DiamondFox
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 80 % (High) |
| Infected Computers: | 21 |
| First Seen: | September 7, 2016 |
| Last Seen: | October 16, 2020 |
| OS(es) Affected: | Windows |
DiamondFox is a threatening botnet that is being used for numerous attacks. DiamondFox can be adapted for multiple purposes. DiamondFox has been linked to attacks involving the theft of credit card data from PoS (Point of Sale) systems, as well as the theft of online passwords and login credentials. DiamondFox, like other botnets, is made up of numerous infected computers that can be coordinated to carry out powerful attacks. One of the threatening aspects of DiamondFox is that it is available to hackers that may not have the capabilities or the access to a botnet like this one, with its services being advertised on underground forums.
Table of Contents
The Harmful Actions Perpetrated by the DiamondFox Botnet
PC security analysts first came across DiamondFox by analyzing threat infections, uncovering a botnet that was developed in VB6. DiamondFox, also known as Gorynch, has numerous functions that make it an attractive option for hackers looking to carry out various types of attacks. DiamondFox may be used to carry out DdoS (Distributed Denial of Service) attacks, where a website or computer can be overloaded with requests from numerous bots; as a RAM scraper, where DiamondFox will track credit card information by scanning the target's network traffic and memory; and password collector (among numerous other features). However, despite that DiamondFox has numerous features, PC security researchers have observed various abnormalities in the DiamondFox's code.
Some of the features that DiamondFox offers con artists for carrying out their attacks include:
- DiamondFox can detect if it is running on a virtual machine, which allows it to evade detection from PC security analysts.
- DiamondFox can detect other security methods such as debuggers and researcher applications.
- DiamondFox can be configured to be installed in a variety of manners and to maintain persistence in custom ways.
- DiamondFox can delete itself permanently to evade analysis.
- DiamondFox includes a keylogger function, that can track what is typed on the target's keyboard.
- DiamondFox can spread through USB external memory devices.
- DiamondFox can disable the Task Manager, the Windows Registry Editor, and other useful applications for dealing with threats.
- DiamondFox can take screenshots of the victim's computer and send them to its Command and Control server.
- DiamondFox's functions can be expanded through the use of plug-ins.
Researchers will find it interesting to know that DiamondFox will look for the following strings in the computer where it is running to detect whether it is running on a virtual system or researcher computer:
ANTIVIRUS
VWINXP-MALTEST
MALWARE-STAR
VMG-CLIENT
HOME-OFF-D5F0AC
NAMAMO-AAAFC41B
BRIAN-BCAD2EA45
CANON
PAN-1E6ECC1F78B
VM_WINXP
WOLF
TEST
COMPUTERNAME
USER-2A6E79DA98
CITY5
Z-235
XP-SILO5YEIYKEX
JH-C64A2618CF31
SYSTEM-78358297
How Botnets Such as DiamondFox Work
Botnets are a large part of how threats spread and attacks are carried out. Con artists will leverage the power of these large networks of computers to send out massive amounts of spam email, infect computers with threats, or interfere with websites and servers through DdoS attacks. In most cases, the computers in the botnet belong to innocent computer users. DiamondFox will be installed on the victim's computer, allowing third parties to control the computer from a remote location and use it in their attacks. While a single computer, by itself, may not be capable of doing much, thousands of computers working together from different parts of the world can carry out mass operations that are a large part of what makes threat attacks so effective. If you suspect that your computer has become infected with DiamondFox and is connecting to a Command and Control server automatically, you should disconnect it from the Internet and use a reliable security program to detect and remove the DiamondFox. Preventive methods are essential in ensuring that DiamondFox does not enter your computer in the first place.
SpyHunter Detects & Remove DiamondFox
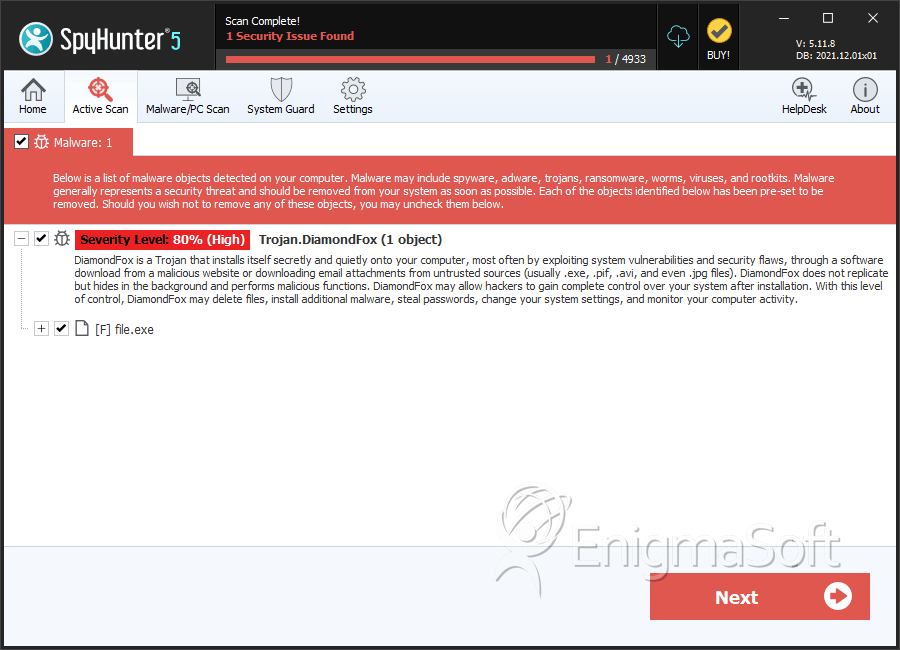
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | 6dd004531a0d20c8378815f613837b6b | 0 |
| 2. | file.exe | 1a7561a0759e02d96b349fd520c04bff | 0 |
| 3. | file.exe | 192973458e74aed3329c42cee89801e0 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.