Hackers Leveraging Coronavirus are Spreading Emotet Malware Campaigns in Japan
 The World Health Organization (WHO) announced a public health emergency for the COVID-2019 pandemic back in January 2020. Unfortunately, hackers and threat actors across the globe are taking advantage of the chaos and fears of the populace to continue their nefarious deeds unabated. An Emotet malware spam campaign has been reported targeting the people of Japan, focused on the Osaka, Gifu, and Totori prefectures. The spam emails are disguised as official notifications about the coronavirus, allegedly coming from disability welfare service providers and public health centers.
The World Health Organization (WHO) announced a public health emergency for the COVID-2019 pandemic back in January 2020. Unfortunately, hackers and threat actors across the globe are taking advantage of the chaos and fears of the populace to continue their nefarious deeds unabated. An Emotet malware spam campaign has been reported targeting the people of Japan, focused on the Osaka, Gifu, and Totori prefectures. The spam emails are disguised as official notifications about the coronavirus, allegedly coming from disability welfare service providers and public health centers.
Table of Contents
Security Researchers on the Emotet Malspam Campaign
Analysts from Kaspersky and IBM X-Force, alongside infosec community experts, managed to find out that Emotet operators were using previously compromised account templates targeting victims of the Emotet malware spam campaign.
IBM researchers reported the attackers to appear to be focusing on geo-targeting their emails and language to spread fear in specific areas. That leads to more clicks on malicious attachments and emails by panicked users. One of the malspam emails mentioned that the coronavirus infection was detected in Gifu prefecture in Japan; another mentions Osaka. For a more legit look, spam emails have phone and fax numbers of actual welfare service providers and public health centers in those areas.
This Week In Malware Ep 12: IC3 Warns Coronavirus-Related Cyber Threats Have Reached Alarming Rates
How does the Emotet Malspam Campaign Work?
Each of the malspam emails contains a warning note attempting to push users to take action. That is done by downloading a malicious Word document attachment that contains the Emotet malspam. The document claims to have precautionary health measures and the latest updates with information related to the coronavirus. Upon opening the infected attachment and enabling macros within Office 365, an obfuscated VBA macro script begins work in the background. It installs a Powershell script that downloads the Emotet malware. Emotet also downloads more malicious payloads that work to extract more data from any compromised systems.
When did Emotet first make an appearance?
Emotet is a malware and cybercrime operation working under the same name. The malware is also known under the monikers Mealybug and Geodo. It was first detected back in 2014 and has been active ever since, used in various campaigns. The first versions of the malware acted as a banking Trojan, working on stealing banking credentials. Emotet operators began to change it later on, making it an initial point of infection for more payloads. Second stage infections may include Emotet modules, to more malware developed for the purpose of cyber crime.
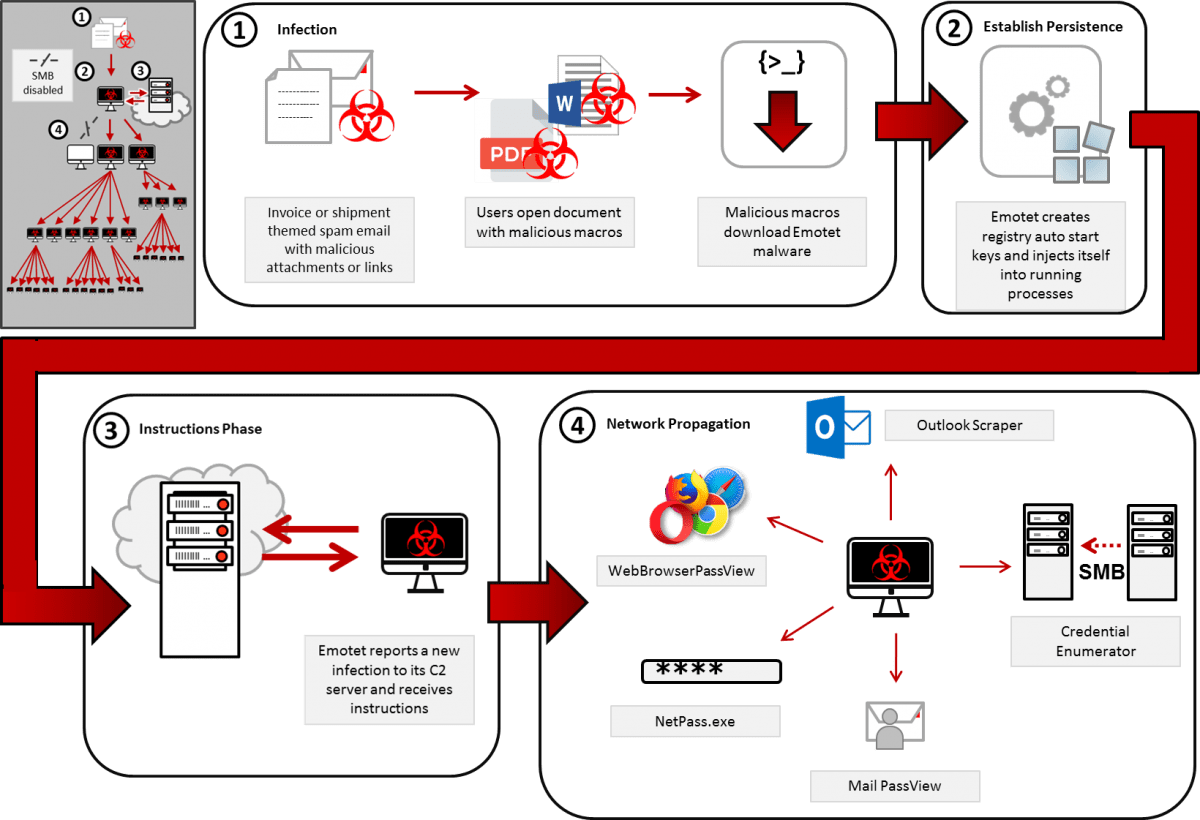
The Emotet infection process; Source: Cybersecurity and Infrastructure Security Agency (CISA)
Security researchers encountered an Emotet campaign riding on environmental activist Greta Thunberg's fame to spread across computers in Europe and Asia. Using the popularity of Thunberg among students, the campaign using the Trojan used her name to target domains using the .com and .edu extensions. The attackers also targeted European and Asian countries, then expanding their campaign to Australia and the United States.
According to Proofpoint and ExecuteMalware researchers, these emails looked like an invite from Greta Thunberg to a climate change summit or a demonstration with emails containing subject lines like "I invite you" and "Demonstration 2019". The emails also asked to share the message with family and friends.