Bublik
Bublik is a malware infection that has been active since Summer of 2011. Bublik received its last major update recently, in January of 2013. This means that Bublik stills represents a significant threat to computers around the world, being used by criminals to steal bank account login information, credit card details and other online banking data. Since Bublik exploits vulnerabilities in Internet Explorer, part of the payload associated with a Bublik attack involves forcing the infected computer to launch Internet Explorer if Bublik detects that another web browser is being used on the infected computer. Bublik gathers information by injecting a code into otherwise harmless file processes and then sending it to a remote server. Bublik also disables web browsers and some security programs on the infected computer and will often be associated with a backdoor or rootkit infection on the victim's computer (which will often be bundled in the same malicious email attachment used to distribute Bublik itself).
Although most banking Trojans are designed to hide their presence from the victim (making it easier for them to steal the victim's online banking information surreptitiously), Bublik has one defining symptom that should immediately alert computer users to the presence of this threat: Bublik will cause Internet Explorer to launch instead of other web browsers launched on the infected computer. When the victim attempts to open Google Chrome, Opera, Safari or other commonly used web browsers, Internet Explorer is open instead. To do this, Bublik makes a change to the Windows Registry that ensures that Internet Explorer starts up instead of the intended web browser.
The initial Bublik infection will come from a malicious email attachment that is distributed using common spam email social engineering techniques. This malicious email attachment is contained in an email message which subject is 'Booking confirmation' and a fake email address with the domain booking.com. The malicious attachment can have a number of different names, but will usually imply that it contains booking details and will be in ZIP format. When this malicious ZIP file is opened, it will drop copies of Bublik's executable files in your system folder. Bublik will also make changes to the Windows Registry to ensure that these malicious executable files run automatically whenever the victim starts up Windows.
SpyHunter Detects & Remove Bublik
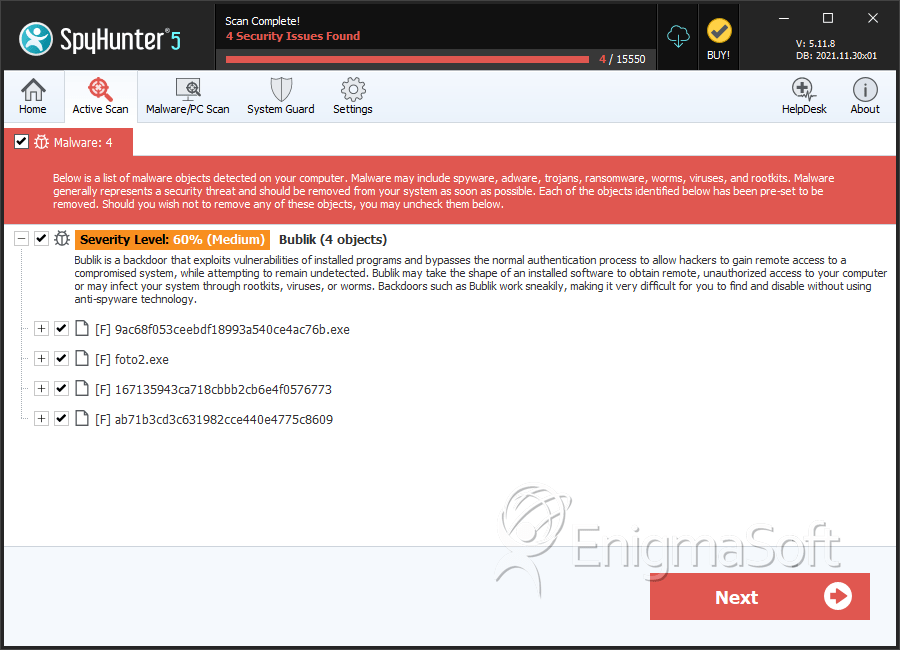
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | 9ac68f053ceebdf18993a540ce4ac76b.exe | 7463812252fe676326e7553af7908d8f | 0 |
| 2. | foto2.exe | 355e27b767b35abe58d37bc577987d2f | 0 |
| 3. | 167135943ca718cbbb2cb6e4f0576773 | 167135943ca718cbbb2cb6e4f0576773 | 0 |
| 4. | ab71b3cd3c631982cce440e4775c8609 | ab71b3cd3c631982cce440e4775c8609 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.