Backdoor:Win32/Blohi.B
Backdoor:Win32/Blohi.B is a malware infection that criminals are using to cheat in card games located on Korean gaming websites. Backdoor:Win32/Blohi.B is also being used to steal information and money from computer users participating in the affected games. Backdoor:Win32/Blohi.B is part of a multi-component malware attack that involves three different kinds of spyware infections. These are being used to infect players of a Korean card game program. Backdoor:Win32/Blohi.B will steal sensitive data from the infected computer, potentially allowing criminals to gain access to the victim's bank accounts, online social media and email accounts and credit card information. Backdoor:Win32/Blohi.B can also allow people to cheat in the affected games by letting the person controlling Backdoor:Win32/Blohi.B gain an unfair advantage.
Computer users participating in the affected game are being targeted by three different malware infections. Backdoor:Win32/Blohi.B itself is a typical spy Trojan, monitoring the victim's online activity and allowing criminals to spy on the infected computer's screen, keystrokes and files. These malware attacks are also being used to gain access to personal identification numbers and credit card information which is used to register and participate in these games (which use real-world money for gambling). The gaming applications being affected by Backdoor:Win32/Blohi.B and its related attackers include the following:
- LASPOKER.EXE
- highlow2.exe
- baduki.exe
- duelpoker.exe
- HOOLA3.exe
- poker7.exe
- FRN.exe
The three malware infections associated with this attack are Urelas, Gupboot, and Blohi (Backdoor:Win32/Blohi.B). These are essentially a spy Trojan, a bootkit and a backdoor Trojan and keylogger.
Backdoor:Win32/Blohi.B makes its way into a computer through a social engineering strategy that involves disguising Backdoor:Win32/Blohi.B as a legitimate gaming application. Backdoor:Win32/Blohi.B itself uses NSIS (Nullsoft Scriptable Install System) installers to make it looks like as if Backdoor:Win32/Blohi.B is a legitimate gaming application. Backdoor:Win32/Blohi.B tries to establish a connection with a Korean search engine to make sure that the infected computer is connected to the Internet. Once this occurs, Backdoor:Win32/Blohi.B starts interfering with running file processes, taking screenshots of the infected computer and monitoring all keys pressed on the victim's keyboard. Backdoor:Win32/Blohi.B has the ability to cause the appearance of a fake Blue Screen of Death. This fake Windows error screen may be used to trick computer users into restarting their computer so that they will allow additional malware to be installed on their computer without being aware.
SpyHunter Detects & Remove Backdoor:Win32/Blohi.B
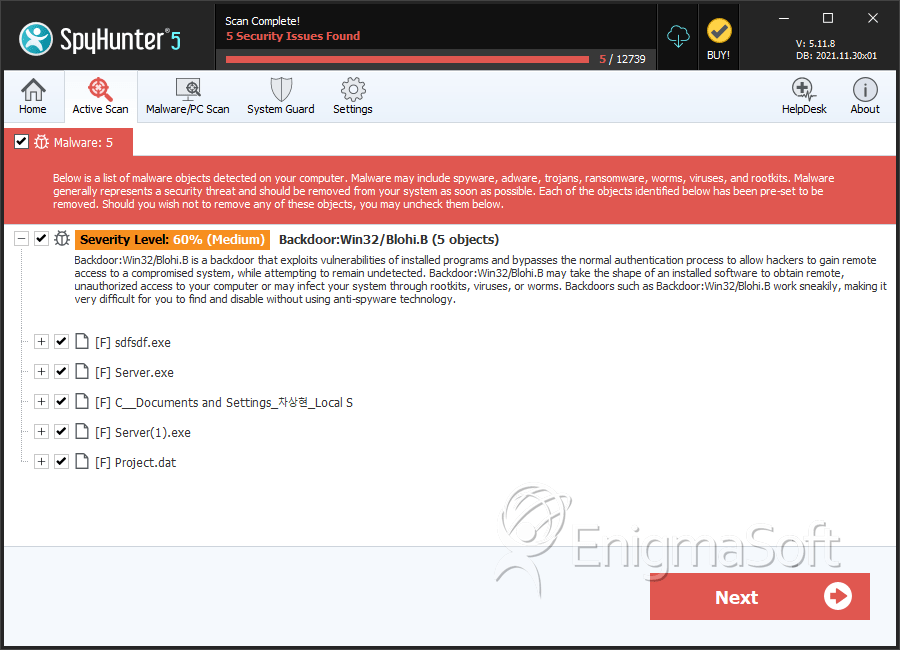
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | sdfsdf.exe | 16ff3d13debbf82a27463c1eac15c61a | 0 |
| 2. | Server.exe | ac1252cb0a80bfdf1e502599e7b68e24 | 0 |
| 3. | C__Documents and Settings_차상현_Local S | 336a057dbc314f886c02aa9b0cd3ecea | 0 |
| 4. | Server(1).exe | 7e5e2c6dc85a78be00071bf2ea816809 | 0 |
| 5. | Project.dat | 3fe5d8db697c9c2e123b830f36224816 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.