Kovter Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
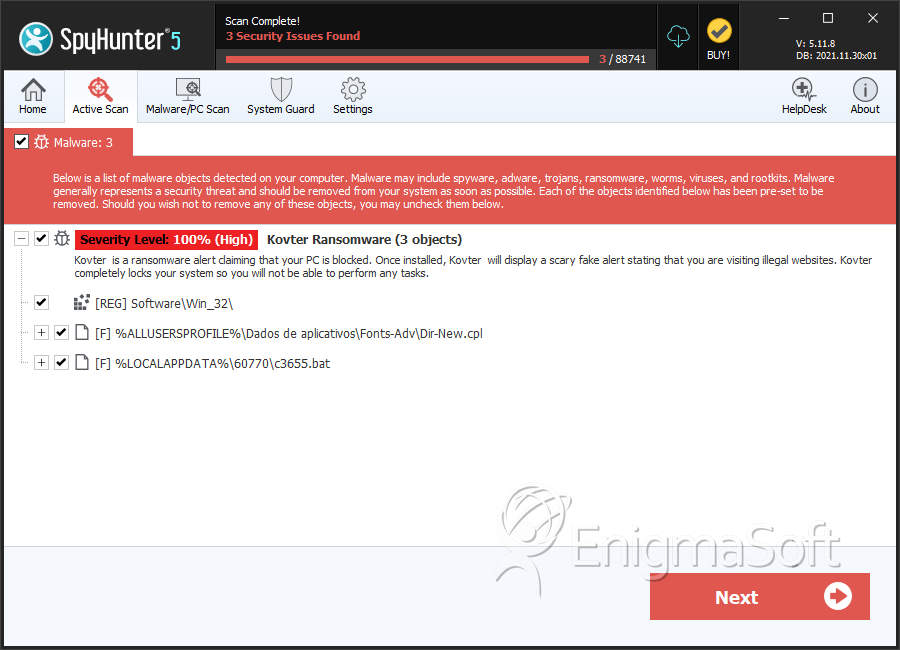
| Threat Level: | 100 % (High) |
| Infected Computers: | 56 |
| First Seen: | April 10, 2013 |
| Last Seen: | October 24, 2025 |
| OS(es) Affected: | Windows |
Kovter Ransomware Image
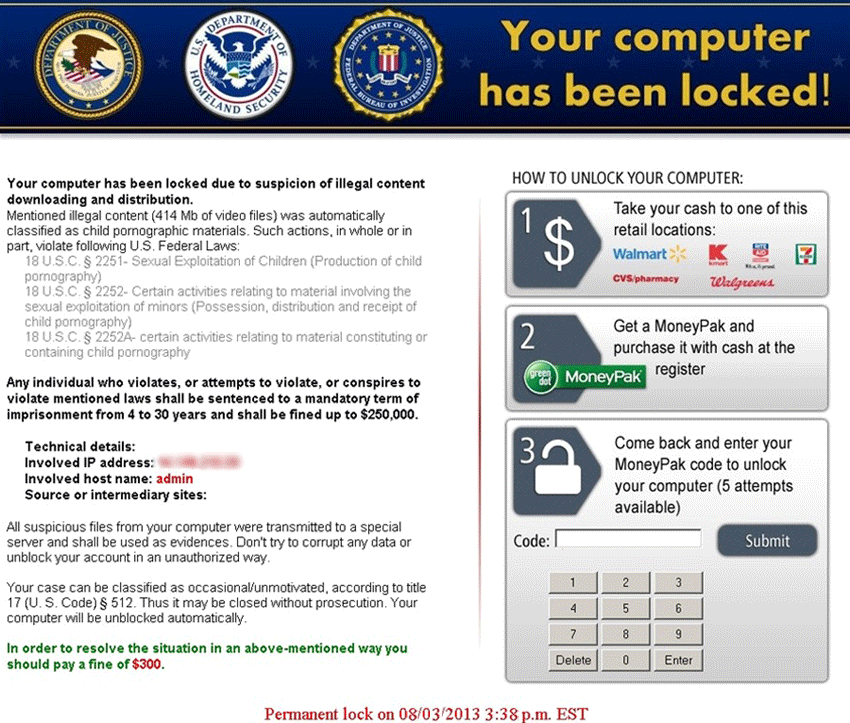
The Kovter Ransomware is a malware threat that carries out a common Police Ransomware scam in order to steal money from unsuspecting computer users. The Kovter Ransomware is a relatively new Police Ransomware Trojan, first detected in 2013 in the wild. Like most Police Trojans, the Kovter Ransomware displays a fake message from the police intending to trick the victim into paying a 'penalty' in order to stay away from jail time. Like other Police Rasomware, the Kovter Ransomware has a Winlocker component that allows the Kovter Ransomware to block access to the infected computer. However, the main reason why the Kovter Ransomware has attracted the scrutiny of malware researchers is because this malware infection uses a unique tactic in order to scare inexperienced computer users into parting with their money.
Table of Contents
The Kovter Ransomware Uses an Approach that Sets It Apart from Other, Similar Threats
One of the reasnos whythe Kovter Ransomware has quickly become a severe threat to computers is that the Kovter Ransomware collects data from the victim's Web browser that the Kovter Ransomware then uses to scam the computer user more effectively. Rather than displaying a generic message, like other Police Rasomware Trojans, the Kovter Ransomware can craft its message with data from the victim's online history and web browsing habits in order to scare the computer user with specific information in its Police Ransomware message. There's a Kovter Ransomware variant that displays a fake message from the United States Department of Homeland Security, the FBI and the United States Department of Justice. The messages claim that the victim had downloaded illegal content on the Internet and that the infected computer was used to distribute this content.
The main aspect of the Kovter Ransomware attack that sets the Kovter Ransomware apart from similar Police Ransomware threats is that its ransom message also includes data such as the victim's IP address and a URL that supposedly contains the 'illegal content' found on the victim's computer. The Kovter Ransomware scans the victim's web browser history for websites containing pornographic material. If a website in the Web browser's history matches one of the websites in this threat's list, the Kovter Ransomware will claim that the source of the illegal content was that particular website. Otherwise, the Kovter Ransomware chooses a pornographic website at random. Computer users that have visited websites with pornographic content may then be alarmed to find the website that they visited in the Kovter Ransomware's message, making this threat's message more believable.
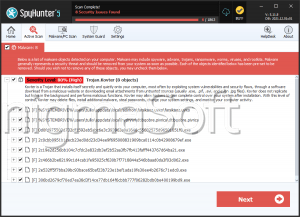
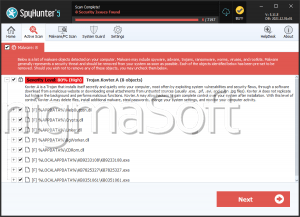
SpyHunter Detects & Remove Kovter Ransomware
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | Dir-New.cpl | 6a97e3cc5aee03350666d8749995c77d | 7 |
| 2. | c3655.bat | 3b1ed34a26477222dbddafc31b54fee9 | 1 |
| 3. | %LOCALAPPDATA%\KB[RANDOM NUMBER]\KB[RANDOM NUMBER].exe |