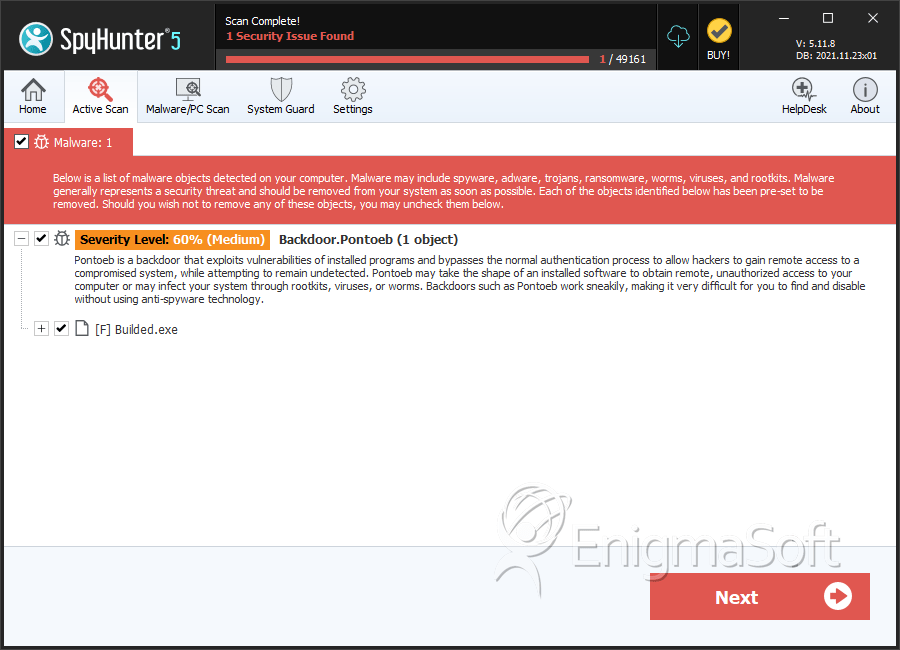
Backdoor.Pontoeb
Backdoor.Pontoeb is a dangerous backdoor Trojan that may find its way onto a computer through a backdoor vulnerability. Once installed, Backdoor.Pontoeb will load at startup of Windows where it may connect to a remote source. Remove attackers may have access to an infected system through Backdoor.Pontoeb which puts stored data at risk of being stolen. Furthermore, Backdoor.Pontoeb is known to hide amongst different executable files throughout a system's hard drive. The download of other unknown malware may occur once Backdoor.Pontoeb has connected to a remote source. It is very important to remove Backdoor.Pontoeb so it is not able to cause destruction through remove connections.
SpyHunter Detects & Remove Backdoor.Pontoeb
File System Details
Backdoor.Pontoeb may create the following file(s):
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | crstk.exe | ||
| 2. | uodbs.dll | ||
| 3. | Oik6C8D0B8D.sys | ||
| 4. | inlisw32.dll | ||
| 5. | ctfmonipa.exe | ||
| 6. | commctl32.dll | ||
| 7. | verupd.exe | ||
| 8. | wb.exe | ||
| 9. | WUDHost.exe | ||
| 10. | dwm.exe | ||
| 11. | pstc.exe | ||
| 12. | uTorent.exe | ||
| 13. | systemup.exe | ||
| 14. | mkqiq.exe | ||
| 15. | ctfmonqdd.exe | ||
| 16. | Counter-Strike Source.exe | ||
| 17. | 9719831.exe | ||
| 18. | inetsw32.dll | ||
| 19. | Windows.exe | ||
| 20. | win32rundll.exe | ||
| 21. | waudiohd.exe | ||
| 22. | unupx.dll | ||
| 23. | wtsx.exe | ||
| 24. | taskhostt.exe | ||
| 25. | netbt.sys | ||
| 26. | deep_freeze_standard_6_2.exe | ||
| 27. | CR-WR311.EXE | ||
| 28. | AppleMainInit.dll | ||
| 29. | onetsw32.dll | ||
| 30. | system.exe | ||
| 31. | svchost.exe | ||
| 32. | audiohd.exe | ||
| 33. | The_Lost_Watch_3D_Screensaver.scr | ||
| 34. | Builded.exe | 91768143d6c9909c3d36508a495263c8 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.