Hancitor
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 80 % (High) |
| Infected Computers: | 46 |
| First Seen: | August 11, 2016 |
| Last Seen: | February 25, 2022 |
| OS(es) Affected: | Windows |
Trojan downloaders have been growing in popularity in the world of the cybercrime. Among the most popular ones is Hancitor – despite it not being among the top-tier of its class, this vicious Trojan downloader makes up in its vast methods of propagation. Hancitor has been spread far and wide by cyber crooks around the globe and has proven to be very effective. This Trojan downloader has been observed to involve spreading info stealers and banking Trojans mainly.
The main propagation method of Hancitor is via spam email campaigns. The attackers use a rich variety of email templates for their spam campaigns, and also may switch between two delivery methods – a macro-laced document as an attachment or urging the user to download the corrupted document from an external server.
Earlier campaigns employed the first method. Usually, the infected file will be in the form of a .rar or .zip archive. Often, the attackers would use social engineering tactics and try to trick the victim into opening their attachment. Such methods are disguising the file as a delivery update from shopping websites such as eBay and Amazon, a PayPal statement, or other fraudulent documents attached, masked as legitimate files.
Later on, the propagators of Hancitor started using a new method. Instead of attaching a macro-laced file they would attempt to pressure users into clicking a link that would lead them to a file hosted on an external server. Again, they would use the names of companies such as PayPal and Amazon in an attempt to make their scam seem more legitimate.
It would seem that people who use Windows 7 and Windows XP are the ones most susceptible to Hancitor. That does not mean that users with different operating systems need not worry. The best practice, in this case, is to keep all your software up to date, especially your Microsoft Office packages as they have been observed to be exploited by Hancitor specifically.
The shady individuals behind Hancitor are hosting hundreds of servers worldwide, which come to show us how large-scale this operation is. Only in the United States, there are over 180 servers, which are propagating Hancitor. There have also been servers detected in Japan, India, Thailand, Ireland and South Africa among other countries.
If you want to stay safe, you need to remember that threats like Hancitor exploit vulnerabilities in outdated software and as tedious as it may be to update all the software on your PC it is better than having to deal with a pain in the backside like Hancitor.
Table of Contents
SpyHunter Detects & Remove Hancitor
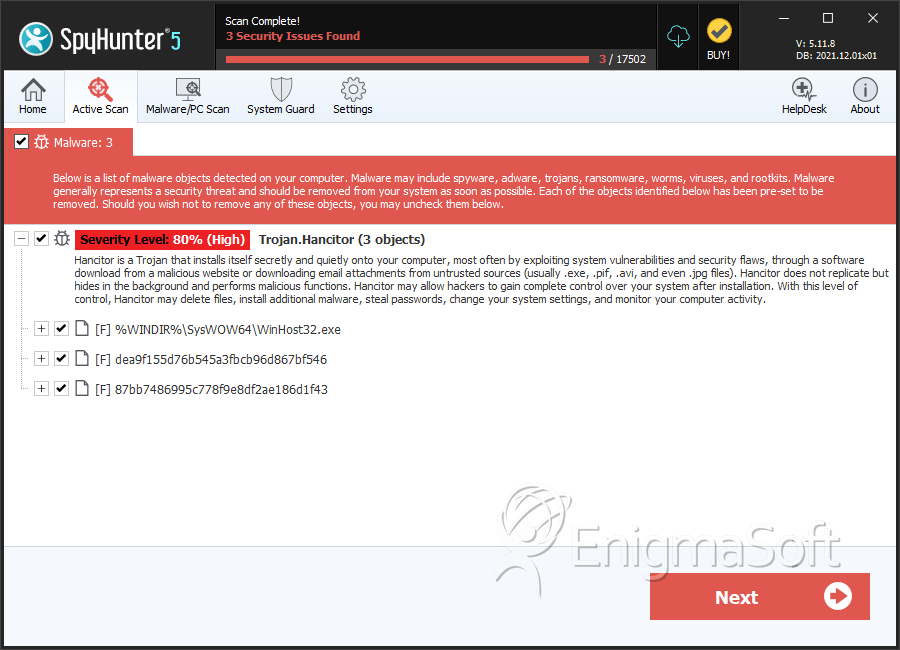
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | winhost32.exe | 7ac797edd9a7a14a48096b3ca6fbdd27 | 1 |
| 2. | WinHost32.exe | 3d3397d4b612cba1ae6961dea285e480 | 0 |
| 3. | dea9f155d76b545a3fbcb96d867bf546 | dea9f155d76b545a3fbcb96d867bf546 | 0 |
| 4. | 87bb7486995c778f9e8df2ae186d1f43 | 87bb7486995c778f9e8df2ae186d1f43 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.