Godzilla Loader
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 80 % (High) |
| Infected Computers: | 6 |
| First Seen: | April 7, 2017 |
| Last Seen: | September 21, 2022 |
| OS(es) Affected: | Windows |
Nowadays, it has become very easy to be a cybercriminal. Although it would be easier to operate any malware if you have the required technical knowledge certainly, one does not need to have any experience in programming necessarily. An increasing number of cyber crooks are selling their hacking tools on forums online. Anything from RaaS (Ransomware as a Service) to RATs (Remote Access Trojans) and various loaders. As long as you are willing to pay good money, you can become a cybercriminal with very little effort.
A particular offer has been picking up steam recently. It is about a hacking tool named the Godzilla Loader. The authors of this tool are selling it for $500. Although this may seem like a bit of a steep price, the creators of the Godzilla Loader promise their clients regular updates with the possibility of new features being added. The main purpose of the periodical updates is to ensure that the Godzilla Loader will continue to stay under the radar of anti-malware applications. Despite its seemingly high price, the Godzilla Loader is far from expensive when you compare it to the more popular tools of this kind that are on the market, like the Emotet Trojan for example.
The creators of the Godzilla Loader state that their threat is written in the C programming language. They also claim that the Godzilla Loader sports a wide variety of features, which would enable it to avoid detection from anti-virus applications and take advantage of known vulnerabilities in some Windows features. Furthermore, the Godzilla Loader supposedly has a very user-friendly control panel via which the users would be able to control and monitor the activities of this loader.
The User Account Control (UAC) WIndows security feature was introduced back when Windows Vista was released, and it has undergone a lot of improvements since then. Unfortunately, it is far from enough to stop malware when there are multiple known exploits to bypass this basic security feature, especially. Of course, the Godzilla Loader is not any different, and it will use one of the popular vulnerabilities to bypass UAC.
The executable file of the Godzilla Loader is very small in size - just 15KB. This would allow it to be obfuscated in the code and therefore, easily avoid detection. Furthermore, the Godzilla Loader exploits a particular vulnerability found in Windows 10, which allows it to run its harmful payload with all administrative privileges.
The communication between the Godzilla Loader and the Command & Control server is protected via an RSA-2048 key that is required for authentication. This way, no-one but the attacker would be able to control the active Godzilla Loader instances in case the command server gets hijacked.
In case the client intends to spread ransomware via the Godzilla Loader, this hacking tool also is capable of wiping out the Shadow Volume Copies on the infected host, making it almost impossible to retrieve any data after the encryption.
To make sure you stay safe from threat actors like the Godzilla Loader download and install a reputable anti-virus application and do not forget to keep it up-to-date.
SpyHunter Detects & Remove Godzilla Loader
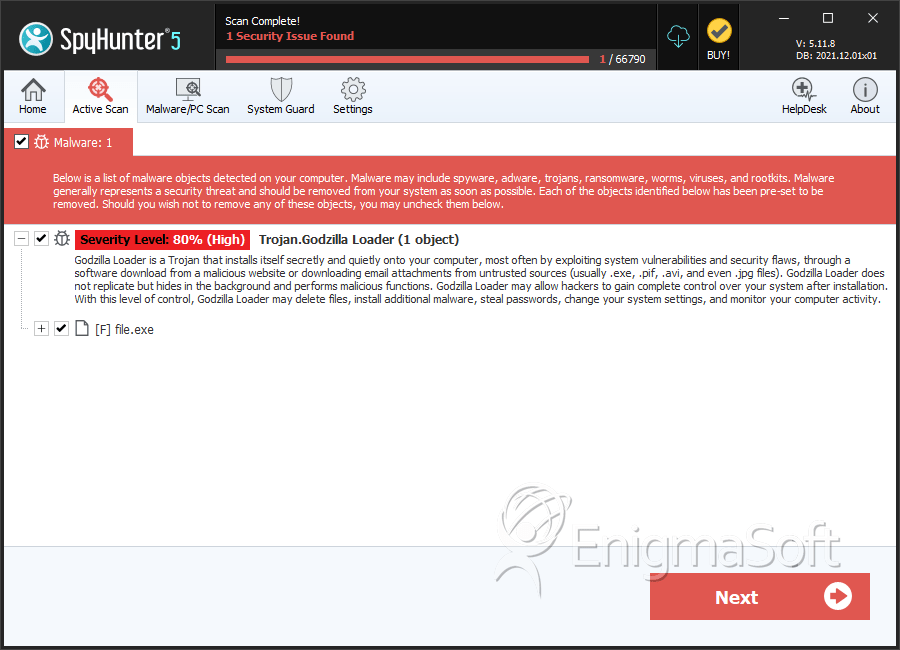
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | be6ad315b3b003abe5ceb9f2a6667a06 | 3 |
| 2. | file.exe | eef32da8c0a664615f2404902cc2340e | 0 |
| 3. | file.exe | d5debe3ed73deb9d8ab4ecdee23cbde7 | 0 |
| 4. | file.exe | cf4da95d5e2b291c2fc0803b53e79af8 | 0 |
| 5. | file.exe | 1557ef817b86b17f965ed723f13c6f0e | 0 |

