Backdoor.Bifrose.N
Backdoor.Bifrose.N is a backdoor Trojan that opens a back door on the compromised PC and steals confidential information. While being run, Backdoor.Bifrose.N creates the file and sets the file attribute to FILE_ATTRIBUTE_HIDDEN. Backdoor.Bifrose.N download files, upload files, executes and delete files and additional components. Backdoor.Bifrose.N creates the registry entry so that it can load automatically whenever you boot up Windows. Backdoor.Bifrose.N initiates a new Internet Explorer process, adds itself into it, ends its own execution, and proceeds onto running inside the new Internet Explorer process. Backdoor.Bifrose.N connects to the specific URL. Backdoor.Bifrose.N gathers disk and partition information, locale information, and titles of running applications, and changes the names of the files.
Table of Contents
SpyHunter Detects & Remove Backdoor.Bifrose.N
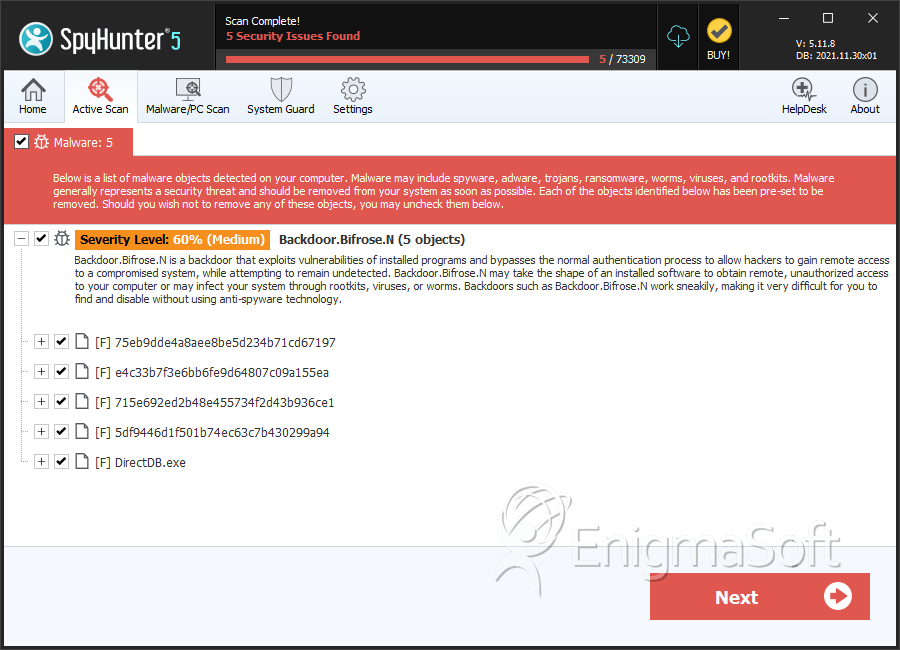
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | %System%\advapi32.dll | ||
| 2. | %CommonProgramFiles%\DirectDB.exe | ||
| 3. | %UserProfile%\Application Data\addons.dat | ||
| 4. | 75eb9dde4a8aee8be5d234b71cd67197 | 75eb9dde4a8aee8be5d234b71cd67197 | 0 |
| 5. | e4c33b7f3e6bb6fe9d64807c09a155ea | e4c33b7f3e6bb6fe9d64807c09a155ea | 0 |
| 6. | 715e692ed2b48e455734f2d43b936ce1 | 715e692ed2b48e455734f2d43b936ce1 | 0 |
| 7. | 5df9446d1f501b74ec63c7b430299a94 | 5df9446d1f501b74ec63c7b430299a94 | 0 |
| 8. | DirectDB.exe | bfeba75c012d5d995bfa50e76a21d089 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.