Montiera Toolbar
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Popularity Rank: | 2,451 |
| Threat Level: | 50 % (Medium) |
| Infected Computers: | 19,219 |
| First Seen: | May 28, 2012 |
| Last Seen: | December 22, 2025 |
| OS(es) Affected: | Windows |
Montiera Toolbar is a potentially unwanted program (PUP)/browser plug-in, which may access the PC without the computer user's agreement. Montiera Toolbar may change the default homepage and search service on the computer system with its own website and display non-stop pop-up advertisements throghout Web search sessions. In fact, activities of Montiera Toolbar may probably be executed for the commercial intention only because computer users may always be urged by Montiera Toolbar to visit questionable websites that may pay for its authprs for boosting their traffic. If the PC user has been diverted to such suspicious websites, he should go away from it immediately because the computer system may be affected by malware threats or other PC infections. Montiera Toolbar may invade the PC via two different tactics. Montiera Toolbar may be downloaded from its official website or it may propagate and enter the PC through packaged free software.
Table of Contents
SpyHunter Detects & Remove Montiera Toolbar
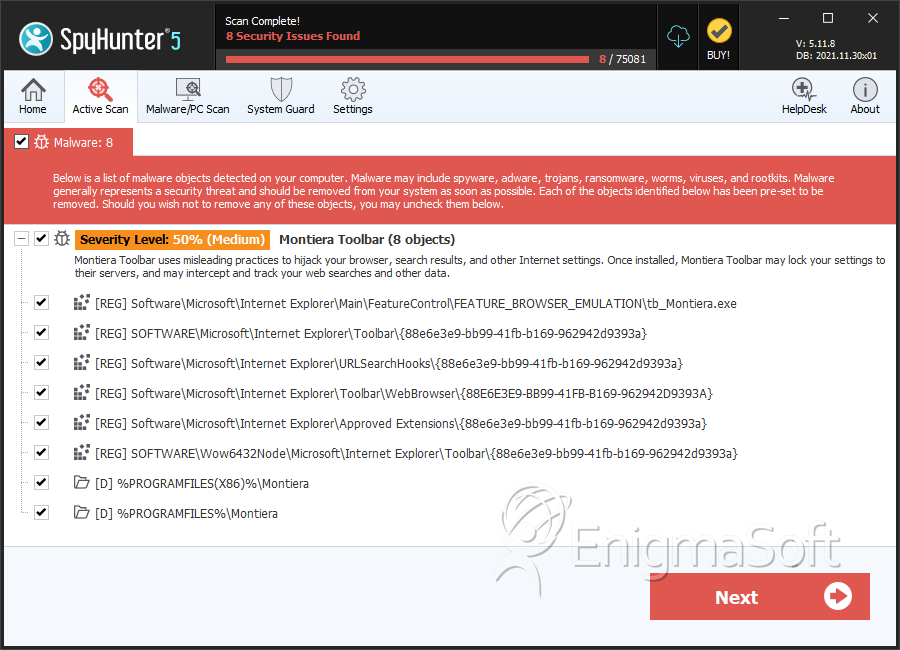
Registry Details
Directories
Montiera Toolbar may create the following directory or directories:
| %APPDATA%\Montiera |
| %LOCALAPPDATA%\NativeMessaging\CT3232085 |
| %LocalAppData%\Google\Chrome\User Data\Default\Extensions\hadddalehlfhlejijophcfblmnejelkb |
| %LocalAppData%\Google\Chrome\User Data\Default\Local Extension Settings\hadddalehlfhlejijophcfblmnejelkb |
| %PROGRAMFILES%\Montiera |
| %PROGRAMFILES(X86)%\Montiera |
| %USERPROFILE%\AppData\LocalLow\Montiera |
Analysis Report
General information
| Family Name: | Montiera Toolbar |
|---|---|
| Signature status: | No Signature |
Known Samples
Known Samples
This section lists other file samples believed to be associated with this family.|
MD5:
e7abed8be82d55a905a6a47d7c6aae18
SHA1:
e07a2e5337e7c9f7b4d861f9b8e1a2de60b6e751
SHA256:
2A016BAF99C73A3177B661CBCE2096E6D530C7B8A12649FEF759CFC9E4EAC22B
File Size:
1.30 MB, 1299822 bytes
|
|
MD5:
713498c43504a35c4477e9ff9fdb577f
SHA1:
d24573cdf723355fe830251042fcaf3369693823
SHA256:
2AF553572D152B406779547BECC7248533FD57275C4396CFFC33E1E33E580976
File Size:
1.22 MB, 1217023 bytes
|
|
MD5:
d9d8503bca3462cb405d6fe9b57a64f8
SHA1:
3649bbefd6e9d34252fa0aa6a15c953d5aa43101
SHA256:
D71387E1F3D9EFD925D0F5AF64972B2CAC7C6FC4EC25FF2B1CFAAAEEC2F8AB26
File Size:
1.22 MB, 1216977 bytes
|
|
MD5:
7c9d62e716c518261dcdb556e825fd64
SHA1:
0ba76e63633861dec0543ac872338ee0d657a849
SHA256:
41B0939B07F107D750F43BC8EC00026A6AD119706BB4CD0A047B54921B5DE151
File Size:
1.22 MB, 1217092 bytes
|
Windows Portable Executable Attributes
- File doesn't have "Rich" header
- File doesn't have debug information
- File doesn't have exports table
- File doesn't have relocations information
- File doesn't have security information
- File is 32-bit executable
- File is either console or GUI application
- File is GUI application (IMAGE_SUBSYSTEM_WINDOWS_GUI)
- File is Native application (NOT .NET application)
- File is not packed
Show More
- IMAGE_FILE_DLL is not set inside PE header (Executable)
- IMAGE_FILE_EXECUTABLE_IMAGE is set inside PE header (Executable Image)
File Icons
File Icons
This section displays icon resources found within family samples. Malware often replicates icons commonly associated with legitimate software to mislead users into believing the malware is safe.Windows PE Version Information
Windows PE Version Information
This section displays values and attributes that have been set in the Windows file version information data structure for samples within this family. To mislead users, malware actors often add fake version information mimicking legitimate software.| Name | Value |
|---|---|
| File Version | 1.00 |
| Internal Name | TJprojMain |
| Original Filename | TJprojMain.exe |
| Product Name | Project1 |
| Product Version | 1.00 |
Windows API Usage
Windows API Usage
This section lists Windows API calls that are used by the samples in this family. Windows API usage analysis is a valuable tool that can help identify malicious activity, such as keylogging, security privilege escalation, data encryption, data exfiltration, interference with antivirus software, and network request manipulation.| Category | API |
|---|---|
| Other Suspicious |
|