'Drive-by Exploit' Email Scam
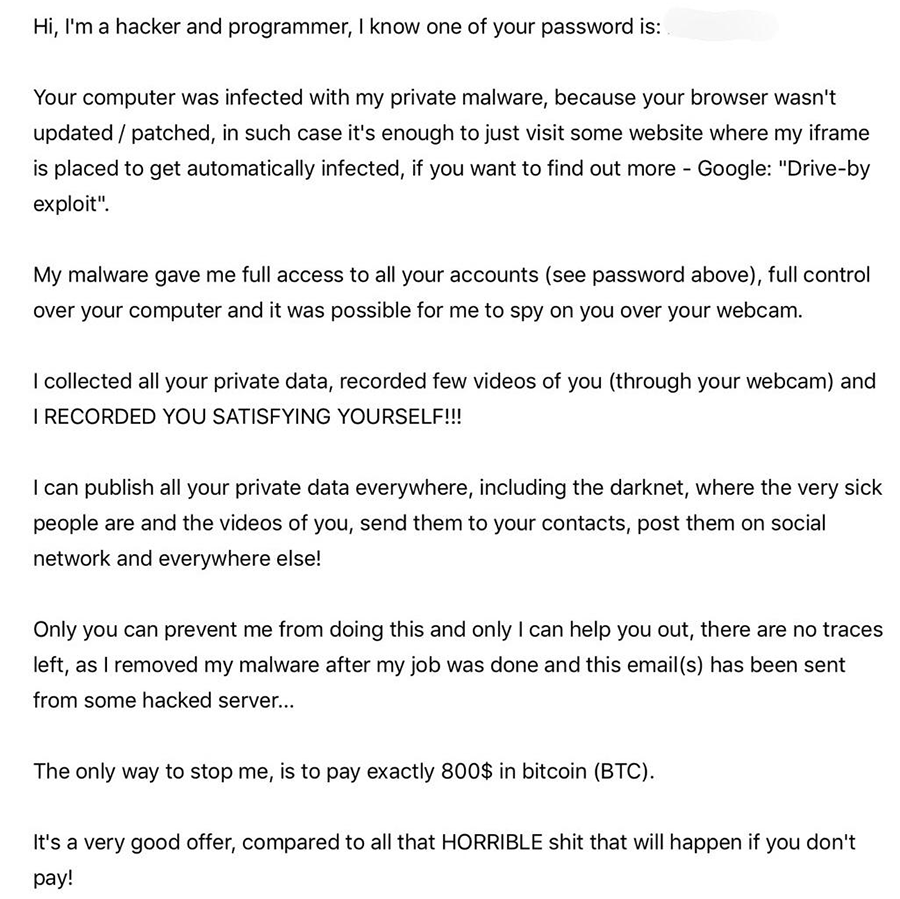
'Drive-by Exploit' Email Scam Image
Not all cyber crooks are armed to the teeth with all sorts of complex hacking tools, as the average user tends to imagine. Often, such elaborate threats are not needed as the attackers can use human psychology to manipulate the users into performing actions they normally would not. This is an art of social engineering which is very widely exploited for unsafe purposes by cybercriminals. The authors of the "Drive-by Exploit" Email Scan have employed this method in the spreading of their creation.
Table of Contents
Social Engineering Tricks
The "Drive-by Exploit" scam relies on spam email campaigns, and no users are safe if their emails are known publicly. The email distributed is rather lengthy. In it, the attackers go on to explain to users how their system had been compromised by a threat named "private malware" because they have visited a hacked website. Some versions of the scam claim that a RAT (Remote Administration Tool) has been installed on the victim’s machine to extract data and make pornographic video recordings. Still, that malicious tool had been subsequently removed in order not to leave any traces. The message is tailored in a manner meant to instill fear in the user as the attackers go on to claim that they have obtained the person's data and even videos of them. This is topped by their statement that all the data gathered will not only be sold on the Dark Web but will also be shown to the user's family, friends, and colleagues.
The Attackers Demand Between $700 and $1500 in Bitcoin
In the email, the cybercriminals claim that as long as the user pays them some amount between $700 and $1500 in the shape of Bitcoin, transferred to a given wallet, all the data that they have supposedly gathered will be wiped permanently, and the user will never hear from them again. However, nothing the attackers have said in the email is real. There is no "private malware" or RAT that has infected the user's computer. This particular scan also is known under a different alias – "Save Yourself" Email Scam. This became clear as experts noticed that both tactics were using the same email addresses – "saveyou36@8395.com," "saveyou51@1225.com," "saveyou84@4914.com," etc. They are both nothing but smoke and mirrors, and you should be ever vigilant because shady individuals like the ones responsible for the "Drive-by Exploit" and "Save Yourself" Email Scams are lurking all around the Web looking for unsuspecting and naïve users to trick.
“Drive-by-Exploit” Scam Also Displays Old User Passwords
Some of the victims of the "Drive-by-Exploit" campaign report that the scam emails they have received have contained legitimate passwords. The cyber crooks have inserted these user passwords in their attempt to make their claims sound plausible and to ensure that more people fall into the cyber trap. Many users would think their computer has actually been hacked as that would explain how the scammers have their passwords. However, the passwords, just like the email addresses, could have been obtained from old data breaches. Users’ information that has been subject to a breach in the past has most likely been sold on the Dark Web, and that is where the scammers have obtained it from. Yet, if it is a password that you still use, you have to change it immediately! Next, simply delete the "Drive-by-Exploit" messages from your mailbox. Needless to say - never open any attachment that could have been added to the scam emails, as it may download an actual piece of malware on your machine.

