Backdoor.Win32.BlackHole
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 11 |
| First Seen: | January 26, 2010 |
| Last Seen: | December 8, 2019 |
| OS(es) Affected: | Windows |
Backdoor.Win32.BlackHole is dangerous Backdoor malware that enters your computer using manipulative methods. It will gain access the computer, without permission or and once it is active, you will experience many annoying computer issues. The biggest problem with Backdoor.Win32.BlackHole is that it's main purpose is to give hackers to secure remote access to a computer, as well as install all types of additional malware and threats that will harm your computer. Backdoor.Win32.BlackHole may proceed to copy itself onto other remote locations on your computer, as well as the factor that it may also execute certain processes, delete information, create information as well as modify certain system files within your machine.
Computer experts recommend using a well-known malware remover to detect and remove Backdoor.Win32.BlackHole from the compromised system. Backdoor.Win32.BlackHole will wreak havoc in your life if given the chance. Terminate this Backdoor malware immediately once it has been detected.
Table of Contents
Aliases
15 security vendors flagged this file as malicious.
| Anti-Virus Software | Detection |
|---|---|
| Panda | HackTool/BlackHole.CA |
| Ikarus | HackTool.Win32.BlackHole |
| Microsoft | Backdoor:Win32/Musminim.A |
| Antiy-AVL | HackTool/Win32.BlackHole.gen |
| AntiVir | BDS/BlackHol.A |
| DrWeb | BackDoor.DarkHole.1 |
| Comodo | UnclassifiedMalware |
| Sophos | Troj/MusMinim-B |
| BitDefender | Backdoor.BlackHol.A |
| Kaspersky | HackTool.Win32.BlackHole.a |
| ClamAV | Backdoor.BlackHole-1 |
| Avast | MacOS:BlackHole [Trj] |
| Symantec | Trojan.ADH |
| F-Prot | W32/MalwareF.ABHXT |
| NOD32 | probably a variant of Win32/Agent.CZVCFVD |
SpyHunter Detects & Remove Backdoor.Win32.BlackHole
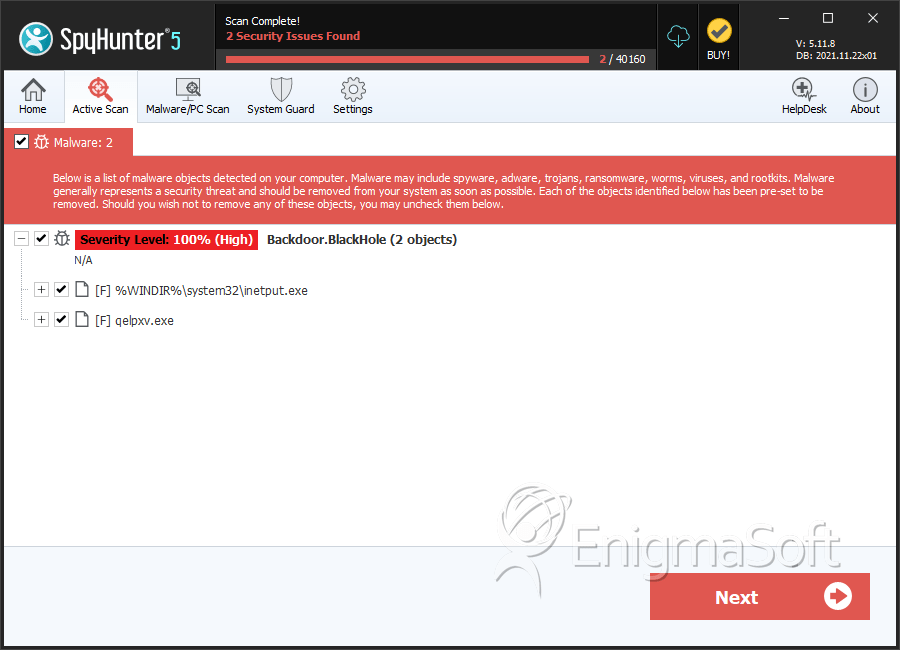
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | inetput.exe | 8145f8a5a84bfe540ccae4e187734fd7 | 10 |
| 2. | qelpxv.exe | 44231b5d10df4693599d3522e3ac325e | 0 |

