GoldenSpy
 Malware experts have identified a new threat, which has been dubbed GoldenSpy. According to analysts, there have been two companies that have been breached so far. Both organizations are located in the United Kingdom. One of the affected companies is involved in software development, while the other one operates in the financial sector. What is very intriguing about the GoldenSpy malware is that it was delivered to the targets via a taxation software that was presented as legitimate by a Chinese bank. The bank in question required the affected companies to install the dodgy software. It is unknown if the bank was aware that the taxation software they required their partners to install carried the payload of the GoldenSpy malware.
Malware experts have identified a new threat, which has been dubbed GoldenSpy. According to analysts, there have been two companies that have been breached so far. Both organizations are located in the United Kingdom. One of the affected companies is involved in software development, while the other one operates in the financial sector. What is very intriguing about the GoldenSpy malware is that it was delivered to the targets via a taxation software that was presented as legitimate by a Chinese bank. The bank in question required the affected companies to install the dodgy software. It is unknown if the bank was aware that the taxation software they required their partners to install carried the payload of the GoldenSpy malware.
GoldenSpy essentially comes from a family of malware called GoldenHelper. Within the GoldenHelper family of threats, GoldenSpy is one of many components that is found embedded within Chinese tax software. The Trustwave SpiderLabs cybersecurity firm have uncovered many aspects about GoldenSpy and the GoldenHelper malware family where common DLL, EXE, and even DAT system files are leveraged in a way to hide the infection on a Windows computer.
The processes path demonstrated below is an example of the GoldenHelper's malware going through its functions, delivery, and ultimately its installation process flow.
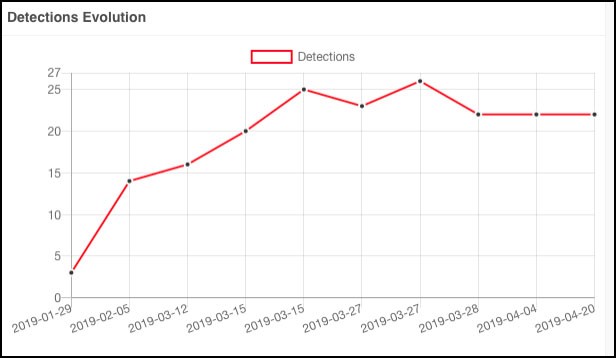
GoldenSpy (GoldenHelp) Wmiasssrv.dll system file detection rates - Source: Trustwave
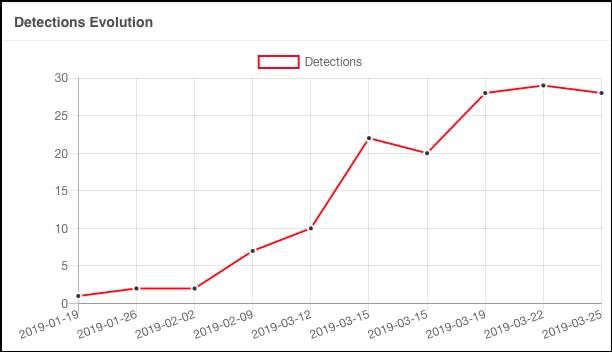
GoldenSpy (GoldenHelp) random DLL system file detection rates - Source: Trustwave
Trustwave also demonstrated how some of GoldenHelper's (GoldenSpy's) random DLL files grew in detection throughout the months of March and April of 2019. Today, it is believed that GoldenSpy remains active and may leverage other system files to evade detection and proliferate in undercover methods.
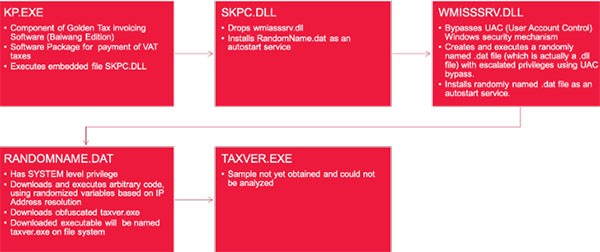
GoldenSpy (GoldenHelp) system file process flow - Source: Trustwave
Table of Contents
GoldenSpy’s Reach is Vast Among Chinese Companies
In late July 2020, the FBI sent out a stern warning of the backdoor malware that is being loaded through networks of companies that operate in China through government mandated tax software. The companies that are forced to utilize the tax software is tasked with handling the value-added tax (VAT) payments to the Chinese tax authority, which possess a great risk to all who have loaded the software essentially expanding the risk of GoldenSpy to become a serious problem.
The Chinese government requires companies to install tax software that happens to be associated with GoldenSpy, which has prompted the FBI to warn of the threat. - Source: ZDNet
The known operation of backdoor threats is to load without any indication to the computer user or network administrator, further making the proliferation of GoldenSpy a mounting issue that could result in the theft of proprietary data from companies in China. Such companies that are affected by GoldenSpy or the family of GoldenHelper threats could do business in other countries, which may become a problem outside of the scope of China.
The Operations of GoldenSpy are Relentless
The GoldenSpy threat serves the purpose of a backdoor Trojan. Once the GoldenSpy malware has compromised a targeted system, it will allow its operators to execute additional files on the host, as well as run remote commands. Upon installing the shady taxation software, the GoldenSpy malware will also be planted on the host. It takes no longer than two hours for the dodgy application to inject the payload of the GoldenSpy malware on the host. Next, the GoldenSpy Trojan will make sure to gain persistence on the host by spawning two copies of its payload and setting up two services, which are programmed to run whenever the infiltrated system is rebooted. This nasty threat also will gain administrator permissions, which will allow it to have almost full control over the breached system. If the user removes one of the copies of the threat, the other one will inject a new payload immediately. Unfortunately, uninstalling the dubious taxation software will not help you rid yourself of the GoldenSpy Trojan.
The taxver.exe file has been found by computer security researchers from Trustwave as being an executable file associated with GoldenSpy that will covertly download and run a final payload with system-level privileges. Such privileges could give GoldenSpy unadulterated access to certain areas of an infected system to identify network traffic and perform malicious actions at the optimal time for the best effect on the computer. Other notable files include the Skpc.dll dynamic link library files that has multiple variations, some that do not indicate the containing of malicious artifacts, according to Trustwave’s findings.
Among files that are associated with GoldenSpy, researchers have uncovered several variations of files as listed below:
- %ALLUSERPROFILE%"\taxver.exe
- %COMMONPROGRAMFILES%"\taxver.exe
- %WINDIR%"\debug\taxver.exe
- %WINDIR%"\debug\wia\taxver.exe
- %WINDIR%"\taxver.exe
- %WINDIR%\system32\taxver.exe
- JSKP_BWB_1.0.4.0.exe
- msxxxs999.dat
- Skpc.dll – MD5: 490d17a5b016f3abc14cc57f955b49b3
- Skpc.dll – MD5: 9e2ebdbc9ba4dca69a712e3268f3ab77
- Skpc.dll – MD5: fbb35e8f16e7d5a735f06ae03e8bfaac
- Skpc.dll – MD5: 61eed90b1ae70244cd87a3abd3ec622a
- Skpc.dll – MD5: d312336fd46972a544929d0dc4e07b83
- Skpc.dll – MD5: 27d448f9d2bed761e15541c55b5966f2
- Skpc.dll – MD5: 471c75acc284396354c89616f9030718
- Wmiasssrv.dll – MD5: 682a0826db8572bad205a4db12005e13
- Wmiasssrv.dll – MD5: 26e71f1d387298162c1b19e858d001a1
What makes the GoldenSpy malware so threatening is that the targets may not realize that there is something shady taking place on their systems since the threat was delivered by what appeared to be a legitimate application recommended by a trustworthy partner. Both the infection vector and the Trojan itself are very complex and point to an experienced and highly-skilled group of cybercriminals. We will likely hear about more businesses and organizations targeted by the GoldenSpy threat in the future.
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | %WINDIR%\system32\taxver.exe | ||
| 2. | %WINDIR%"\debug\wia\taxver.exe | ||
| 3. | %WINDIR%"\debug\taxver.exe | ||
| 4. | %WINDIR%"\taxver.exe | ||
| 5. | %ALLUSERPROFILE%"\taxver.exe | ||
| 6. | %COMMONPROGRAMFILES%"\taxver.exe | ||
| 7. | msxxxs999.dat | 490d17a5b016f3abc14cc57f955b49b3 | |
| 8. | Wmiasssrv.dll | 682a0826db8572bad205a4db12005e13 | |
| 9. | Wmiasssrv.dll | 26e71f1d387298162c1b19e858d001a1 | |
| 10. | Skpc.dll | 9e2ebdbc9ba4dca69a712e3268f3ab77 | |
| 11. | Skpc.dll | fbb35e8f16e7d5a735f06ae03e8bfaac | |
| 12. | Skpc.dll | 61eed90b1ae70244cd87a3abd3ec622a | |
| 13. | Skpc.dll | d312336fd46972a544929d0dc4e07b83 | |
| 14. | Skpc.dll | 27d448f9d2bed761e15541c55b5966f2 | |
| 15. | Skpc.dll | bee06d785b7e51a0127a96c5854d4345 | |
| 16. | Skpc.dll | 471c75acc284396354c89616f9030718 | |
| 17. | JSKP_BWB_1.0.4.0.exe |
URLs
GoldenSpy may call the following URLs:
| bbs.tax-helper.info |
| download.tax-helper.com |
| inf.tax-assistant.com |
| info.tax-assistant.com |
| info.tax-assistant.info |
| info.tax-helper.ltd |
| tax-assistant.com |
| tax-assistant.info |
| tax-helper.ltd |
| tip.tax-helper.ltd |
| tools.tax-helper.info |
| update.tax-helper.com |
| update.tax-helper.ltd |

