Ammyy Admin
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Popularity Rank: | 442 |
| Threat Level: | 10 % (Normal) |
| Infected Computers: | 265,579 |
| First Seen: | January 9, 2014 |
| Last Seen: | February 4, 2026 |
| OS(es) Affected: | Windows |
The AMMYY RAT is a Remote Access Trojan that has been around for quite a while. The AMMYY RAT has existed in some form since early 2016. Variants of the AMMYY RAT have been involved in a variety of malware attacks, ranging from sophisticated, high-profile malware attacks to small campaigns. The attacks associated with the criminals responsible for the AMMYY RAT, known as TA505, have been carried since, at least, 2014, and probably earlier.
Table of Contents
Recent Attacks Perpetrated by the AMMYY RAT
The most recent attacks involving the AMMYY RAT were spotted in Spring and Summer of 2018. These AMMYY RAT attacks involve corrupted spam email attacks, which include corrupted file attachments that download and install the AMMYY RAT onto the victim's computer. The spam emails used to deliver the AMMYY RAT will use spoofed email addresses, often spoofing the recipient's own domain in an attempt to make it seem as if the email is coming from within their own organization (increasing the likelihood that they will open the message). These emails will include subject lines that are vague and generic, often involving random digits and a word such as 'Bill,' 'Receipt' or 'Invoice.' Once the AMMYY RAT is installed, the AMMYY RAT will take over the victim's computer, making it possible for the criminals to control the victim's computer from a remote location.
How the AMMYY RAT Works
The version 3 of the Ammyy Admin, the precursor of the AMMYY RAT, was leaked on the Dark Web. Using the source code for this threat, criminals have been able to create threats like the AMMYY RAT to carry out attacks. The AMMYY RAT has several advanced features, which include the following:
- The AMMYY RAT can be used to control the infected computer directly from a remote location.
- The AMMYY RAT can be used to manage the victim's files, carrying out any sort of file operation and collecting data by uploading these files to a remote server.
- The AMMYY RAT has proxy support, which can help criminals use the infected computer as a proxy to carry out other attacks.
- The AMMYY RAT has audio chat capabilities, allowing the criminals to communicate with the victim or spy on the victim using the infected computer's microphone or Webcam.
The Potential of the AMMYY RAT Attacks
The AMMYY RAT attacks have the potential to cause quite a bit of damage, and the fact that the AMMYY RAT's source code is now available on the Dark Web readily has meant that new versions of the AMMYY RAT and variants of this threat can be released more frequently. These attacks can result in a wide variety of effects, depending on the intent of the criminal. Criminals can use the AMMYY RAT to collect data, spy on victims or harass computer users. The AMMYY RAT also can be used in high-profile attacks to collect proprietary data or for high-end operations. RATs like the AMMYY RAT have another application, which is to install other malware onto the victims' computers. Using RATs like the AMMYY RAT, criminals can install Bitcoin miners, ransomware, adware, or numerous other types of malware, which can be used to monetize the attack, in cases where the victim does not have data that is worthwhile for the criminals collect particularly.
Protecting Your Computer from Threats Like the AMMYY RAT
The best protection against threats like the AMMYY RAT is to have an updated and effective security program, which will protect your computer in real time. Additionally, you should take precautions against spam email messages, because they serve as the main way in which threats like the AMMYY RAT are distributed.
Aliases
3 security vendors flagged this file as malicious.
| Antivirus Vendor | Detection |
|---|---|
| Kaspersky | not-a-virus:RemoteAdmin.Win32.Ammyy.an |
| Antiy-AVL | RemoteAdmin/Win32.Ammyy |
| AntiVir | SPR/RemoteAdmin.AG |
SpyHunter Detects & Remove Ammyy Admin
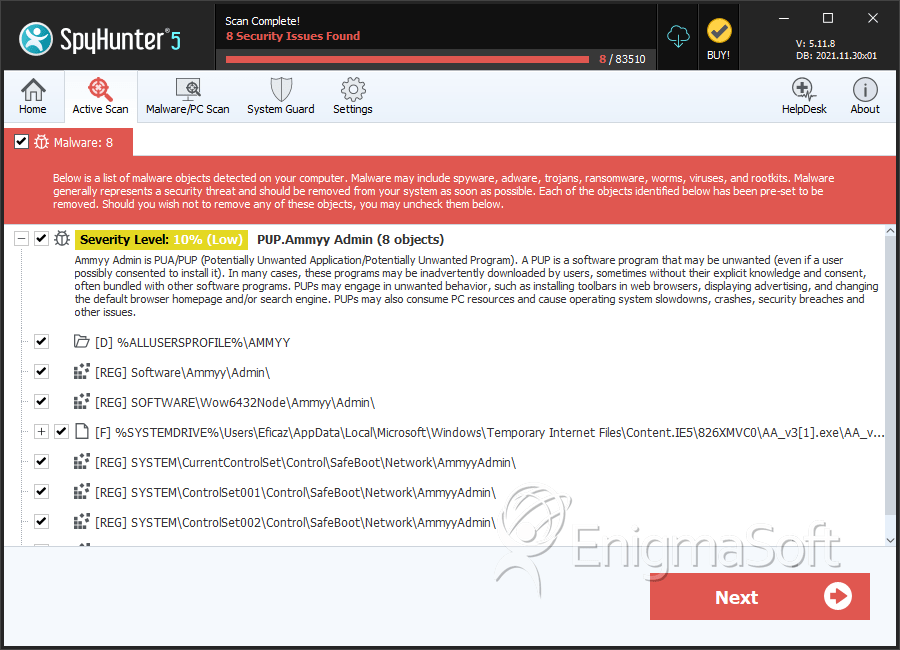
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | AA_v3[1].exe | 11bc606269a161555431bacf37f7c1e4 | 13,385 |
| 2. | CW2.exe | 5686a7032e37087f0fd082a04f727aad | 491 |
| 3. | ARE.SM | 84e4d318f5140e3ab182035aab3db603 | 41 |
| 4. | Ammyy Admin v3.exe | 7f7c2b7cf6c3e2c279af61a51014db14 | 6 |
| 5. | AMMYY_Admin[1].exe | 488df3646d78cdc4e68c25fcb3b6289b | 5 |
| 6. | AMMYY_Admin.exe | 221c2c1099923dc6348d7bc1a21d2a3b | 4 |
| 7. | AA_v3.2.exe | 1dd9262509f92afaa76f2be36f4a6693 | 2 |
| 8. | ammyy admin setup.exe | 9bfdaa941c5dd95f4bd1a8956d55c7fc | 2 |
| 9. | ammyy.exe |
Registry Details
Directories
Ammyy Admin may create the following directory or directories:
| %ALLUSERSPROFILE%\AMMYY |
| %ALLUSERSPROFILE%\Anwendungsdaten\AMMYY |
| %ALLUSERSPROFILE%\Application Data\AMMYY |
| %ALLUSERSPROFILE%\Dados de aplicativos\AMMYY |
| %ALLUSERSPROFILE%\Dane aplikacji\AMMYY |
| %ALLUSERSPROFILE%\Dati applicazioni\AMMYY |
| %ALLUSERSPROFILE%\Datos de programa\AMMYY |
Analysis Report
General information
| Family Name: | PUP.Ammyy Admin |
|---|---|
| Signature status: | Hash Mismatch |
Known Samples
Known Samples
This section lists other file samples believed to be associated with this family.|
MD5:
50d64ffeb08128d75bc388c7570cc770
SHA1:
31aa6cab8f8853d15c7e31f996733573dd7e20ec
SHA256:
FD1D7FD8C4B0E1BB8AED4D4386EE6F4ADB4C50D0ADE7CEACB27B122EE8AA1245
File Size:
657.89 KB, 657893 bytes
|
|
MD5:
48025a8d472cb91a48cf581c57cd64cb
SHA1:
2d6e65ee1a18741172c00dace16672bb81ceba2a
SHA256:
3176D09DE81567A400E3CF1002466B35AA3683BD6AAF2B6E67E9063A022501BB
File Size:
722.74 KB, 722736 bytes
|
|
MD5:
567f4e3137bf7dfa40a2be740c1dff49
SHA1:
ead7dbce3a78ac9ef4d80dd6ad1944608983bd67
SHA256:
53EF233B4674C51884B03E39066237DD6D8A0B596BABD5450E09D8702CEB39A5
File Size:
769.53 KB, 769528 bytes
|
Windows Portable Executable Attributes
- File doesn't have "Rich" header
- File doesn't have debug information
- File doesn't have exports table
- File doesn't have relocations information
- File doesn't have security information
- File has exports table
- File is 32-bit executable
- File is either console or GUI application
- File is GUI application (IMAGE_SUBSYSTEM_WINDOWS_GUI)
- File is Native application (NOT .NET application)
Show More
- File is not packed
- IMAGE_FILE_DLL is not set inside PE header (Executable)
- IMAGE_FILE_EXECUTABLE_IMAGE is set inside PE header (Executable Image)
File Icons
File Icons
This section displays icon resources found within family samples. Malware often replicates icons commonly associated with legitimate software to mislead users into believing the malware is safe.Windows PE Version Information
Windows PE Version Information
This section displays values and attributes that have been set in the Windows file version information data structure for samples within this family. To mislead users, malware actors often add fake version information mimicking legitimate software.| Name | Value |
|---|---|
| Company Name | Ammyy LLC |
| File Description | Ammyy Admin |
| File Version |
|
| Internal Name | Ammyy Admin |
| Original Filename | AMMYY_Admin.exe |
| Product Name | Ammyy Admin |
| Product Version |
|
Digital Signatures
Digital Signatures
This section lists digital signatures that are attached to samples within this family. When analyzing and verifying digital signatures, it is important to confirm that the signature’s root authority is a well-known and trustworthy entity and that the status of the signature is good. Malware is often signed with non-trustworthy “Self Signed” digital signatures (which can be easily created by a malware author with no verification). Malware may also be signed by legitimate signatures that have an invalid status, and by signatures from questionable root authorities with fake or misleading “Signer” names.| Signer | Root | Status |
|---|---|---|
| Ammyy LLC | COMODO RSA Certification Authority | Hash Mismatch |
| Ammyy | VeriSign Class 3 Code Signing 2010 CA | Hash Mismatch |
File Traits
- HighEntropy
- Installer Manifest
- No Version Info
- RAR (In Overlay)
- WRARSFX
- x86
Block Information
Block Information
During analysis, EnigmaSoft breaks file samples into logical blocks for classification and comparison with other samples. Blocks can be used to generate malware detection rules and to group file samples into families based on shared source code, functionality and other distinguishing attributes and characteristics. This section lists a summary of this block data, as well as its classification by EnigmaSoft. A visual representation of the block data is also displayed, where available.| Total Blocks: | 1,782 |
|---|---|
| Potentially Malicious Blocks: | 1,232 |
| Whitelisted Blocks: | 548 |
| Unknown Blocks: | 2 |
Visual Map
? - Unknown Block
x - Potentially Malicious Block
Similar Families
Similar Families
This section lists other families that share similarities with this family, based on EnigmaSoft’s analysis. Many malware families are created from the same malware toolkits and use the same packing and encryption techniques but uniquely extend functionality. Similar families may also share source code, attributes, icons, subcomponents, compromised and/or invalid digital signatures, and network characteristics. Researchers leverage these similarities to rapidly and effectively triage file samples and extend malware detection rules.- Ammy.A
Files Modified
Files Modified
This section lists files that were created, modified, moved and/or deleted by samples in this family. File system activity can provide valuable insight into how malware functions on the operating system.| File | Attributes |
|---|---|
| \device\harddisk0\dr0 | Generic Read,Write Data,Write Attributes,Write extended,Append data |
| c:\programdata\ammyy\hr | Generic Write,Read Attributes |
| c:\programdata\ammyy\hr3 | Generic Write,Read Attributes |
| c:\programdata\ammyy\settings3.bin | Generic Write,Read Attributes |
Registry Modifications
Registry Modifications
This section lists registry keys and values that were created, modified and/or deleted by samples in this family. Windows Registry activity can provide valuable insight into malware functionality. Additionally, malware often creates registry values to allow itself to automatically start and indefinitely persist after an initial infection has compromised the system.| Key::Value | Data | API Name |
|---|---|---|
| HKCU\software\ammyy\admin::hr | 絓獖ㅦ켟晨劽 | RegNtPreCreateKey |
| HKLM\software\wow6432node\ammyy\admin::hr | 絓獖ㅦ켟晨劽 | RegNtPreCreateKey |
| HKCU\software\ammyy\admin::hr3 | RegNtPreCreateKey | |
| HKLM\software\wow6432node\ammyy\admin::hr3 | RegNtPreCreateKey | |
| HKLM\system\controlset001\control\safeboot\network\ammyyadmin_1184:: | Service | RegNtPreCreateKey |
| HKCU\software\ammyy\admin::hr | 絓獖ㅦ㨖漬劽 | RegNtPreCreateKey |
| HKLM\software\wow6432node\ammyy\admin::hr | 絓獖ㅦ㨖漬劽 | RegNtPreCreateKey |
| HKCU\software\ammyy\admin::hr3 | RegNtPreCreateKey | |
| HKLM\software\wow6432node\ammyy\admin::hr3 | RegNtPreCreateKey | |
| HKLM\system\controlset001\control\safeboot\network\ammyyadmin_d4c:: | Service | RegNtPreCreateKey |
Windows API Usage
Windows API Usage
This section lists Windows API calls that are used by the samples in this family. Windows API usage analysis is a valuable tool that can help identify malicious activity, such as keylogging, security privilege escalation, data encryption, data exfiltration, interference with antivirus software, and network request manipulation.| Category | API |
|---|---|
| Anti Debug |
|
| User Data Access |
|
| Network Winsock2 |
|
| Service Control |
|
| Network Info Queried |
|
| Network Winsock |
|
| Network Wininet |
|
| Network Winhttp |
|