iSpy Keylogger
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 80 % (High) |
| Infected Computers: | 3 |
| First Seen: | October 19, 2016 |
| OS(es) Affected: | Windows |
PC security analysts are monitoring the iSpy Keylogger, a keylogger that is being distributed on the Dark Web. The iSpy Keylogger is available for anyone that wants to use it to carry out attacks for prices between $25 and $35 USD. The iSpy Keylogger is designed to collect passwords from the victims' Web browsers, record chats on Skype, take pictures using the victim's webcam, take screenshots of the victim's computer, and collect software license keys for programs like Microsoft Office and Adobe Photoshop. The iSpy Keylogger is being distributed using corrupted scripts on hijacked websites and corrupted email attachments contained in spam email messages.
Table of Contents
The iSpy Keylogger may Cause Huge Problems to Computer Users
The iSpy Keylogger has one unique characteristic: many versions of the iSpy Keylogger are signed with expired digital certificates to look legitimate, making it more difficult for some security programs to detect and intercept an iSpy Keylogger infection. There are several characteristics of the iSpy Keylogger: the iSpy Keylogger is delivered with a loader, which delivers a payload that is encrypted and compressed using .Net, Visual Basic 6.0 and AutoIT. The iSpy Keylogger loader has six specific components and several features. The following are features of the iSpy Keylogger:
- The iSpy Keylogger may monitor the infected computer's clipboard, monitoring content that the victim copies or cuts.
- The iSpy Keylogger monitors the victim's webcam and is able to take pictures using the infected computer's camera.
- The iSpy Keylogger may monitor the victim's keystrokes, collecting data that is typed into the infected computer.
- Curiously, the iSpy Keylogger will look for PINs belonging to RuneScape, a well-known multiplayer online game.
- The iSpy Keylogger will take screenshots, taking pictures of what the victim views on the infected computer's screen.
- The iSpy Keylogger is capable of collecting passwords typed in the infected computer.
The latest versions of the iSpy Keylogger have included an additional feature, which makes it capable of recording chats carried out on Skype. The iSpy Keylogger also has a feature that allows it to delete and block warning messages that may appear on infected computers.
How the Con Artists may Buy and Sell the iSpy Keylogger and Similar Threats
The iSpy Keylogger is sold on the Dark Web via subscription. Con artists distributing the iSpy Keylogger provide three different subscription tiers, depending on what the con artists are planning on doing with the iSpy Keylogger. Some versions of the iSpy Keylogger have the ability to terminate anti-virus software and relay data using a variety of protocols when communicating with its Command and Control server. The iSpy Keylogger uses a custom encryption method to send the collected data to its Command and Control server. The latest samples analyzed use FTP to deliver the collected data. Con artists may subscribe to the iSpy Keylogger for one month, six months, or a full year, with the prices for each being $25, $35 and $45 USD respectively. The free availability of threats like the iSpy Keylogger makes this threat infection and similar threats particularly threatening. Anyone can purchase the iSpy Keylogger as long as they have the money and access to the Dark Web. This puts a devastating threat attack in the hands of potential con artists that don't need a particularly advanced knowledge of threats.
Preventing an iSpy Keylogger Attack
PC security researchers strongly advise computer users to use a reliable security application that is fully up-to-date to protect their computers. Make sure that all security updates are applied regularly, especially since the newest versions of the iSpy Keylogger are updated constantly to evade or disable threats. Since the iSpy Keylogger may be distributed by using corrupted email messages or hijacked websites, PC security analysts strongly advise computer users to take precautions when browsing the Web. To prevent these infections, computer users need to be educated about handling sensitive material online.
SpyHunter Detects & Remove iSpy Keylogger
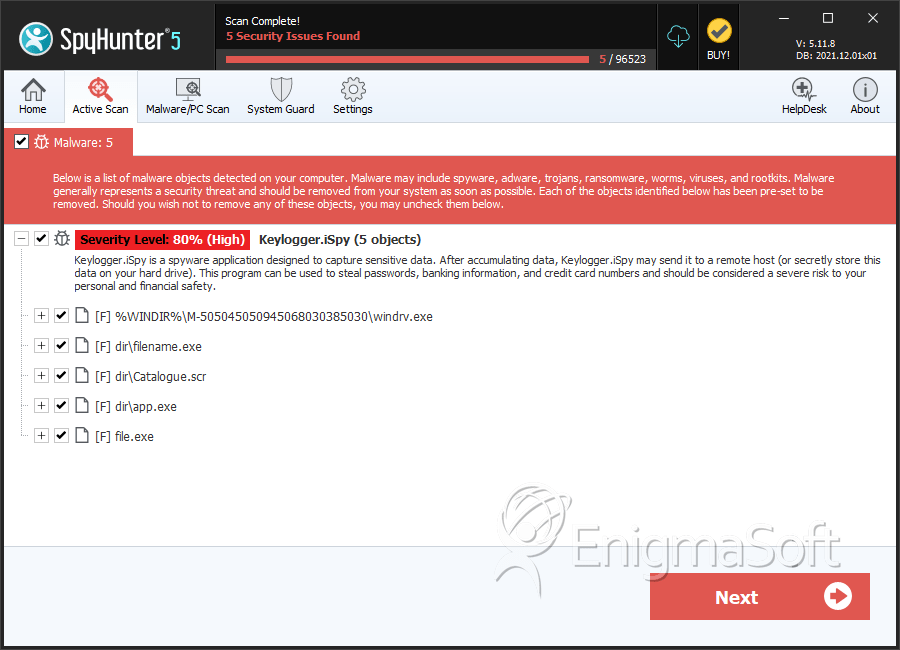
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | windrv.exe | 2b8e2d23c88b11bbcf59928d5d440bdb | 3 |
| 2. | filename.exe | 51981d91472c00a78a6358cc2d5ff47f | 0 |
| 3. | filename.exe | ca66771aaaf3e6b4be57f09d9cfabcc1 | 0 |
| 4. | Catalogue.scr | c17dad76326700c24daef882e8550be4 | 0 |
| 5. | app.exe | 9373eb008dd45458d424ce928b8d4475 | 0 |
| 6. | filename.exe | b99491b53faabb559adf42d6156d9dad | 0 |
| 7. | file.exe | 45e1b7642f8bdc7fb92cac05866d6114 | 0 |
| 8. | file.exe | 76a860f17061acb0ecf2835d9acba1c0 | 0 |
| 9. | file.exe | aa2087f75fdfc11bab85308c706d848e | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.