Pass to Post Ads
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 20 % (Normal) |
| Infected Computers: | 38 |
| First Seen: | March 11, 2016 |
| Last Seen: | May 10, 2019 |
| OS(es) Affected: | Windows |
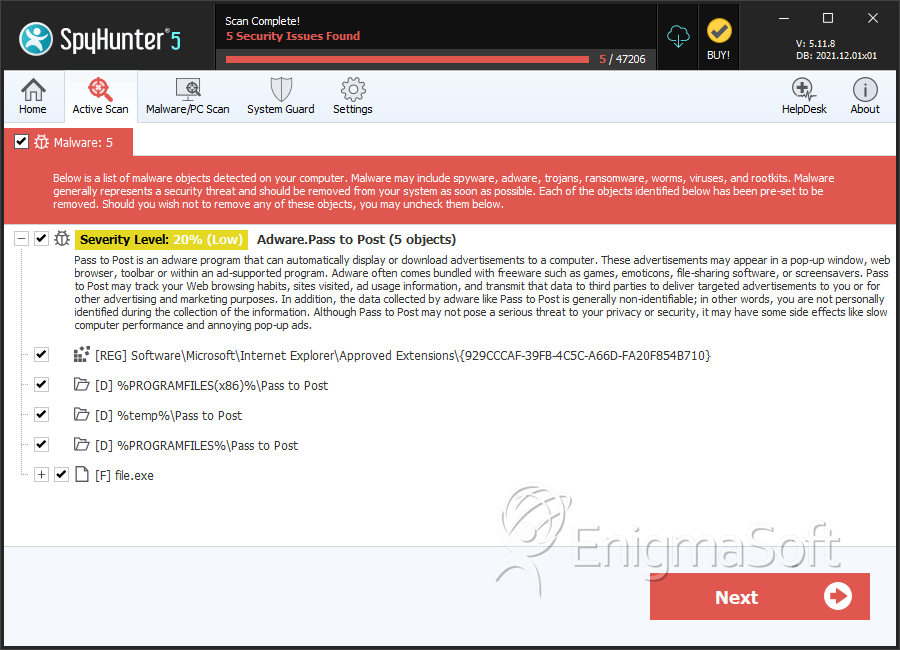
The Pass to Post browser plug-in that you may be surprised to see in your Extensions Manager is developed by the infamous Yontoo LLC and falls into the category of adware. The Pass to Post adware is promoted as a browser plug-in that can help users organize their email inbox better and faster, and access attached files intuitively. However, the Pass to Post adware does not provide resources on its own and may bookmark pages at Forbes.com, Mindtools.com, and Lifehacker.com to provide the functionality you were promised. The Pass to Post adware is not created for the purpose of helping users organize their emails but to help its developers earn substantial pay-per-click revenue from pushing advertising content in your browser. The Pass to Post adware may use JavaScript to load pop-up windows, banners, and transitional advertisements while you surf the Internet. The Pass to Post adware may host video commercials on your new tab page and reroute your Web traffic to affiliate online stores. The Pass to Post adware may edit your DNS configuration to prevent you from shopping at trusted online stores like Amazon and Best Buy.
Security experts note that the Pass to Post adware is similar to Candle Jar and GadgetPrise and may welcome users to provide their email address and mobile phone number to access exclusive deals and offers. Needless to say, users should not provide their contact information to the marketers associated with the Pass to Post adware to avoid being spammed. The Pass to Post adware may use your system resources to mine digital currency like DigiCoin, Litecoin, and Bitcoin to generate a steady stream of revenue for its creators. Therefore, your PC may run at a diminished capacity, and you may not be able to play games and manipulate HD graphics correctly. Security experts reveal that the Pass to Post adware may connect to remote servers over insecure channels to download promotional materials on your hard drive and show notifications on your desktop when your browser is closed. The proper method to remove the Pass to Post adware is by installing a credible anti-spyware instrument that can detect and remove the binary associated with the Pass to Post adware.
Table of Contents
SpyHunter Detects & Remove Pass to Post Ads
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | 6e8b61e0ee751dd83946c8c8e7a7610b | 0 |
Registry Details
Directories
Pass to Post Ads may create the following directory or directories:
| %PROGRAMFILES%\Pass to Post |
| %PROGRAMFILES(x86)%\Pass to Post |
| %temp%\Pass to Post |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.