Backdoor:Win32/Bezigate.B
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 60 % (Medium) |
| Infected Computers: | 34 |
| First Seen: | September 25, 2013 |
| Last Seen: | March 24, 2022 |
| OS(es) Affected: | Windows |
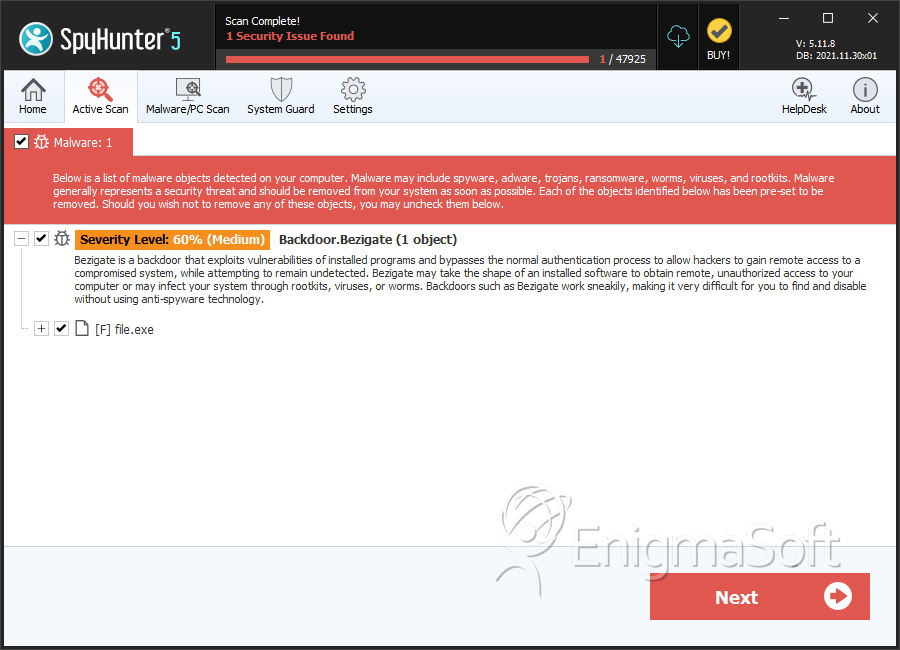
Backdoor:Win32/Bezigate.B is a backdoor Trojan that permits cybercrooks to obtain remote unauthorized access and control of the targeted PC. Backdoor:Win32/Bezigate.B can accomplish various potentially harmful activities on the corrupted PC, incorporating but not limited to stealing sensitive details and files and transmitting them to a distant server. Backdoor:Win32/Bezigate.B drops and executes copies of itself in one of several folders (%current directory%, %windir% and %APPDATA%), as any of the file names. Backdoor:Win32/Bezigate.B modifies the Windows Registry to make sure that it can load automatically whenever the computer user boots up the affected computer. Backdoor:Win32/Bezigate.B tries to communicate with cybercrooks using the particular combinations of URLs and ports. Backdoor:Win32/Bezigate.B can create/remove/copy/move/modify files and folders, kill and start processes, steal information about the PCr, enumerate and make modifications to the Windows Registry, enumerate/modify/start/end running services, open and close Internet browser windows, retrieve files from the PC and transfer them to the cybercriminal, log keystrokes and steal private details.
Table of Contents
SpyHunter Detects & Remove Backdoor:Win32/Bezigate.B
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | 912d940cd2652d092cca54a8d6fad54c | 1 |
| 2. | microdbs.exe | ||
| 3. | msizap.exe | ||
| 4. | spsreng.exe | ||
| 5. | 456.exe | ||
| 6. | msiexc.exe | ||
| 7. | mypass.exe | ||
| 8. | xtreme.exe | ||
| 9. | 123.exe | ||
| 10. | mscon.exe | ||
| 11. | msupdt32.exe | ||
| 12. | stub2546.exe | ||
| 13. | file.exe | 6b93722a18630cf1d2ed71f133041e01 | 0 |
Registry Details
URLs
Backdoor:Win32/Bezigate.B may call the following URLs:
| 78.184.197.86 1604 |
| abdelsamed666.no-ip.com 5050 |
| all.evilpacket.org 7709 |
| barod.no-ip.biz 1515 |
| ermenello.servegame.com 4781 |
| fofo-123.no-ip.biz 1515 |
| hack4ps.no-ip.info 131 |
| jorlu.sytes.net 645 |
| m30w.evilpacket.org 7709 |
| monbebe.no-ip.org 1515 |
| mrkarar.np-ip.ibz 1515 |
| network-info.sytes.net 1604 |
| nikt0x.no-ip.biz 1515 |
| niku.uk.to 1515 |
| nnqi.vicp.cc 81 |
| r0x0r.no-ip.org 1515 |
| rawr.evilpacket.org 7709 |
| sorbbolindo.no-ip.biz 1515 |
| topcumt2.zapto.org 1604 |
| updupdupd.servepics.com 1604 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.