Backdoor.Proxybox
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 60 % (Medium) |
| Infected Computers: | 54 |
| First Seen: | July 10, 2012 |
| OS(es) Affected: | Windows |
Backdoor.Proxybox is a backdoor Trojan able to open a back door and allow a hacker to gain remote access on poorly protected computers. Trojans are stealth and can not only open a port to communicate with a C&C server, but can also make systems changes comparable to that of a programmer or IT expert. Trojans use common vectors to gain deceptive entry, often hiding behind faces (i.e. interfaces and prompts) claiming to be innocent or of great help. Studies show most malware invasions occur when victims click too fast and fail to fortify their systems with proper security. After slipping inside, Backdoor.Proxybox will set up shop by executing files, adding registry entries, including one that runs the malicious executable each time Windows is booted, and by performing its main function, opening a backdoor. An open port could allow more malware to be downloaded, such as a keylogger or a rogue security program.
Backdoor.Proxybox is without an interface and was intended to work resident in the background. If your system is suddenly running slow, web pages freezing up or you've been notified Backdoor.Proxybox is present, you should react swiftly by using a stealth anti-malware to uproot and permanently remove all hidden malware.
Table of Contents
Aliases
15 security vendors flagged this file as malicious.
| Anti-Virus Software | Detection |
|---|---|
| Panda | Generic Malware |
| AVG | BackDoor.Agent.ARMF |
| Fortinet | W32/Agent.DEOE!tr.rkit |
| Ikarus | Trojan.Rootkit |
| Antiy-AVL | Trojan/Win32.Agent.gen |
| AntiVir | TR/Rootkit.Gen |
| DrWeb | Trojan.NtRootKit.14541 |
| Comodo | UnclassifiedMalware |
| Sophos | Mal/Generic-L |
| Kaspersky | Rootkit.Win32.Agent.deoe |
| eSafe | Win32.Backdoor.Proxy |
| Avast | Win32:Malware-gen |
| Symantec | Backdoor.ProxyBox |
| K7AntiVirus | RootKit |
| McAfee | Generic.dx!bf3j |
SpyHunter Detects & Remove Backdoor.Proxybox
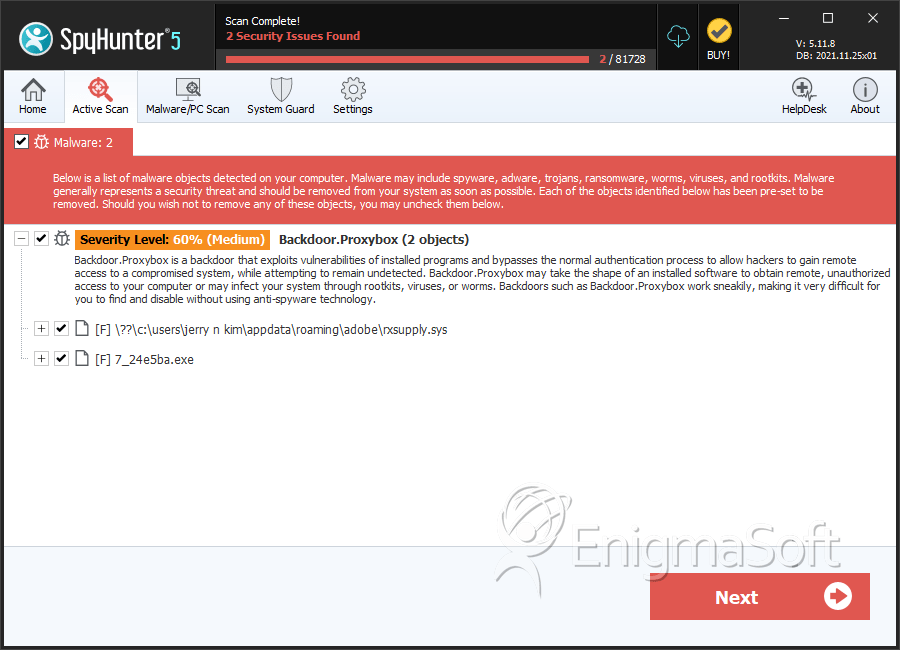
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | rxsupply.sys | 86908d0c072ce28a7650b78bab5a06e5 | 54 |
| 2. | %SystemDrive%\Documents and Settings\All Users\Application Data\Adobe\sp.dll | ||
| 3. | %SystemDrive%\Documents and Settings\All Users\Application Data\Adobe\rxsupply.sys | ||
| 4. | %SystemDrive%\Documents and Settings\All Users\Application Data\Adobe\fs.cfg | ||
| 5. | 7_24e5ba.exe | 24e5ba364afcaa1a4754a8902301c312 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.