Trojan.Wdfload
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Ranking: | 14,495 |
| Threat Level: | 80 % (High) |
| Infected Computers: | 12,859 |
| First Seen: | January 17, 2017 |
| Last Seen: | April 2, 2024 |
| OS(es) Affected: | Windows |
Trojan.Wdfload is an extremely harmful Trojan that is used to carry out attacks on computer users. There have been numerous reports regarding Trojan.Wdfload, indicating that this Trojan poses a threat to computer users and their computers. Because of this, PC security analysts strongly advise computer users to ensure that their security software is fully up-to-date and capable of dealing with Trojan.Wdfload and similar threats.
Table of Contents
How the Trojan.Wdfload Infection Works
Trojan.Wdfload seems like a generic threat detection used by many anti-virus programs to indicate one of the numerous types of Trojan infections commonly. However, in the case of Trojan.Wdfload, this is a specific Trojan that was first observed in the second week of Jun 2017. There are several other names associated with Trojan.Wdfload, including 'CertLock' and 'Ceram.' Trojan.Wdfload is designed to infiltrate a computer and install itself in the infected computer's Temp directory. Once Trojan.Wdfload has been installed with a file name that includes a string of random numbers and letters (indistinguishable from many common Windows system files), Trojan.Wdfload will begin carrying out its attack on the victim's computer.
Trojan.Wdfload can Affect All Versions of the Windows Operating System
Trojan.Wdfload is designed to infect all versions of Windows specifically, including Windows 10, Windows 8.1, Windows 8, Windows 7, Windows Vista, and even Windows XP, which will be nearly twenty years old! This is because Trojan.Wdfload takes advantage of certain vulnerabilities that are inherent in the Windows system architecture that does not exist in other types of operating systems. There are many ways to distribute Trojan.Wdfload, with the most common being the use of spam email attachments, fake software downloads, and attack websites, which use exploit kits to carry out these attacks.
During its attack, Trojan.Wdfload will inject a corrupted DLL file into the infected computer. This corrupted DLL allows Trojan.Wdfload to exploit certain vulnerabilities in the Windows operating system that allow Trojan.Wdfload to manipulate security certificates, interfering with the infected computer's security and safety online and when installing any software. Trojan.Wdfload can be used to block any software running, as well as interfering with anti-virus programs installed on the infected computer. Trojan.Wdfload can be used to trick Windows into thinking that legitimate software and even security programs are unsafe, and vice versa, that threats like Trojan.Wdfload itself are legitimate programs.
Dealing with Trojan.Wdfload and Its Effects
Trojan.Wdfload has caught the attention of PC security researchers because it is simple, small and easy to implement. It also uses an attack that is flexible and can be adapted to numerous other tactics and attacks. For example, it would be simple to incorporate the Trojan.Wdfload infection into industrial espionage or ransomware tactics. Trojan.Wdfload can be used to make other threat attacks more effective and difficult to remove, and that is one of the reasons why Trojan.Wdfload is so especially threatening.
Because of Trojan.Wdfload been so problematic, PC security researchers strongly advise computer users to take steps to ensure that their computers are fully updated and protected from these attacks. Use a reliable security program that is fully up-to-date and ensure that this security program is capable of blocking numerous attacks, including those that originate online, perhaps from Remote Desktop Connections. Apart from a reliable security program, it also is crucial to use a Firewall and an anti-spam filter, as well as other security components that can be used to keep your computer safe. However, like most Trojans, the most effective way to distribute Trojan.Wdfload is through social engineering, taking advantage of human weakness. Educating computer users and ensuring that they know how to spot and recognize unsafe content online is the best protection against Trojan.Wdfload and similar threats.
SpyHunter Detects & Remove Trojan.Wdfload
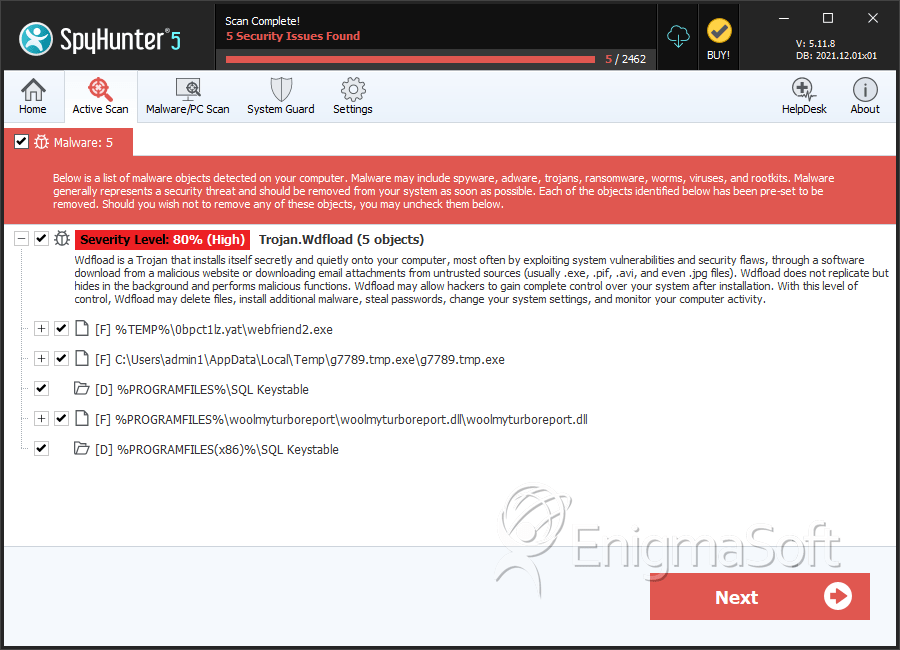
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | webfriend2.exe | 5d7ec0baaa26f766d88fec4af2d1257c | 49 |
| 2. | webfriend2.exe | 6a805384ec05737af818e4786be04fb6 | 36 |
| 3. | webfriend2.exe | f4f8bd68427f60b8186b00b7fc94cadf | 26 |
| 4. | webfriend2.exe | 7438698fe2fa1e945c91e189c80fa760 | 16 |
| 5. | webfriend2.exe | d36be2a7a50e76b9bb826a776ec9f5fd | 15 |
| 6. | g7789.tmp.exe | 766d5232cde530be672cdfd713c43596 | 13 |
| 7. | webfriend2.exe | a2e511ee4e61a87b0055ef1885e059a5 | 8 |
| 8. | webfriend2.exe | a0d6bcc2af34b9fa68bb4abe22485756 | 4 |
| 9. | woolmyturboreport.dll | 19e65228e04ad751ea81b9e7bdfee369 | 4 |
| 10. | webfriend2.exe | 561af8e9b994a14402e5b232ab7759ba | 3 |
Registry Details
Directories
Trojan.Wdfload may create the following directory or directories:
| %PROGRAMFILES%\SQL Keystable |
| %PROGRAMFILES(x86)%\SQL Keystable |

Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.