Emotet Malware Q3 2020 Massive Surge Garners Attention
 Earlier this year Emotet's operators took some time off but ever since Emotet returned it has been in the spotlight for many security researchers and organizations. The banking trojan-turned-dropper takes a prominent place in Bromium’s October Threat Insights Report. The report highlights a staggering 1200% spike in the number of Emotet instances detected by HP Sure Click. The number represents the comparison between numbers for Q2 and Q3 of 2020.
Earlier this year Emotet's operators took some time off but ever since Emotet returned it has been in the spotlight for many security researchers and organizations. The banking trojan-turned-dropper takes a prominent place in Bromium’s October Threat Insights Report. The report highlights a staggering 1200% spike in the number of Emotet instances detected by HP Sure Click. The number represents the comparison between numbers for Q2 and Q3 of 2020.
It should be noted that Emotet was inactive for most of Q2 which partially explains the huge spike. However, the significant increase in Emotet campaign activity is not just the result of a clever use of statistics. At the end of July, the cybercriminals behind Emotet came back in full force. The sheer volume of Emotet phishing campaigns was enough to warrant public warnings by multiple CERTs (Computer Emergency Response Teams) as well as one from Microsoft and CISA. Japan and New Zealand saw the biggest spikes in targeted Emotet attacks but France, Italy and the Netherlands were also in the cybercriminals’ sights.
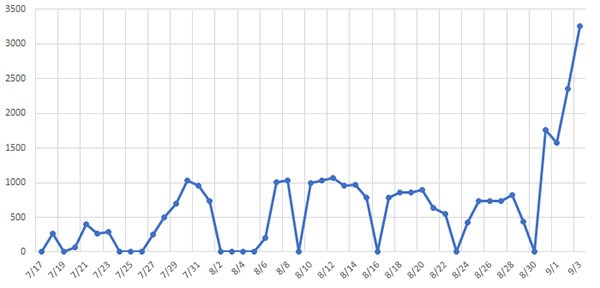
Emotet malware increase chart - Source: cyber-ir.com
Despite the long break, the main infection vector for Emotet hasn’t changed. The trojan is most commonly spread in phishing campaigns. In most cases phishing attacks use popular topics as subject lines and this is often true of Emotet campaigns. However, Emotet’s arsenal also includes a technique called "thread hijacking." This approach involves compromising a device or network and the accessible email accounts. Once the cybercriminals have compromised an email account they can inject email responses in already active message threads. This increases the chances of the target opening the email as it seems to be from a known contact. Those emails come with attached documents which contain malicious macros that, if enabled, will download and install Emotet on the victim’s device and accessible networks.
While Emotet used to be a banking trojan in its infancy, these days it’s mostly used as a dropper for other malware. The most common Emotet payloads are TrickBot, Qbot and Ryuk ransomware. There have been reports that after the initial push in August Emotet has slowed down. While that may be true, attacks are still carried out every work day and HP’s researchers anticipate that the campaigns will go on into 2021.