Backdoor.Proxyier
Backdoor.Proxyier is a family of Trojans that includes malware such as the Claretore Trojans, and several variations of the Proxyier family. Backdoor.Proxyier is a relatively recent infection, first detected in December of 2012. ESG security researchers have classified any contact with Backdoor.Proxyier Trojans as severe security risks which should be dealt with at once. According to ESG security analysts, there have been several reports of Backdoor.Proxyier infections being spread through infected music websites, particularly targeting computer users in India. While Backdoor.Proxyier Trojans may have several ways of attacking a computer system, they all have in common the fact that they attempt to inject themselves into running file processes on the infected computer to try to monitor any web browser activity in order to attempt to direct the victim towards URLs containing other malware or online scams. ESG security analysts have received reports of Backdoor.Proxyier infections being spread through a file named scandsk.exe, which is disguised as a security program. Actually, this file is the Backdoor.Proxyier Trojan itself.
Table of Contents
How the Backdoor.Proxyier Trojans Infect a Computer System
The main symptom of a Backdoor.Proxyier infection is the appearance of a malicious modification to the Windows Registry which, pretending to be a 'Windows Update Center', actually allows Backdoor.Proxyier to run automatically when the infected computer starts up. During its installation process, Backdoor.Proxyier creates two files, an EXE and a TMP file. These have randomly-generated names and are placed in the System Folder and in the Temp folder respectively. Backdoor.Proxyier also creates the registry entry mentioned above. Once this is done, Backdoor.Proxyier can use the TMP file as a variation of a DLL hijacking attack, by attempting to copy it into every process currently running on the infected computer system.
The main way in which Backdoor.Proxyier attacks is by trying to intercept web browser communications, by monitoring essential DLL files used by all web browsers. It then has the ability to intercept and replace links in web pages. For example, some variants of Backdoor.Proxyier have been found to replace the JavaScript used by Google advertisements in order to change the advertisements displayed on the infected computer (allowing criminals to profit from advertising revenue). Backdoor.Proxyier has the ability to monitor the infected computer and relay this information to a remote server through a 'backdoor' (an unauthorized opening) in the infected computer system's security.
SpyHunter Detects & Remove Backdoor.Proxyier
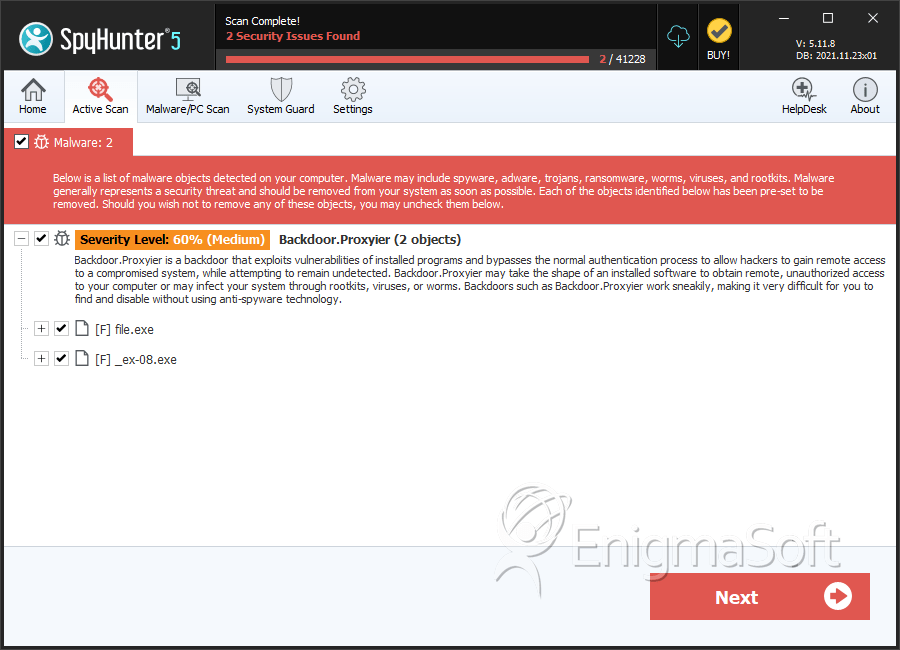
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | 43a6067f34419267d3086206683ada7a | 0 |
| 2. | _ex-08.exe | e5ba68e3ea1e15b7952e8ff8ea6f8e04 | 0 |
| 3. | _ex-08.exe | d6a48d531d8b4a23f4f95d724be561c7 | 0 |
| 4. | _ex-08.exe | 93a9be3b2b01a0b16a240ce28c508be7 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.