123.sogou.com
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Popularity Rank: | 2,654 |
| Threat Level: | 50 % (Medium) |
| Infected Computers: | 61,147 |
| First Seen: | September 28, 2015 |
| Last Seen: | February 1, 2026 |
| OS(es) Affected: | Windows |
Table of Contents
SpyHunter Detects & Remove 123.sogou.com
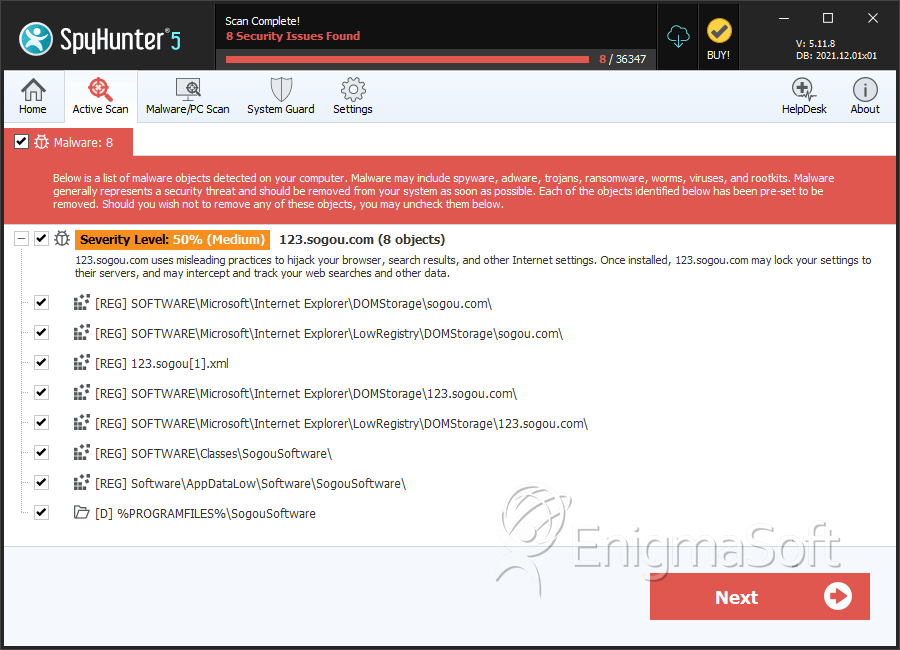
Registry Details
Directories
123.sogou.com may create the following directory or directories:
| %PROGRAMFILES%\SogouSoftware |
| %PROGRAMFILES(x86)%\SogouSoftware |
| %USERPROFILE%\AppData\LocalLow\SogouSoftware |
URLs
123.sogou.com may call the following URLs:
| /123.sogou.com |
Analysis Report
General information
| Family Name: | 123.sogou.com |
|---|---|
| Packers: | UPX |
| Signature status: | No Signature |
Known Samples
Known Samples
This section lists other file samples believed to be associated with this family.|
MD5:
810ebc873ae922c0f77a92ff8853feb5
SHA1:
98b6ae374501fe1f34e989f450e858493ebe7887
File Size:
2.62 MB, 2616973 bytes
|
|
MD5:
947a29e90c2643f9c922305bdf0adcef
SHA1:
f1350a03d0b4e318a4b06c3105409064e55b0bb7
File Size:
6.48 MB, 6484870 bytes
|
|
MD5:
331812beb7fd1cc72d071723d0d33871
SHA1:
7fc8857abb1b9bb064b49bf26b71277886101668
File Size:
2.62 MB, 2616973 bytes
|
|
MD5:
2dbdce5d57305a9fef24e3d92a26c501
SHA1:
772a29121c5182350cbff698410ab18ee6400f59
SHA256:
198996AF26E0EFE31AD8EA204B20DD3A0C1F6BB897493D913EC958B956A65C83
File Size:
2.62 MB, 2616449 bytes
|
|
MD5:
66e4234d0a09a0880598032d76f97241
SHA1:
e22453cd4e38285575b7fb3f0f8ff3653d321fe1
SHA256:
0CB504B79DC3738F788125E4FA6B341A28468044CC1A0FBB0A7692AA1A5D165E
File Size:
6.48 MB, 6484294 bytes
|
Show More
|
MD5:
1d6271070adb5aafd0e4b4bfdc9f64ed
SHA1:
75ef950d61cd0bde4e6f9043a26b6ffcf148515e
SHA256:
9C72C54DA230CABB5AD5F830611185766A8CF87CFEE3B058446034B4C37821B1
File Size:
6.48 MB, 6484294 bytes
|
|
MD5:
eea7800c4f460a50056ae40b9b04c479
SHA1:
1b73f6a8c5feabf641b67b3647abeb298fa71dc2
SHA256:
42AB12497A0313CA7869F3A25D80F56E2B9A8A657C0E5188E46F9C9C48821A40
File Size:
2.62 MB, 2616631 bytes
|
|
MD5:
63f31fb46ebb5777a91f370abd04efca
SHA1:
44c51daf73e1f8914254f661da9a4b03578fdcec
SHA256:
1D5C63375175603AD674CDE61C9CDD03C0A94E63F63F5554A1A10E2313C05221
File Size:
6.48 MB, 6484862 bytes
|
|
MD5:
3dd28a2bdb569d931095abf8655c1eea
SHA1:
7dbfcebbafaa0d0591bb6cbc6c251b455b3464a9
SHA256:
B25C1D7C67AF72A77A5DF2443A9A5C23F4A0EB3065448FE31FD2383D7515DC01
File Size:
6.48 MB, 6484870 bytes
|
|
MD5:
d91696af4b44d604b7961e2d52c585b9
SHA1:
e630da3728a7226940c7a675d3144c147bd4d15c
SHA256:
E6C6D28F06078D6FAA61287FDE1C427965B877F3AB0E3F813E298656DB293F6E
File Size:
6.70 MB, 6701044 bytes
|
|
MD5:
4a012fcff75e403c659a5097e9948fbc
SHA1:
b20c166dad60e7a2f3d47e99a90cd9f9a1c55ed3
SHA256:
52745717D37E69920C9EB7EF4E4EF6A069B35CE98352D73CB62D15B9D64B27B9
File Size:
2.62 MB, 2620910 bytes
|
|
MD5:
33349bbda2480ad01ba96a8920cb0fab
SHA1:
d6ba0eddfdcfe0cea2d6ab45114aaf1aa53e34b1
SHA256:
2CB121FAF8AF8806E7269C0B1AD9C4611C14C82419285BDEF1B9B3B6BE14E074
File Size:
2.63 MB, 2627229 bytes
|
|
MD5:
eaf61ea2df7491b110e8310822dfa67a
SHA1:
394e51cf4b052ec816eab4109d997a76ecf56f31
SHA256:
894A85BA9141BD72C603B31148CACA0D90EDB317C8E13AC604B423C636E56CFA
File Size:
2.63 MB, 2630471 bytes
|
|
MD5:
00003b547ea00efbfccd10ea93d3ac20
SHA1:
735e1c66682eee1cbff38f33b60301b4e5da3f61
SHA256:
594AC639CA8A9C1E458A60D8181B51C006521601CCEE6388A105E20100EFD1E2
File Size:
383.11 KB, 383112 bytes
|
|
MD5:
3b1636bb83c127cd64670a8b6af88158
SHA1:
d289c9396815b17d73709f33ff818d45bf992b14
SHA256:
BD2BB2144AE37ABD7C82FD9F0433619E6692E64CA0D34E1F8E65931F147B5DBB
File Size:
2.63 MB, 2629441 bytes
|
|
MD5:
049dd1a83ea77fa647957075443f2894
SHA1:
7033d560f6487a36d6611220e8f8550d2c5210bd
SHA256:
15FEC3D99B3FBE6159AE6C8DCD7538DAEC436B00DD049BD415495FBBA1D1A82A
File Size:
6.52 MB, 6523270 bytes
|
|
MD5:
1920b57044f13ab2eae9553e78356231
SHA1:
73b2422b87c6a296ba2015537a5287f0dec44261
SHA256:
6BD11BA4FE4A549709C4A1FC4E7E59E72F0E8924A266B0D84AD159BE436D75C6
File Size:
2.63 MB, 2627664 bytes
|
|
MD5:
70d97d24078dabdc5f72c106bd813165
SHA1:
044de90e0896ccfec4b6a7782ab4d99f53511558
SHA256:
105A09D4DBBE7009D9A335EFB4177EDBE7E51B67B9C522634318ECF2CA5860D3
File Size:
626.40 KB, 626402 bytes
|
|
MD5:
a3549fb4489de50bc0821f36659a053f
SHA1:
65ebd8423df12d2e240db1b266b86d436508bc9e
SHA256:
531032960D275AA1C394C7CCBFA6991B56962696E893993167DDF9BE10D528DE
File Size:
6.52 MB, 6519686 bytes
|
|
MD5:
b69f46b64bc7366cbdf355a211477a51
SHA1:
601a57563d8f095ce60cf50117c373312eee4e54
SHA256:
28256A6A1864D9A4BCA0539EA3C31802DBA88393389840242B688856D386CD65
File Size:
6.53 MB, 6525318 bytes
|
|
MD5:
424f2fc2470b76439fa7aabdd21711f8
SHA1:
9af148890768d24602495800fecacbee581de0ce
SHA256:
5FEB11706F771B98F7CE4CE7A22FF61CD943BC5B2893046BE63BCCD33625EE91
File Size:
1.15 MB, 1146584 bytes
|
|
MD5:
b226eacd974ef3dca15d2057478eda2b
SHA1:
3888c5c3ce649d71598790dba8631b94139a6edb
SHA256:
37C672B6AEEE2EC6383DD11C9F80CA6C8A1ADD6A662546728B60E4A687328114
File Size:
6.52 MB, 6519686 bytes
|
|
MD5:
2e27600c8f15e2c6bd60189e603ebea9
SHA1:
a87f4c46e4fdeb9e74e7b181f2898882b446e952
SHA256:
D28A1ACD622FAEAAA6A961DE3C6240E947E2350A2216E19B9398F1640DEA792B
File Size:
3.05 MB, 3046935 bytes
|
|
MD5:
8f282533da3d4da6d8eddc21b6cc98e0
SHA1:
e754ef3d339c97739aab1c11116b27cff31c93d8
SHA256:
1A0C2CDCD00960415D306B009BA516F1DA42F2E923D5D47A84CC2A7E49640B67
File Size:
2.63 MB, 2632717 bytes
|
|
MD5:
7881fd0c718cdc1dbda8884ccba8aca0
SHA1:
4573f5ee5584f3ae15a9310d733ee181c7f45311
SHA256:
A6C3A75026CCA0358911E30812BA97D0089FA33D0DFDF8DCC7F8FB5175F07484
File Size:
2.61 MB, 2612832 bytes
|
|
MD5:
73d6c1f5c826b54088ad4208f338ca6a
SHA1:
b06330557eaf39615ddefc10adb9384bb4d5d822
SHA256:
CF3B012489E6314243FC079CEF68077AB52C5CAE1C61E998FDEEFE17A9D324AC
File Size:
7.53 MB, 7529890 bytes
|
|
MD5:
ad3d11d8db7d03aa74e7531337fb9614
SHA1:
beb88d03ec7c56abb99f5374e95dfa0a8b5a46f5
SHA256:
AEB9113D146B14CFB05284AA9DF9694A5D10CBA24F4B25DC9E2EF7B7918CB978
File Size:
1.83 MB, 1833374 bytes
|
|
MD5:
009ce097b1bef310f87ce120376682e4
SHA1:
73c28213f14b99e6840f6879569144d131576e46
SHA256:
471241A241AD0B542E637E2B9C45E5741AB1DF0945B1D7406177FD08F1CB23B3
File Size:
2.63 MB, 2632717 bytes
|
|
MD5:
3417bedc0c16d4be5cc9c85d92886594
SHA1:
5cd55471d60148f27b36e4c90b502696e91968b5
SHA256:
68071F0D5217035B46E2E62E6FED515EF851EC147CC2F3C33526C7A098292FDC
File Size:
6.53 MB, 6531490 bytes
|
|
MD5:
f239001a348770396bb7aa40a7de8167
SHA1:
240a23046a0466bfb3708f4f9b42b0afe242db9b
SHA256:
EA5793168D4D88028A0FA67BC15CCC57726A9515B2F1D66EF5811135962934A3
File Size:
6.53 MB, 6531490 bytes
|
|
MD5:
01ba31f92e23b59456cfe0ff69c224ce
SHA1:
665e18f365ebacd70c9b85027f8a2e39ea9a4923
SHA256:
F255A640BD8FB294109F9130919D66A65DE2B98238F70F932D61782D70DAEE3F
File Size:
3.05 MB, 3050634 bytes
|
|
MD5:
df05d0e11abdb89a01a522b5feeb4971
SHA1:
4a67fd84bd4fa8504124e254f2a834f6b92ebd81
SHA256:
B5CA68220837ECD585C65D2EE606340FEDD2439C850043195B26E4D0919A6A4E
File Size:
6.48 MB, 6483942 bytes
|
|
MD5:
9d0f6745f410f1bcacab0f6126c08a41
SHA1:
7f6f8b13b44f403435267133c8ea92acfc75f9fc
SHA256:
37BCADE863E4ED46218627DEF5A533AE73549D8478BB1C5378D569C40314C15D
File Size:
2.63 MB, 2627486 bytes
|
|
MD5:
723f58c3d33923312ec5031ebe12caa4
SHA1:
d6e50e17969d18ff08e47dc0026de9ebb013b65b
SHA256:
3555DC33AEED561C37A27AE052E67F38CCA7A568A19033B9424E588B16552ADE
File Size:
7.53 MB, 7529890 bytes
|
|
MD5:
1010607718f1fcf2f2a1ae1760a391a1
SHA1:
d5b21d4a2ec4002ac2f7682b285ece7965040e4a
SHA256:
1555C7F3036929883788E57C987D972D3B69E2FA879A7E4822DD8FA904388C1D
File Size:
2.61 MB, 2613808 bytes
|
|
MD5:
1727c727e212fe19200f5e8338bf35af
SHA1:
05e48df97970a34ccfaec5137dac9a12b6c4bdb8
SHA256:
E31C4CA511410F12265669267948D1A54AB6A8CC1C4EEBE6AE071C24B7FB095E
File Size:
7.52 MB, 7524770 bytes
|
|
MD5:
a676e7bd4f04268756dadf63cf74311c
SHA1:
a5f524f0039eef971d872b93c48a53877ec59bcb
SHA256:
1E64AA2E429F3B5035999754DB3F2F06D45F97B8A12DB14F2396D196995EFBF4
File Size:
7.53 MB, 7529890 bytes
|
|
MD5:
74f1bce56ae3a82cefe0bd588ba5eb71
SHA1:
95c95ad94e0567c82dd53cabeffe5eafa0c27f75
SHA256:
553DA15033130C078AF29A8746E331742236400EB0888675B2FA49E6BE09565C
File Size:
7.52 MB, 7517090 bytes
|
|
MD5:
bae648856eab7720092cf12bebf6a792
SHA1:
5a1c4447749242a8e536d43bab3314560d1ea569
SHA256:
3F984FD0D1CBA638A554986B4270AEB2DF8F1979FB62A07463588C7CC4381B2C
File Size:
2.97 MB, 2974196 bytes
|
|
MD5:
308aa47682988e42ba4f21db04121456
SHA1:
fccd32aff040a488556b9cae02bb50bd3cd3e20a
SHA256:
F00DDE901C9FD36CBD67DB5B4D1377DC2F9333F1792EE75EF39CD241F34BDB4B
File Size:
2.62 MB, 2622507 bytes
|
|
MD5:
5f6174dbb1581679bfda2c018bcfcea3
SHA1:
a00cec29d3f1c8fd6886f153d773631b2dc7617a
SHA256:
23C2CA003B847B250427619A48CB12A69DA033533F1AEA0EDAF9681E413F9685
File Size:
2.63 MB, 2631816 bytes
|
|
MD5:
4b2b6401bb0ae7d8c0386c597d2124fb
SHA1:
084be6a5f924b336b71daa97909ba73b7d3df664
SHA256:
B554C74E64CD28612E06CE901B2E1998C9A1A4C443C0FEEE4EC8777E90AF2093
File Size:
6.52 MB, 6519686 bytes
|
Windows Portable Executable Attributes
- File doesn't have "Rich" header
- File doesn't have debug information
- File doesn't have exports table
- File doesn't have relocations information
- File doesn't have security information
- File has been packed
- File is 32-bit executable
- File is either console or GUI application
- File is GUI application (IMAGE_SUBSYSTEM_WINDOWS_GUI)
- File is Native application (NOT .NET application)
Show More
- File is not packed
- IMAGE_FILE_DLL is not set inside PE header (Executable)
- IMAGE_FILE_EXECUTABLE_IMAGE is set inside PE header (Executable Image)
File Icons
File Icons
This section displays icon resources found within family samples. Malware often replicates icons commonly associated with legitimate software to mislead users into believing the malware is safe.Windows PE Version Information
Windows PE Version Information
This section displays values and attributes that have been set in the Windows file version information data structure for samples within this family. To mislead users, malware actors often add fake version information mimicking legitimate software.| Name | Value |
|---|---|
| Company Name |
|
| File Description |
|
| File Version |
Show More
|
| Legal Copyright |
|
| Product Name |
|
| Product Version |
Show More
|
Files Modified
Files Modified
This section lists files that were created, modified, moved and/or deleted by samples in this family. File system activity can provide valuable insight into how malware functions on the operating system.| File | Attributes |
|---|---|
| c:\users\user\appdata\local\temp\nsa222.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete |
| c:\users\user\appdata\local\temp\nsb3a9.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete |
| c:\users\user\appdata\local\temp\nsb633.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete |
| c:\users\user\appdata\local\temp\nsb634.tmp\installoptions.dll | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\nsb634.tmp\iospecial.ini | Generic Read,Write Data,Write Attributes,Write extended,Append data |
| c:\users\user\appdata\local\temp\nsb634.tmp\iospecial.ini | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\nsb634.tmp\modern-header.bmp | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\nsb634.tmp\modern-wizard.bmp | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\nsb634.tmp\setuplib.dll | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\nsb634.tmp\system.dll | Generic Write,Read Attributes |
Show More
| c:\users\user\appdata\local\temp\nsbbe45.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete |
| c:\users\user\appdata\local\temp\nsc26d4.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete |
| c:\users\user\appdata\local\temp\nsc410c.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete |
| c:\users\user\appdata\local\temp\nsc4f65.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete |
| c:\users\user\appdata\local\temp\nsca8ce.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete |
| c:\users\user\appdata\local\temp\nsccda4.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete |
| c:\users\user\appdata\local\temp\nsd7eb5.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete |
| c:\users\user\appdata\local\temp\nsed622.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete |
| c:\users\user\appdata\local\temp\nsg3f58.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete |
| c:\users\user\appdata\local\temp\nsh4f66.tmp\installoptions.dll | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\nsh4f66.tmp\iospecial.ini | Generic Read,Write Data,Write Attributes,Write extended,Append data |
| c:\users\user\appdata\local\temp\nsh4f66.tmp\iospecial.ini | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\nsh4f66.tmp\modern-header.bmp | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\nsh4f66.tmp\modern-wizard.bmp | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\nsh4f66.tmp\setuplib.dll | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\nsh4f66.tmp\system.dll | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\nsh8e73.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete |
| c:\users\user\appdata\local\temp\nsi3592.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete |
| c:\users\user\appdata\local\temp\nskf2ca.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete |
| c:\users\user\appdata\local\temp\nsl2e95.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete |
| c:\users\user\appdata\local\temp\nsl688f.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete |
| c:\users\user\appdata\local\temp\nsm258c.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete |
| c:\users\user\appdata\local\temp\nsm47a2.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete |
| c:\users\user\appdata\local\temp\nsm8d5a.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete |
| c:\users\user\appdata\local\temp\nsn42eb.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete |
| c:\users\user\appdata\local\temp\nsn4423.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete |
| c:\users\user\appdata\local\temp\nsna8bf.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete |
| c:\users\user\appdata\local\temp\nsnaa45.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete |
| c:\users\user\appdata\local\temp\nsp3e0f.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete |
| c:\users\user\appdata\local\temp\nspf124.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete |
| c:\users\user\appdata\local\temp\nsq50a.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete |
| c:\users\user\appdata\local\temp\nsqbcce.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete |
| c:\users\user\appdata\local\temp\nsr303b.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete |
| c:\users\user\appdata\local\temp\nsr31c1.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete |
| c:\users\user\appdata\local\temp\nsrcc6b.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete |
| c:\users\user\appdata\local\temp\nss42c1.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete |
| c:\users\user\appdata\local\temp\nss4ca4.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete |
| c:\users\user\appdata\local\temp\nst4e79.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete |
| c:\users\user\appdata\local\temp\nstaa65.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete |
| c:\users\user\appdata\local\temp\nsv665d.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete |
| c:\users\user\appdata\local\temp\nsw2fbe.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete |
| c:\users\user\appdata\local\temp\nsw46a8.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete |
| c:\users\user\appdata\local\temp\nsw4e3c.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete |
| c:\users\user\appdata\local\temp\nsw5c2b.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete |
| c:\users\user\appdata\local\temp\nswbe26.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete |
| c:\users\user\appdata\local\temp\nswbfac.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete |
| c:\users\user\appdata\local\temp\nsx5f87.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete |
| c:\users\user\appdata\local\temp\nsy36da.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete |
| c:\users\user\appdata\local\temp\nsz806b.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete |
| c:\users\user\appdata\local\temp\nszd789.tmp | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete |
| c:\users\user\appdata\local\temp\~nsu.tmp\au_.exe | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete,LEFT 262144 |
Registry Modifications
Registry Modifications
This section lists registry keys and values that were created, modified and/or deleted by samples in this family. Windows Registry activity can provide valuable insight into malware functionality. Additionally, malware often creates registry values to allow itself to automatically start and indefinitely persist after an initial infection has compromised the system.| Key::Value | Data | API Name |
|---|---|---|
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Users\Iymsyzmq\AppData\Local\Temp\~nsu.tmp\Au_.exe | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Users\Iymsyzmq\AppData\Local\Temp\~nsu.tmp\Au_.exe��\??\C:\Users\Iymsyzmq\AppData\Local\Temp\~nsu.tmp | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Users\Zrvdxhvk\AppData\Local\Temp\~nsu.tmp\Au_.exe | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Users\Zrvdxhvk\AppData\Local\Temp\~nsu.tmp\Au_.exe��\??\C:\Users\Zrvdxhvk\AppData\Local\Temp\~nsu.tmp | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Users\Qdxjcpxi\AppData\Local\Temp\~nsu.tmp\Au_.exe | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Users\Qdxjcpxi\AppData\Local\Temp\~nsu.tmp\Au_.exe��\??\C:\Users\Qdxjcpxi\AppData\Local\Temp\~nsu.tmp | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Users\Uuxpsktx\AppData\Local\Temp\~nsu.tmp\Au_.exe | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Users\Uuxpsktx\AppData\Local\Temp\~nsu.tmp\Au_.exe��\??\C:\Users\Uuxpsktx\AppData\Local\Temp\~nsu.tmp | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Users\Jqdglvwu\AppData\Local\Temp\~nsu.tmp\Au_.exe | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Users\Jqdglvwu\AppData\Local\Temp\~nsu.tmp\Au_.exe��\??\C:\Users\Jqdglvwu\AppData\Local\Temp\~nsu.tmp | RegNtPreCreateKey |
Show More
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Users\Vkoquque\AppData\Local\Temp\~nsu.tmp\Au_.exe | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Users\Vkoquque\AppData\Local\Temp\~nsu.tmp\Au_.exe��\??\C:\Users\Vkoquque\AppData\Local\Temp\~nsu.tmp | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Users\Jkxzwnat\AppData\Local\Temp\~nsu.tmp\Au_.exe | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Users\Jkxzwnat\AppData\Local\Temp\~nsu.tmp\Au_.exe��\??\C:\Users\Jkxzwnat\AppData\Local\Temp\~nsu.tmp | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Users\Erueifwx\AppData\Local\Temp\~nsu.tmp\Au_.exe | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Users\Erueifwx\AppData\Local\Temp\~nsu.tmp\Au_.exe��\??\C:\Users\Erueifwx\AppData\Local\Temp\~nsu.tmp | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Users\Lifiovun\AppData\Local\Temp\~nsu.tmp\Au_.exe | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Users\Lifiovun\AppData\Local\Temp\~nsu.tmp\Au_.exe��\??\C:\Users\Lifiovun\AppData\Local\Temp\~nsu.tmp | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Users\Vxdzvfkq\AppData\Local\Temp\~nsu.tmp\Au_.exe | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Users\Vxdzvfkq\AppData\Local\Temp\~nsu.tmp\Au_.exe��\??\C:\Users\Vxdzvfkq\AppData\Local\Temp\~nsu.tmp | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Users\Vkvufnro\AppData\Local\Temp\~nsu.tmp\Au_.exe | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Users\Vkvufnro\AppData\Local\Temp\~nsu.tmp\Au_.exe��\??\C:\Users\Vkvufnro\AppData\Local\Temp\~nsu.tmp | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Users\Ofsegtho\AppData\Local\Temp\~nsu.tmp\Au_.exe | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Users\Ofsegtho\AppData\Local\Temp\~nsu.tmp\Au_.exe��\??\C:\Users\Ofsegtho\AppData\Local\Temp\~nsu.tmp | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Users\Pqehulon\AppData\Local\Temp\~nsu.tmp\Au_.exe | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Users\Pqehulon\AppData\Local\Temp\~nsu.tmp\Au_.exe��\??\C:\Users\Pqehulon\AppData\Local\Temp\~nsu.tmp | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Users\Brhdtktg\AppData\Local\Temp\~nsu.tmp\Au_.exe | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Users\Brhdtktg\AppData\Local\Temp\~nsu.tmp\Au_.exe��\??\C:\Users\Brhdtktg\AppData\Local\Temp\~nsu.tmp | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Users\Zyjbugdv\AppData\Local\Temp\~nsu.tmp\Au_.exe | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Users\Zyjbugdv\AppData\Local\Temp\~nsu.tmp\Au_.exe��\??\C:\Users\Zyjbugdv\AppData\Local\Temp\~nsu.tmp | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Users\Zkxetydt\AppData\Local\Temp\~nsu.tmp\Au_.exe | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Users\Zkxetydt\AppData\Local\Temp\~nsu.tmp\Au_.exe��\??\C:\Users\Zkxetydt\AppData\Local\Temp\~nsu.tmp | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Users\Zfqgpkkp\AppData\Local\Temp\~nsu.tmp\Au_.exe | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Users\Zfqgpkkp\AppData\Local\Temp\~nsu.tmp\Au_.exe��\??\C:\Users\Zfqgpkkp\AppData\Local\Temp\~nsu.tmp | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Users\Yhoyrddd\AppData\Local\Temp\~nsu.tmp\Au_.exe | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Users\Yhoyrddd\AppData\Local\Temp\~nsu.tmp\Au_.exe��\??\C:\Users\Yhoyrddd\AppData\Local\Temp\~nsu.tmp | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Users\Wueejtel\AppData\Local\Temp\~nsu.tmp\Au_.exe | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Users\Wueejtel\AppData\Local\Temp\~nsu.tmp\Au_.exe��\??\C:\Users\Wueejtel\AppData\Local\Temp\~nsu.tmp | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Users\Hbvnlwek\AppData\Local\Temp\~nsu.tmp\Au_.exe | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Users\Hbvnlwek\AppData\Local\Temp\~nsu.tmp\Au_.exe��\??\C:\Users\Hbvnlwek\AppData\Local\Temp\~nsu.tmp | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Program Files (x86)\Microsoft\EdgeUpdate\1.3.205.9��\??\C:\Users\Adrmktbm\AppData\Local\Temp\~nsu.tmp\Au_.exe | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Program Files (x86)\Microsoft\EdgeUpdate\1.3.205.9��\??\C:\Users\Adrmktbm\AppData\Local\Temp\~nsu.tmp\Au_.exe��\??\C:\Use | RegNtPreCreateKey |
| HKLM\software\microsoft\windows nt\currentversion\notifications\data::418a073aa3bc1c75 | RegNtPreCreateKey | |
| HKLM\software\microsoft\windows nt\currentversion\notifications\data::418a073aa3bc1c75 | RegNtPreCreateKey | |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Program Files (x86)\Microsoft\EdgeUpdate\1.3.205.9��\??\C:\Windows\SystemTemp\b1a39cca-eadf-4949-a384-a0ef6a3b3fd2.tmp��\ | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Windows\SystemTemp\77e37ce0-8214-4414-aced-551c5ae204d7.tmp��\??\C:\Windows\SystemTemp\e28eadcf-6ab0-4d8c-8821-7ce9a6aba1 | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | \??\C:\Windows\SystemTemp\a9dd6c3f-d641-4292-855a-e9c09c1b694b.tmp��\??\C:\Windows\SystemTemp\85968c61-a19d-4e7b-a80f-d2a1fc3c08 | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | *1\??\C:\sandbox_live\tmp\111621\7116\c\users\user\appdata\local\temp\~nsu.tmp\au_.exe | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | *1\??\C:\sandbox_live\tmp\111621\7116\c\users\user\appdata\local\temp\~nsu.tmp\au_.exe��*1\??\C:\sandbox_live\tmp\111621\7116\c\ | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | *1\??\C:\Windows\SystemTemp\2f634a6e-6b36-47d1-a032-04624398405f.tmp��*1\??\C:\sandbox_live\tmp\112682\5412\c\users\user\appdata | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | *1\??\C:\Windows\SystemTemp\MicrosoftEdgeUpdate.exe.old122e4��*1\??\C:\Windows\SystemTemp\CopilotUpdate.exe.old12352��*1\??\C:\P | RegNtPreCreateKey |
| HKLM\system\controlset001\control\session manager::pendingfilerenameoperations | *1\??\C:\Windows\SystemTemp\MicrosoftEdgeUpdate.exe.old5af52��*1\??\C:\Windows\SystemTemp\CopilotUpdate.exe.old5af62��*1\??\C:\P | RegNtPreCreateKey |
| HKLM\software\microsoft\windows nt\currentversion\notifications\data::418a073aa3bc1c75 | RegNtPreCreateKey | |
| HKLM\software\microsoft\windows nt\currentversion\notifications\data::418a073aa3bc1c75 | RegNtPreCreateKey | |
| HKLM\software\microsoft\windows nt\currentversion\notifications\data::418a073aa3bc1c75 | RegNtPreCreateKey | |
| HKLM\software\microsoft\windows nt\currentversion\notifications\data::418a073aa3bc1c75 | RegNtPreCreateKey | |
| HKLM\software\microsoft\windows nt\currentversion\notifications\data::418a073aa3bc1c75 | RegNtPreCreateKey | |
| HKLM\software\microsoft\windows nt\currentversion\notifications\data::418a073aa3bc1c75 | RegNtPreCreateKey |
Windows API Usage
Windows API Usage
This section lists Windows API calls that are used by the samples in this family. Windows API usage analysis is a valuable tool that can help identify malicious activity, such as keylogging, security privilege escalation, data encryption, data exfiltration, interference with antivirus software, and network request manipulation.| Category | API |
|---|---|
| Anti Debug |
|
| User Data Access |
|
| Process Shell Execute |
|
Shell Command Execution
Shell Command Execution
This section lists Windows shell commands that are run by the samples in this family. Windows Shell commands are often leveraged by malware for nefarious purposes and can be used to elevate security privileges, download and launch other malware, exploit vulnerabilities, collect and exfiltrate data, and hide malicious activity.
"C:\Users\Iymsyzmq\AppData\Local\Temp\~nsu.tmp\Au_.exe" _?=c:\users\user\downloads\
|
"C:\Users\Zrvdxhvk\AppData\Local\Temp\~nsu.tmp\Au_.exe" _?=c:\users\user\downloads\
|
"C:\Users\Qdxjcpxi\AppData\Local\Temp\~nsu.tmp\Au_.exe" _?=c:\users\user\downloads\
|
"C:\Users\Uuxpsktx\AppData\Local\Temp\~nsu.tmp\Au_.exe" _?=c:\users\user\downloads\
|
"C:\Users\Jqdglvwu\AppData\Local\Temp\~nsu.tmp\Au_.exe" _?=c:\users\user\downloads\
|
Show More
"C:\Users\Vkoquque\AppData\Local\Temp\~nsu.tmp\Au_.exe" _?=c:\users\user\downloads\
|
"C:\Users\Jkxzwnat\AppData\Local\Temp\~nsu.tmp\Au_.exe" _?=c:\users\user\downloads\
|
"C:\Users\Erueifwx\AppData\Local\Temp\~nsu.tmp\Au_.exe" _?=c:\users\user\downloads\
|
"C:\Users\Lifiovun\AppData\Local\Temp\~nsu.tmp\Au_.exe" _?=c:\users\user\downloads\
|
"C:\Users\Vxdzvfkq\AppData\Local\Temp\~nsu.tmp\Au_.exe" _?=c:\users\user\downloads\
|
"C:\Users\Vkvufnro\AppData\Local\Temp\~nsu.tmp\Au_.exe" _?=c:\users\user\downloads\
|
"C:\Users\Ofsegtho\AppData\Local\Temp\~nsu.tmp\Au_.exe" _?=c:\users\user\downloads\
|
"C:\Users\Pqehulon\AppData\Local\Temp\~nsu.tmp\Au_.exe" _?=c:\users\user\downloads\
|
"C:\Users\Brhdtktg\AppData\Local\Temp\~nsu.tmp\Au_.exe" _?=c:\users\user\downloads\
|
"C:\Users\Zyjbugdv\AppData\Local\Temp\~nsu.tmp\Au_.exe" _?=c:\users\user\downloads\
|
"C:\Users\Zkxetydt\AppData\Local\Temp\~nsu.tmp\Au_.exe" _?=c:\users\user\downloads\
|
"C:\Users\Zfqgpkkp\AppData\Local\Temp\~nsu.tmp\Au_.exe" _?=c:\users\user\downloads\
|
"C:\Users\Yhoyrddd\AppData\Local\Temp\~nsu.tmp\Au_.exe" _?=c:\users\user\downloads\
|
"C:\Users\Wueejtel\AppData\Local\Temp\~nsu.tmp\Au_.exe" _?=c:\users\user\downloads\
|
"C:\Users\Hbvnlwek\AppData\Local\Temp\~nsu.tmp\Au_.exe" _?=c:\users\user\downloads\
|
"C:\Users\Adrmktbm\AppData\Local\Temp\~nsu.tmp\Au_.exe" _?=c:\users\user\downloads\
|
"C:\Users\Lxqhsaae\AppData\Local\Temp\~nsu.tmp\Au_.exe" _?=c:\users\user\downloads\
|
"C:\Users\Pnnkcvrr\AppData\Local\Temp\~nsu.tmp\Au_.exe" _?=c:\users\user\downloads\
|
"C:\Users\Voiocfci\AppData\Local\Temp\~nsu.tmp\Au_.exe" _?=c:\users\user\downloads\
|
"C:\Users\Mjlmvbaq\AppData\Local\Temp\~nsu.tmp\Au_.exe" _?=c:\users\user\downloads\
|
"C:\Users\Znehiych\AppData\Local\Temp\~nsu.tmp\Au_.exe" _?=c:\users\user\downloads\
|
"C:\Users\Kfiwwrlv\AppData\Local\Temp\~nsu.tmp\Au_.exe" _?=c:\users\user\downloads\
|
"C:\Users\Litfstnx\AppData\Local\Temp\~nsu.tmp\Au_.exe" _?=c:\users\user\downloads\
|
"C:\Users\Efugpmtm\AppData\Local\Temp\~nsu.tmp\Au_.exe" _?=c:\users\user\downloads\
|
"C:\Users\Rhaeeaps\AppData\Local\Temp\~nsu.tmp\Au_.exe" _?=c:\users\user\downloads\
|
"C:\Users\Fdtgqizc\AppData\Local\Temp\~nsu.tmp\Au_.exe" _?=c:\users\user\downloads\
|
"C:\Users\Bwpnjxjq\AppData\Local\Temp\~nsu.tmp\Au_.exe" _?=c:\users\user\downloads\
|
"C:\Users\Qxkwkqrr\AppData\Local\Temp\~nsu.tmp\Au_.exe" _?=c:\users\user\downloads\
|
"C:\Users\Luemskjf\AppData\Local\Temp\~nsu.tmp\Au_.exe" _?=c:\users\user\downloads\
|
"C:\Users\Kyigghly\AppData\Local\Temp\~nsu.tmp\Au_.exe" _?=c:\users\user\downloads\
|
"C:\Users\Lumdusdl\AppData\Local\Temp\~nsu.tmp\Au_.exe" _?=c:\users\user\downloads\
|
"C:\Users\Phikgzyd\AppData\Local\Temp\~nsu.tmp\Au_.exe" _?=c:\users\user\downloads\
|
"C:\Users\Pgluclsv\AppData\Local\Temp\~nsu.tmp\Au_.exe" _?=c:\users\user\downloads\
|
"C:\Users\Ilwozmcw\AppData\Local\Temp\~nsu.tmp\Au_.exe" _?=c:\users\user\downloads\
|
"C:\Users\Maffvdne\AppData\Local\Temp\~nsu.tmp\Au_.exe" _?=c:\users\user\downloads\
|
"C:\Users\Qxvlkvyq\AppData\Local\Temp\~nsu.tmp\Au_.exe" _?=c:\users\user\downloads\
|
"C:\Users\Zpweeplb\AppData\Local\Temp\~nsu.tmp\Au_.exe" _?=c:\users\user\downloads\
|
