Nworm
The Nworm component is a feature present in the notorious TrickBot infostealer. This feature appears to have first been introduced to the TrickBot infostealer in April 2020.
The goal of the Nworm feature is to make the TrickBot infostealer operate very silently. However, to achieve this, the Nworm module prevents the threat from gaining persistence on the infected host. Most insfostealers would make sure to gain persistence on the compromised system to make sure that they will be able to operate for longer periods, and therefore exfiltrate more data.
However, the operators of the TrickBot infostealer may have made a smart choice to get rid of the persistence feature in return for a threat that operates very silently. This is because the TrickBot infostealer targets servers instead of regular PCs mainly.
Since servers are far less likely to be rebooted regularly, the persistence feature is not crucial for a successful infostealing campaign. Because of the Nworm module, the TrickBot infostealer runs directly from the memory of the infected host, thus leaving little to no traces of its activity. This makes it very difficult to detect the presence of the TrickBot infostealer on a compromised system. It also makes it rather hard to determine whether the TrickBot infostealer has breached the system in the past.
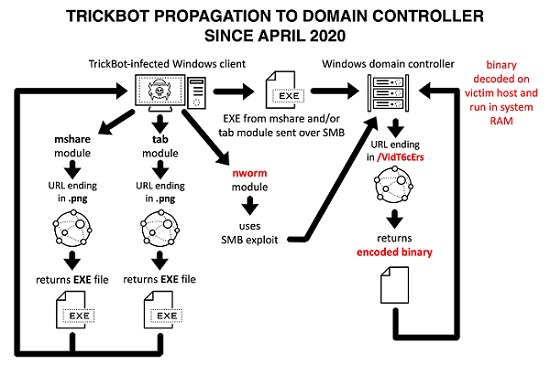
TrickBot propagation.
Source: unit42.paloaltonetworks.com
Another feature introduced by the Nworm module is the utilization of a complex encryption and decryption process. This is yet another feature that helps the TrickBot infostealer operate very stealthy. Before the introduction of this module, the TrickBot infostealer would fetch the payload in a plain format – this makes it very easy for security measures to spot the harmful activity of the threat and therefore halt the attack.
The HTTP traffic caused by Nworm is considerably different than the one generated by the previously used Mworm module:
- URL for TrickBot EXE through Mworm ends with: [/]images/redcar.png
- URL for TrickBot EXE through Nworm ends with: [/]ico/VidT6cErs
- Mworm: TrickBot EXE returned unencrypted in HTTP traffic
- Nworm: TrickBot EXE returned encrypted in HTTP traffic
Since the introduction of the Nworm component, it has become clear that the operators of the TrickBot infostealer are putting emphasis on stealth over persistence and targeting servers, rather than personal computers.
URLs
Nworm may call the following URLs:
| http://107.172.221.106/ico/VidT6cErs |
| http://107.172.221.106/images/cursor.png |
| http://107.172.221.106/images/imgpaper.png |
| http://23.95.227.159/ico/VidT6cErs |
| http://23.95.227.159/images/cursor.png |
| http://23.95.227.159/images/imgpaper.png |

