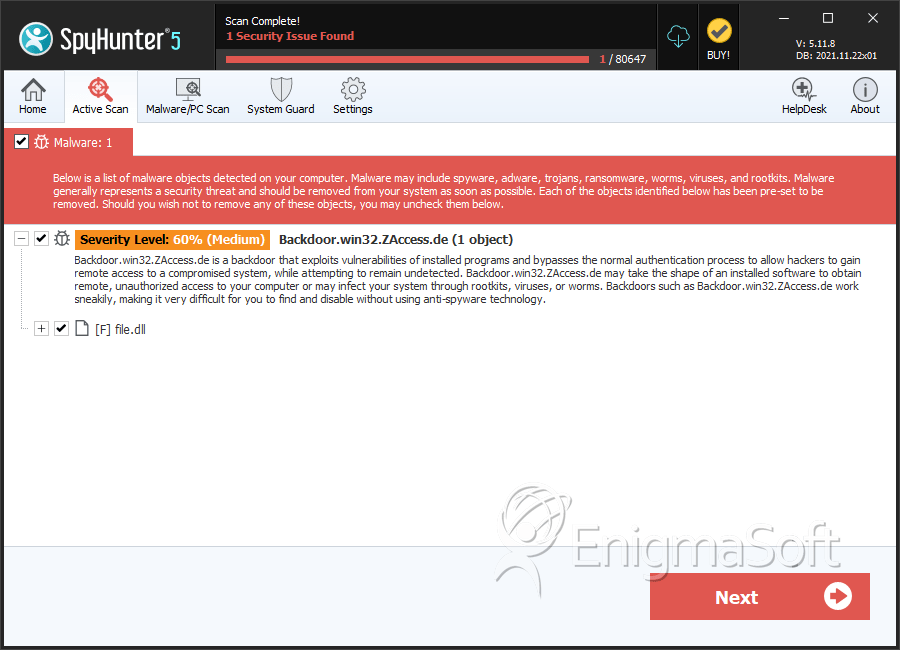
Backdoor.win32.ZAccess.de
Backdoor.win32.ZAccess.de is a backdoor Trojan that propagates through software exploits or existing network vulnerability. Once installed on the affected computer system, Backdoor.win32.ZAccess.de creates an entry to enable remote attackers get access to your computer, take control over your screen, steal personal information and download and execute malicious files without your knowledge. Backdoor.win32.ZAccess.de is created to damage your computer system by deleting important system files and disabling anti-virus programs. Backdoor.win32.ZAccess.de can also redirect you to malicious websites. to delete It is strongly advised to eliminate Backdoor.win32.ZAccess.de immediately upon detection.
Table of Contents
SpyHunter Detects & Remove Backdoor.win32.ZAccess.de
File System Details
Backdoor.win32.ZAccess.de may create the following file(s):
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | c:\program files\mozilla firefox\mozalloc.dll | ||
| 2. | c:\program files\mozilla firefox\libGLESv2.dll | ||
| 3. | c:\program files\mozilla firefox\mozjs.dll | ||
| 4. | c:\program files\mozilla firefox\mozsqlite3.dll | ||
| 5. | c:\program files\mozilla firefox\d3dx9_43.dll | ||
| 6. | c:\program files\mozilla firefox\libEGL.dll | ||
| 7. | c:\program files\mozilla firefox\D3DCompiler_43.dll | ||
| 8. |
C:\Documents and Settings\ |
||
| 9. |
C:\Documents and Settings\ |
||
| 10. |
C:\Documents and Settings\ |
||
| 11. | c:\program files\uTorrentBar | ||
| 12. |
C:\Documents and Settings\ |
||
| 13. | c:\program files\ConduitEngine | ||
| 14. |
C:\Documents and Settings\ |
||
| 15. | c:\program files\Conduit | ||
| 16. | c:\windows\system32\ConduitEngine.tmp | ||
| 17. | file.dll | f194c3614e08235f73c5e72691d7a751 | 0 |
Registry Details
Backdoor.win32.ZAccess.de may create the following registry entry or registry entries:
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{ED7E6D4E-DE3A-4662-A7CA-44ECA5C55ED5}\TypeLib
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{16FC10F7-1272-4A21-96B2-F746B9ADFF8D}\Programmable
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\flashobj.shdocls
settings = 51 00 00 00 00 00 00 00 00 00 00 00 6D 79 70 61 73 73 00 00
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{ED7E6D4E-DE3A-4662-A7CA-44ECA5C55ED5}\ProxyStubClsid32
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{16FC10F7-1272-4A21-96B2-F746B9ADFF8D}\ProgID
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\TypeLib\{2B56ADBB-327F-4905-A410-DDD81CE22BFC}\1.0\HELPDIR
HKEY_CURRENT_USER\Software\BIFROST1.2
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{16FC10F7-1272-4A21-96B2-F746B9ADFF8D}\Implemented Categories
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{16FC10F7-1272-4A21-96B2-F746B9ADFF8D}\VERSION
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{16FC10F7-1272-4A21-96B2-F746B9ADFF8D}\InprocServer32
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\TypeLib\{2B56ADBB-327F-4905-A410-DDD81CE22BFC}\1.0\FLAGS
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\flashobj.shdocls\Clsid
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{16FC10F7-1272-4A21-96B2-F746B9ADFF8D}


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.