Information Security And Control Act 2012 Ransomware
Information Security And Control Act 2012 Ransomware Image
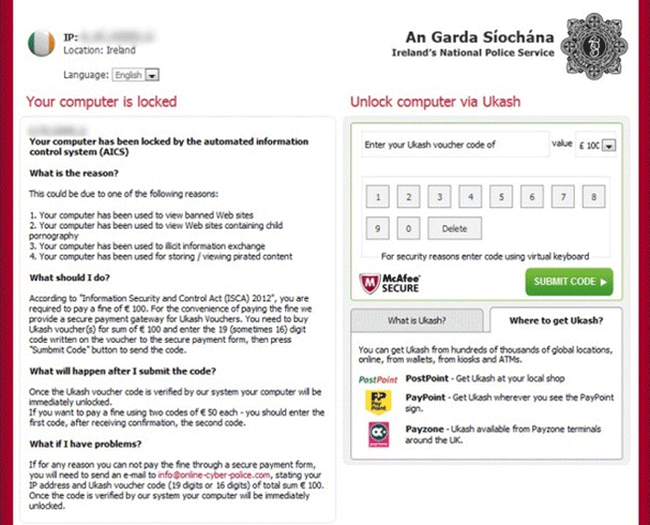
The Information Security and Control Act (ISCA) 2012 ransomware infection is part of a wave of ransomware threats that have started to target computers in North America. Although these kinds of threats were more common in Europe in 2011, towards the summer of 2012 PC security researchers observed a marked rise of ransomware infections targeting computers in Canada and the United States. Pretending to display messages from organizations such as the FBI and the Canadian Mounted Police, these ransomware threats carry out variations on the same scam. Information Security and Control Act (ISCA) 2012 ransomware is designed to block access to the infected computer, effectively taking it hostage until a ransom is paid via a money transfer service. If your computer is blocked because of this fake message from the Information Security and Control Act (ISCA) 2012 ransomware infection, you should avoid paying this threat's fine. Instead, this malware threat can be annihilated with the aid of a responsible anti-malware program.
Despite the fact that the Information Security and Control Act (ISCA) 2012 ransomware message claims to be an official communique from law enforcement, it is actually caused by a Trojan infection. This Trojan makes changes to the Windows Registry that prevents the victim from accessing their own files and programs. Although the Information Security and Control Act (ISCA) 2012 ransomware message claims that the victim's computer was blocked because it violated laws pertaining to copyright protection and intellectual property, it is actually a scam to threaten computer users so that they will pay a nonexistent fine. Ransomware threats similar to the Information Security and Control Act (ISCA) 2012 ransomware are quite common and relatively easy to remove. Because of this, ESG security researchers strongly recommend against paying the fine demanded in this fraudulent message.
Dealing with an Information Security and Control Act (ISCA) 2012 Ransomware Infection
The main obstacle in removing an Information Security and Control Act (ISCA) 2012 ransomware infection is actually managing to gain access to anti-malware software installed on the infected computer. Fortunately, Windows allows computer users to start up in Safe Mode by pressing the F8 key on their keyboard while their computer starts up. Via the Command Prompt, it is somewhat easy to obtain access to the Windows Registry (for advanced computer users removing the Information Security and Control Act (ISCA) 2012 ransomware infection manually) or to your anti-malware software of choice for automatic removal of this ransomware threat.
File System Details
| # | File Name |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|
| 1. | %AppData%\[rnd].exe |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.