Infostealer.Jginko
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 90 % (High) |
| Infected Computers: | 2,982 |
| First Seen: | September 29, 2011 |
| Last Seen: | August 26, 2022 |
| OS(es) Affected: | Windows |
The Infostealer.Jginko virus was created in 2005 as part of a phishing scam. Originally designed to steal banking information from computer users in Japan, this virus has returned in 2011. Infostealer.Jginko is back in the wild, stealing bank account information from Japanese victims. ESG security researchers have observed that bands of computer criminals have turned to Infostealer.Jginko, as a way to attack their victims. While Infostealer.Jginko has not been used often since Infostealer.Jginko's heyday in 2005, Infostealer.Jginko is just as effective as ever. A computer with an Infostealer.Jginko virus infection will turn over banking information to computer criminals.
Table of Contents
How the Infostealer.Jginko Virus Spreads
Most computer users infected with the Infostealer.Jginko virus received their infection from an infected email, containing a malicious attachment corrupted by Infostealer.Jginko. This email tricks the person receiving it by pretending to come from one of the major Japanese banks. However, checking the sender's address, one discovers that it is not an address that is authorized by this Japanese financial institution but was, rather, created by computer criminals. This email will usually notify the victim that it is necessary to renew or receive a code card from the corresponding bank. These code cards are legitimate banking instruments designed for carrying out transactions on the Internet. These code cards are designed to protect their holders from credit card fraud or identity theft, as well as for making Internet transactions as safe as possible. The problem is that, now, computer criminals have taken advantage of these cards to commit fraud. The email sent out by these criminals will claim that the victim must open the attachment to learn the proper procedure for renewing their code cards. This email takes them to an online form, in which their bank account information will be requested. Like most phishing scams, this form is not real. The Infostealer.Jginko records all of the victim's answers and takes a screenshot, which Infostealer.Jginko then sends to a specific Internet address, so that the hackers can gain access to it. The website associated with the Infostealer.Jginko virus is routinely cleaned and the data gathered and erased.
Preventing Infostealer.Jginko Attacks
The Japanese financial institutions that have become involved in this phishing scam have now issued warnings against Infostealer.Jginko. The main way to prevent the theft of one's banking information is to be extremely careful when opening email attachments. It is also important to understand that no serious banking institution will ever ask their costumers to enter their personal identification numbers and sensitive information this way. If you receive emails or phone calls supposedly from your bank asking for this information, you can be sure that you are being scammed.
SpyHunter Detects & Remove Infostealer.Jginko
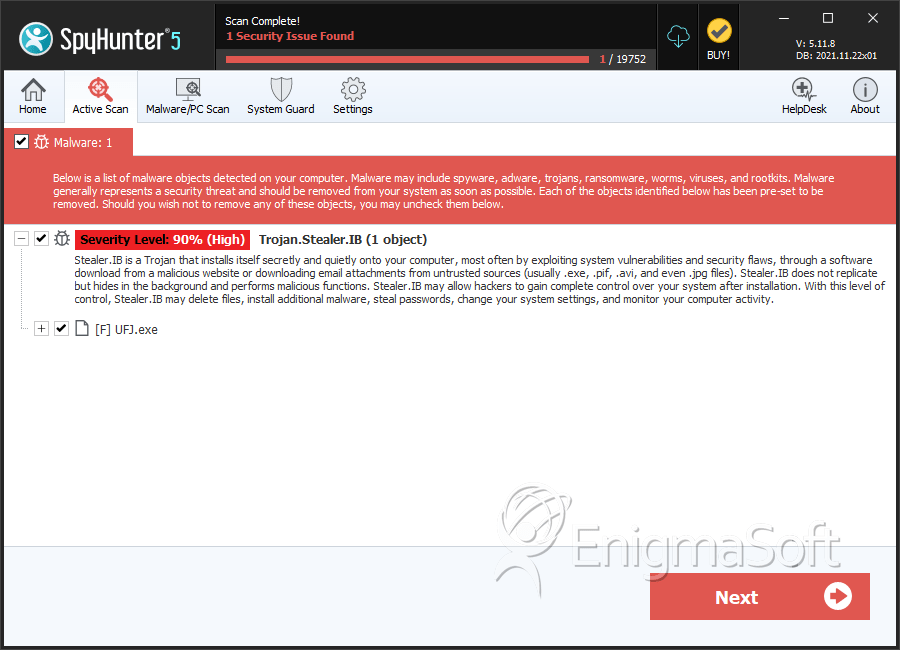
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | C:\system.exe | ||
| 2. | UFJ.exe | 65d03ab7d61aa0844e86ca797a97968a | 0 |
| 3. | UFJ.exe | 5b57d402a27c2903e106b300fe69e2e7 | 0 |
| 4. | UFJ.exe | bf45f320ccbfd8ccc7815d6004b5c953 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.