Client Maximus
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 80 % (High) |
| Infected Computers: | 1,007 |
| First Seen: | September 14, 2017 |
| Last Seen: | June 14, 2025 |
| OS(es) Affected: | Windows |
The Client Maximus is a recently discovered threat that is being used by Brazilian con artists to trick computer users. The Client Maximus appearance in the Brazilian scene indicates that the people responsible for these attacks are increasing in sophistication, and may have larger resources at their disposal possibly. Based on the Client Maximus, it is clear that the con artists in Brazil are now collaborating with other con artists around the world and copying code from sophisticated threat campaigns used in other parts of the world. This demonstrates a clear trend of the increasing sophistication of these attacks.
Table of Contents
How the Client Maximus Malware Infection Works
The Client Maximus' main purpose is to take money from the victims. The Client Maximus has characteristics of banking Trojans that target Brazilian banks specifically. The Client Maximus monitors the victim's online activities to detect and interrupt online banking on the victim's Web browser. The Client Maximus can then use social engineering tactics, such as displaying bogus screens on the affected Web browser to trick the victims into giving up their login credentials and other important banking information.
Distribution Methods Used by the Client Maximus
It seems that most of the Client Maximus attacks are being accomplished with corrupted Java scripts that are delivered to the victims' computers using a variety of common threat delivery methods. Once the Client Maximus has been installed on the victim's computer, it seems that the Client Maximus uses DLL hijacking to carry out its attack inside the victim's computer. After being installed (typically with the help of social engineering techniques), the victim's computer will come under the control of the people operating the Client Maximus.
Beware of Social Engineering Tactics
The Client Maximus will monitor the victim's Web browser and trigger when the victim visits a banking website. The Client Maximus will monitor window titles on the affected Web browser, checking them against a list of predetermined targets. When the Client Maximus detects that the victim is connected to a particular banking website, the Client Maximus will connect to its Command and Control server, and a RAT (Remote Access Trojan) will be used to access the victim's computer. The Client Maximus will block access to the victim's Web browser when the victims enter their banking password. The victims' Web browser will instead display inaccessible social engineering screens designed to prevent them from minimizing or closing the affected window. During this period, the victim, responding to the social engineering cues, will provide authentication elements that allow the con artists to withdraw money from the victim's bank account or carry out other tactics.
Protecting Your Computer from Attacks Like the Client Maximus
Brazilian online banking (much like the Russian online banking scene) has been a prime target for threat creators in the last few years. Because of this, computer users that carry out transactions on Brazilian banks must be careful to ensure that they are protected against the Client Maximus and other sophisticated banking Trojans. There are several steps you can take to ensure that your computer is protected from the intrusion of these threats. The most important of them is to ensure that you are using a trusted security program. It is essential to ensure that all of your software, not only your security program, is updated constantly with the latest security patches and other updates, which can help prevent the con artists from installing unwanted components on your PC.
When choosing an online bank, ensure that your bank has a multiple-step authentication, which can prevent the con artist from tricking you into providing your banking password. Become familiar with your online bank's login procedures and to take caution if any changes occur during the login process. Unexpected windows or messages, especially those asking for login data, should be treated with suspicion.
SpyHunter Detects & Remove Client Maximus
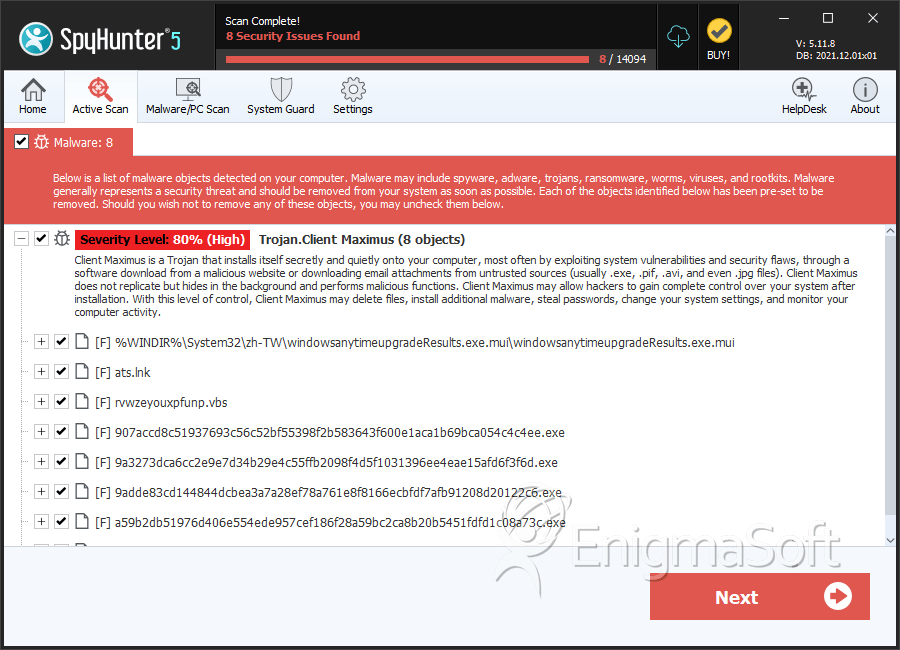
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | windowsanytimeupgradeResults.exe.mui | 4599f72c52d67559f8acfa441f506a68 | 360 |
| 2. | ats.lnk | 2137f22dd0adbfd76c4358cecd391e27 | 3 |
| 3. | rvwzeyouxpfunp.vbs | bc057ca73bbddb77ae1bd9984dd6022f | 3 |
| 4. | 907accd8c51937693c56c52bf55398f2b583643f600e1aca1b69bca054c4c4ee.exe | e8ebe596b60ca9e1bf59d40a311b408b | 0 |
| 5. | 9a3273dca6cc2e9e7d34b29e4c55ffb2098f4d5f1031396ee4eae15afd6f3f6d.exe | 1f5e5aee1d18a6fc95b14fc1984cbb5a | 0 |
| 6. | 9adde83cd144844dcbea3a7a28ef78a761e8f8166ecbfdf7afb91208d20122c6.exe | 612ea6d5083c5ccbdffadc7fca61fb3e | 0 |
| 7. | a59b2db51976d406e554ede957cef186f28a59bc2ca8b20b5451fdfd1c08a73c.exe | 48bad27fb46713dd82015652fead8230 | 0 |
| 8. | ad0f6f11d7c33052d868883fc5e6d696a36fd794f3d6bec55717f6b96532ebf8.exe | 72c130074e78c3139dd60fe8c5c938e9 | 0 |
| 9. | ad5e436662095ab139dee7f078c602dfb40d276ba8a0ca5f7e8ccf5c11a13cfd.exe | cca9d110e8fdfb36b86383122dd13bc4 | 0 |
| 10. | af0da86ffca86d1af7a541026d4a9b99522e155085a094fc130e945977bc77b6.exe | ff55de62b8f71e855fe20773e53fb574 | 0 |
| 11. | bcbc6f9ed5f19266365727473f1b0481fd217e4a6eea7a054a5ac93003855974.exe | 6e0ac45009d98b50283c545dd9489ae3 | 0 |
| 12. | c1abcdc498852eb94f649948416f380bdc55304d10b7a70d5fc2676d9cb380a0.exe | 17a6941c99a55a31ddeae8c75419f989 | 0 |
| 13. | c1df4a05d0d4884310cda3b143518b4a2ed9bddc1c364b8b23dcd45d4aef26c9.exe | 5a0b2e29adc782971d4b4911933858ab | 0 |
| 14. | c2626a33e0d9cb3ccc89786f25efc4fb32b9ae487c2472d70d4004131c7aa462.exe | c4af95b65d7e32011187a887d624b958 | 0 |
| 15. | c410e2094a8da0a4e03d7655ea4d32abde19eab8be1aea926a26945728173595.exe | f8ba3f4edb493d5f7bb922dfc922fae1 | 0 |
| 16. | c88f27d9dd4701f3a5f3183a6ceb715ac2efd00c6655845c70fc2e599b778a01.lnk | 4e602c03c75ceccd9614b56d2e1b2b00 | 0 |
| 17. | cxofkwsf.vbs | e3f926303147c3697c86f3e807ce19e2 | 0 |
| 18. | d17edb0235024927fbb68d3359e7a8a9da808429ea09edf1262de84793d70ba8.exe | c37c10389755ae942e1929f6cafbe155 | 0 |
| 19. | d65f6db00ed2e098db351f4ed84cc80e145d4356125ec603c811a452b4bf7435.exe | 1d1f6119027a6a215e3c23555737806d | 0 |
| 20. | d6f611587b8344c3db1f0287cb733591233e43fe1bb977af6f365b2f78f5e408.exe | 464a59225303b20edce15118744490af | 0 |
| 21. | db97efe49fddd94ec9ed0dc30be0d768ec29e8816e4588a18f39863db76f4170.exe | b1eac6c15953a896bc4ce7214a153f4b | 0 |
| 22. | Deigo.lnk | d844f0beb02855da6e14a97f61b9008c | 0 |
| 23. | e06c427c8fdf65100ac7341be12ec85bdf13c6ecdc07b92b35a75b1ed5a245c7.exe | 89acea6eb95777b01f94ad7e2aea3245 | 0 |
| 24. | ead4c0e53f575e07b2778c514e5623b247f38d279b40d0fcea3eaaf6d77d94c0.exe | 53840f0b8e52bcd983e89abf6f859b54 | 0 |
| 25. | eb4a0323bf35a844cb587258d9843c261874f84814be547cf3c2f55f9eb6c0c4.exe | dbce7006e0fd2c8e74c70a4845996517 | 0 |
| 26. | f775537ba598985f360ec574a942e2fccd23f6cd541cfec76bd5db08b50e63c2.exe | 74c2e4ba19a2f4e03f02a27aa72ab557 | 0 |
| 27. | f7f1c544ac69ffe8565464fa5fb3145380c75bf5cf8d56ce91287d95ff07e969.exe | 6a033c9c9f4860e4cec71b4d4e66e2f7 | 0 |
