp\nsfb896.tmp\bicuz.dll | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\nsfb896.tmp\bicuz.dll | Synchronize,Write Attributes |
| c:\users\user\appdata\local\temp\nsfb896.tmp\dialogs.dll | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\nsfb896.tmp\dialogs.dll | Synchronize,Write Attributes |
| c:\users\user\appdata\local\temp\nsfb896.tmp\inetc.dll | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\nsfb896.tmp\inetc.dll | Synchronize,Write Attributes |
| c:\users\user\appdata\local\temp\nsfb896.tmp\nsjson.dll | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\nsfb896.tmp\nsjson.dll | Synchronize,Write Attributes |
Show More
| c:\users\user\appdata\local\temp\nsfb896.tmp\system.dll | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\nsfb896.tmp\system.dll | Synchronize,Write Attributes |
| c:\users\user\appdata\local\temp\nsfb896.tmp\toplogo1.bmp | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\nsfb896.tmp\toplogo1.bmp | Synchronize,Write Attributes |
| c:\users\user\appdata\local\temp\nspb885.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete |
Registry Modifications
Registry Modifications
This section lists registry keys and values that were created, modified and/or deleted by samples in this family. Windows Registry activity can provide valuable insight into malware functionality. Additionally, malware often creates registry values to allow itself to automatically start and indefinitely persist after an initial infection has compromised the system.| Key::Value | Data | API Name |
|---|---|---|
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Users\Yhhfvqxb\AppData\Local\Temp\nsfB896.tmp\ | RegNtPreCreateKey |
Windows API Usage
Windows API Usage
This section lists Windows API calls that are used by the samples in this family. Windows API usage analysis is a valuable tool that can help identify malicious activity, such as keylogging, security privilege escalation, data encryption, data exfiltration, interference with antivirus software, and network request manipulation.| Category | API |
|---|---|
| Network Wininet |
|
| Anti Debug |
|
| User Data Access |
|
| Other Suspicious |
|
| Syscall Use |
Show More
|
| Process Shell Execute |
|
| Process Manipulation Evasion |
|
Shell Command Execution
Shell Command Execution
This section lists Windows shell commands that are run by the samples in this family. Windows Shell commands are often leveraged by malware for nefarious purposes and can be used to elevate security privileges, download and launch other malware, exploit vulnerabilities, collect and exfiltrate data, and hide malicious activity.
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\8a290881ec3d16e9b12e06d0c4fc825ba6c1325e_0000205256.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\b94610cb5233f9f22576fa63300863b03daf334d_0009147496.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\74970bcdf2209985c410c08c0ad059df50d6426d_0000432800.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\c5cd8e8f85a462d02e9d4a455233e7058bc9a604_0000366400.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\341914b513f79e6cf4a3ea465c53a3ecb6522015_0000069120.,LiQMAxHB
|
Show More
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\aae5ab0c4583e8497911ea0df3d357cd06a97969_0000066048.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\da1fb90a4ea1b5db2b94caf32aa49876d79fdf09_0000346592.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\415dfead14be7570884dabf9d7dd0fcb4205c394_0000017408.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\dd83d8feb3fdaa3edc7d2e7f9781efa80c12b407_0000346392.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\fe553e18379b451436cb34d70deeb56bdcc13209_0000435400.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\ec8c1d0aca379e267bb66a479df1b10858e4c462_0000069120.,LiQMAxHB
|
