Loioir
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 10 % (Normal) |
| Infected Computers: | 51 |
| First Seen: | January 22, 2016 |
| Last Seen: | November 27, 2022 |
| OS(es) Affected: | Windows |
The Loioir malware is a Trojan that is designed to carry out Distributed-Denial-of-Service attacks on computer networks and servers that have access to the Internet via a public Web portal. The Loioir Trojan is similar to Orbyddos, BlackRev, and Orbiter, and can be operated remotely. The Loioir malware may be spread among users by using Trojan-Downloaders such as Winpud and Bartallex and exploit kits such as Sweet Orange. The Loioir Trojan is not programmed to collect information and is not a threat to your sensitive data, but Loioir may hijack most of your system resources and Internet traffic to execute its operations. The Loioir Trojan may be registered as a network adapter on infected systems, decrease your computer performance, and diminish your download and upload speed. The Loioir Trojan is known to use the names of popular PC games to hide its executable in the AppData folder and remain undetected.
Security scanners may detect the Loioir malware as DDoS:MSIL/Loioir and Trojan.MSIL.Loior. The Loioir Trojan may use a shadow instance of your default Internet client to launch a DDoS attack and download instructions from its 'Command and Control' server. The operators of the Loioir malware may use their botnet to earn money by offering DDoS attack on demand and bring down the servers of small businesses and large corporations alike. The Loioir malware is a modern day cyber threat that should not be underestimated. The Loioir botnet has the potential to keep targeted servers offline for as long as a month, and that may cost millions to international companies. As stated above, the Loioir malware may be registered as a network adapter and may feature an outdated digital certificate, which might help system administrators to find its main executable. Computer users that are infected with the Loioir malware should install a renowned anti-malware suite that can handle the removal of the Loioir Trojan for them.
Table of Contents
SpyHunter Detects & Remove Loioir
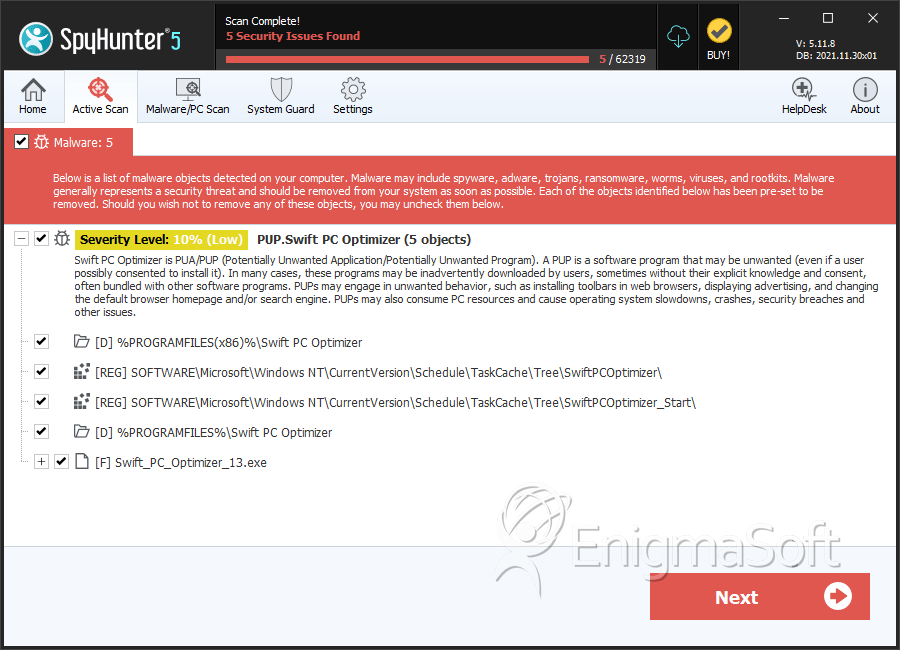
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | Swift_PC_Optimizer_13.exe | 3a9b746086c89e8808ea7406d7c977ee | 4 |
| 2. | %APPDATA%\lolclient\local store\cache.exe | ||
| 3. | %TEMP%\genx5.exe | ||
| 4. |
|
||
| 5. | Cb2rJvGOx3V6nsqxTBvJppp | ||
| 6. | Cb2rJvGOx3V6nsqxTBvJ |
Registry Details
Directories
Loioir may create the following directory or directories:
| %PROGRAMFILES%\Swift PC Optimizer |
| %PROGRAMFILES(x86)%\Swift PC Optimizer |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.