Grandoreiro
Remote banking Trojans that display bogus overlays are very popular threats in South America. The first mass campaigns involving this malware type were detected by cybersecurity researchers in 2014. Ever since 2014, cybercriminals have been launching an increasing number of campaigns of this kind. Among the latest threats of this type is the Grandoreiro malware.
The Grandoreiro threat has two main components:
- A browser extension, which collects information about the user – browsing history, system settings and cookies.
- A remote access module, which serves to provide the operators of the threat with access to the user's Web browser. This module allows the attackers to interact with the browser in question.
According to malware experts, the Grandoreiro threat is being propagated via fraudulent document files. The attackers would tailor the fake files to appear like important documents that need to be reviewed as soon as possible – invoices, tracking details, job offers, etc. To make the bogus documents appear as legitimate files, the attackers use the double extension trick. Many cyber crooks use this trick because Windows hides files' extensions automatically. This means that the user would receive a file that appears to be a regular '.docx' file, when in fact it is a '.msi' file. For example, a file, whose real name is 'CV.docx.msi' would appear as 'CV.docx' on the victim's computer.
Once the Grandoreiro malware infiltrates the targeted computer, it will drop its files in various system directories. Next, to gain persistence, the Grandoreiro malware will alter the system's Windows Registry. The second module of the Grandoreiro threat will be planted in a separate folder on the user's system. Next, the Grandoreiro malware will make sure to create a Google Chrome shortcut that utilizes a specific parameter, which serves to load the corrupted extension manually. All the Google Chrome shortcuts on the user's system will be replaced with a fake copy, which would ensure that whenever the users want to open their browser, they will use one of the bogus variants created by the Grandoreiro threat.
The fake Web browser extension serves to gather data regarding the online activity of the victim:
- Clipboard activity.
- Browser history.
- System settings.
- Notification permissions.
The Grandoreiro malware will observe the URL that is active in the user's browser to detect whether the victim is attempting to access a banking portal. If such activity is detected, the Grandoreiro threat will connect to the C&C (Command & Control) server of the attackers. In this stage of the attack, the victim will likely be presented with carefully tailored overlays and bogus prompts that have one goal – to phish the user's login credentials and banking information. Needless to say, this cyber attack may be very devastating and cause huge financial losses for the victim.
Table of Contents
What is a Remote Overlay Trojan?
Remote overlay trojans are a disturbing trend in Latin America. These trojans are simple but effective and have been popular in Brazil since at least 2014. The attacks are becoming more and more common, with remote overlay trojans considered the most significant financial malware threat for Latin America.
There are plenty of different remote-overlay trojans out in the wild, but they all have similar codes. There are some small differences between them, mostly in how they are deployed and how they infect target computers.
Users are typically infected through spam emails, phishing pages, and malicious file attachments. The malware quickly gets into action once it is installed on a system. Grandoreiro responds once the user connects to a list of entities encoded into it, most of which are local banks in the target area.
Grandoreiro notifies the attacker when the computer accesses a target website. The attacker has remote access to the device. Attackers display an overlay image designed to look just like the real website for the bank. The overlay can prevent users from accessing the site so the attacker can move money, or they have other data fields that victims are prompted to complete to garner extra information.
Attackers conduct fraudulent money transfers in the background, obtaining any information needed to complete the process from the user in real-time.
How Does Grandoreiro Spread?
Researchers who looked into Grandoreiro suggest that it spreads through malspam campaigns. The campaigns leverage a URL that sends users to a website where the virus strikes. The initial infection stage is a loader component. Grandoreiro uses fake invoices in a GitHub repository to get on computers. From there, the loader runs a code to download the payload for Grandoreiro.
The Grandoreiro executable is a standalone dropper at first, but it creates a run key based on where it was executed after running. An example of this key is shown below;
![]()
Grandoreiro run key
Creating Fake Extensions
The virus sample used by the researchers ran for about six minutes before causing an abrupt restart on the infected machine. The malware creates an archive file called ext.zip that contains additional files after this restart. The extra files from the archive are placed in a directory under C:/%user%/*extension folder*/*.
The files from the archive are a modified version of Edit This Cookie, which is a legitimate Google Chrome extension. The dropper then creates a new .link or shortcut file for the Chrome browser. If the shortcut already exists, then the dropper replaces the one that already exists.
This new Chrome shortcut contains a new “- load-extension” parameter that tells Chrome to load the malicious extension upon launch automatically.
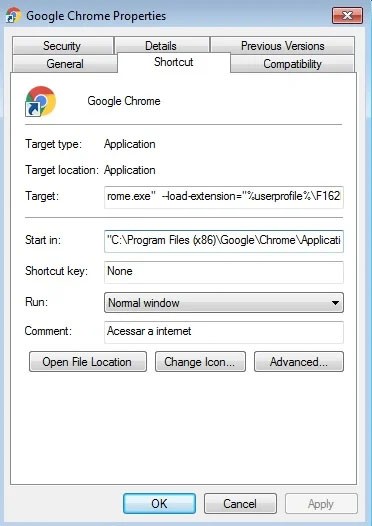
Fake browser extension
If users were already running Chrome when the infection began, Grandoreiro forces Chrome to shut down. By doing this, the malware forces users to re-open Chrome using the malicious shortcut loaded with the fake Grandoreiro extension. The extension loads every time the browser is started with the specific .lnk file created by Grandoreiro.
The creator behind the malicious extension named it “Google Plugin” version 1.5.0 in an attempt to make it appear more genuine. The extension itself adds a new square button to the web browser rather than the “cookie” button of the original Edit This Cookie plugin.
On the surface, the extension asks for permission to access browsing history, display notifications, and modify data a user copies and pastes. Under the surface, though, the extension gains access to all kinds of things, including navigation, tabs, context menus, storage, and web requests.
Once the extension has been deployed, the dropper creates three new files under %appdata%/local/*/:
- EXT.dat
- RB.dat
- EML.dat
Grandoreiro monitors the status of the EXT.dat file and re-creates it when the user removes it from the computer.
The attacker uses the extension to collect all sorts of information about victims from their cookies. This information includes things such as the URL, name, value, and even password and credit card information.
Researchers believe that the attacker grabs cookies and uses the information from them to ride the active session on another device. Basically, the attacker disguises themselves as the user on their own devices, allowing them to act without the need to control the target computer directly.
There are some signs that this strain of Grandoreiro is connected to the original Brazillian version. One of these signs is that some of the data is written in Portuguese. Another clear indication of the connection is that the default locale of the extension is “pt_BR” or Portuguese_Brazil.
Grandoreiro Monitors Victims
Grandoreiro sits quietly in the background of an infected computer until the user does something to trigger it. Actions that trigger Grandoreiro include visiting one of the many banks coded into the extension. When triggered, the malware activates the remote-access features to engage with victims in real-time. The malware displays images on their screen that trick users into keeping their session running. These fake screens also help an attacker to collect information from the victim to conduct their attack.
As with most remote-overlay trojans, the images are made to look like the regular interface for the target bank. Attackers launch these images in real-time for the most effective attacks. Victims don’t realize that anything is happening until it is too late.
Simple But Effective Banking Malware
Grandoreiro is one of many banking trojans in the wild. These trojans are popular with attackers from all around the world. Banking trojans allow hackers to access the bank accounts of victims through infecting devices used to access online banking.
On the global level, major hacking groups use sophisticated trojans like TrickBot to affect large banks across the countries. There’s a real difference between those kinds of schemes and the ones seen in Latin America, and in other places where the language barriers restrict who can operate in an area – such as Spanish and Portuguese speaking countries outside of Latin America.
These regions see a lot of simple but effective malware. The malware here is so simple that anyone can use them, targeting businesses and consumers alike. While the malware is simple in nature, it still allows for an attacker to take over a target device and trick victims in real-time. Being simple doesn’t make this malware any less dangerous than their sophisticated cousins.

