Trojan.Spy.Banker.VCM
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Popularity Rank: | 16,548 |
| Threat Level: | 80 % (High) |
| Infected Computers: | 11,305 |
| First Seen: | May 7, 2013 |
| Last Seen: | January 27, 2026 |
| OS(es) Affected: | Windows |
Table of Contents
Aliases
15 security vendors flagged this file as malicious.
| Antivirus Vendor | Detection |
|---|---|
| Ikarus | Win32.SuspectCrc |
| AntiVir | TR/Graftor.36646 |
| Comodo | TrojWare.Win32.TrojanDownloader.Dadobra.~JH9 |
| BitDefender | Gen:Variant.Zusy.12143 |
| eSafe | Suspicious File |
| McAfee | Artemis!6BD864794F9C |
| Panda | Trj/DataRecovery.A |
| AVG | PSW.Banker6.AHNA |
| Fortinet | W32/Banker.YLX!tr |
| Ikarus | Trojan.Hijacker |
| AhnLab-V3 | Trojan/Win32.Hijacker |
| Microsoft | TrojanSpy:Win32/Banker.VCM |
| AntiVir | TR/Hijacker.Gen |
| Comodo | UnclassifiedMalware |
| Kaspersky | Trojan.Win32.Agent.uign |
SpyHunter Detects & Remove Trojan.Spy.Banker.VCM
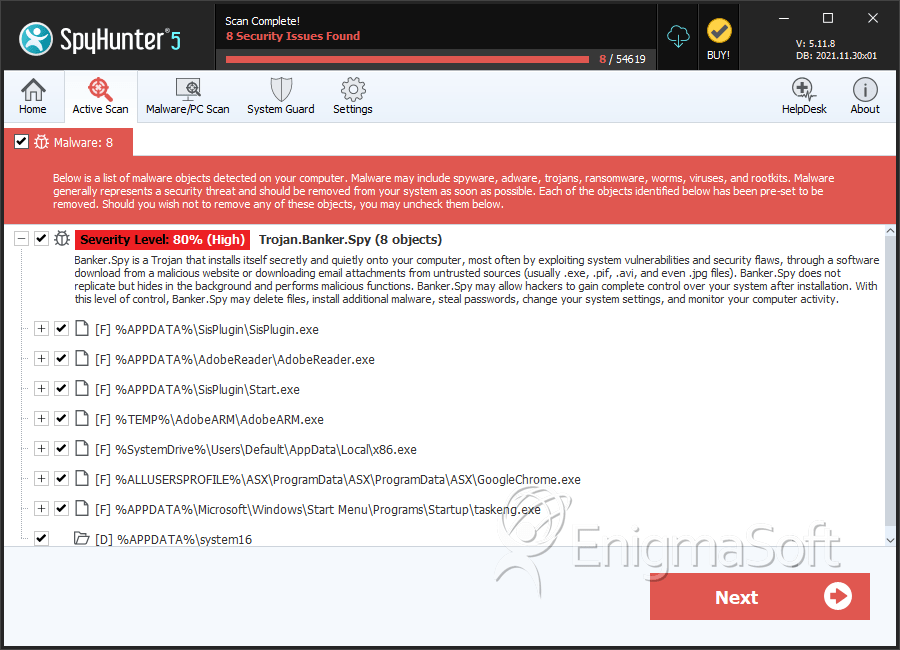
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | x86.exe | 8d5e5a55ae96ee0d4195c48a45f77dd2 | 196 |
| 2. | winsystem32.dll | faec0b184ca314e0966d3a9eb39b4c02 | 118 |
| 3. | AdobeARM.exe | 127c5ab208c8fbc3c8ade9b353f575c4 | 94 |
| 4. | AdobeReader.exe | 3cb8c0500d5437971368d470419b0774 | 71 |
| 5. | df8ece5a2847c8013d1ab852cafa8c927017ff1c94e4aa573528939e304b8442 | ccc6d03c91cb3f2c212c405576489e6b | 34 |
| 6. | Win10.exe | bb2bab235a48180d2a067dedf7bcbb26 | 27 |
| 7. | tHov8F2.cpl | dec4c99540599f9a7c6ad500ff7c2d8a | 25 |
| 8. | helpmng.exe | 1bbb6f292ef5faab7b941befb0272f0a | 23 |
| 9. | chrone.exe | 7e40c95391d71b0d1f7f18e953935bbb | 22 |
| 10. | Java.exe | 1aab17feb05b53f90e890412cb4ae202 | 19 |
| 11. | DealPlyIexplorer.dll | 6bd864794f9c26aa0af3f05a0295d5bc | 7 |
| 12. | IFrameDynamic.dll | e17b47cb66f255ec68b62a77dc9c5b73 | 7 |
| 13. | CortanaPTBR.dll | 48e0d99dba5a7d2f4bfae8ef30705e14 | 3 |
| 14. | taskhosts.exe | e7bed1becf1abbf0a8eeea84e90e54d7 | 1 |
| 15. | taskeng.exe | 938984f3f48d125ebf13ebf59724ae2d | 1 |
| 16. | GoogleChrome.exe | 5616f2099ffce9c922650fdcdf0662aa | 1 |
| 17. | Start.exe | ed9462a5a6f088081d5379abf876c5c0 | 1 |
| 18. | SisPlugin.exe | d9e91a176141ea6f3df64c2f49d2b38e | 1 |
| 19. | iOSPhoneProtect.dll | 68aba3d4eb40cd71eb6c7aa7973d6e43 | 1 |
| 20. | NativeDebian9.dll | 2813f64a6d13de2c18c68bea982ffc04 | 1 |
| 21. | banker.exe | b77925834fa4a5a72ea7c4ebfc92b3eb | 1 |
| 22. | file.exe | 142ebfa97041ca2beec66f9e8dfd07e4 | 0 |
Registry Details
Directories
Trojan.Spy.Banker.VCM may create the following directory or directories:
| %ALLUSERSPROFILE%\ASX\ProgramData |
| %APPDATA%\SisPlugin |
| %APPDATA%\system16 |
| %appdata%\SASD41310 |
Analysis Report
General information
| Family Name: | Trojan.Banker.Spy |
|---|---|
| Signature status: | Self Signed |
Known Samples
Known Samples
This section lists other file samples believed to be associated with this family.|
MD5:
ce88b3fa40e095cf69ebaab3e567aa9a
SHA1:
7f19ad248fa8a6a5b690f43d47205f9b9c3c6ea1
SHA256:
DF75AD44724F55947703272AD0026811C86473B324B1422EC1B99ADA00845C35
File Size:
7.64 MB, 7640408 bytes
|
|
MD5:
211e0baad67b127e75a0383659a7d1e1
SHA1:
1cf6bee8e24d85a26a495ded0435bdc972e3535c
SHA256:
0D6B7DE839BC56E3EBF79BE57836DA9A09FC4B11DDC22022F33F5CEB15D0F973
File Size:
8.67 MB, 8670224 bytes
|
|
MD5:
73c253c199e234784e56c3a53f6db92f
SHA1:
618ee80cb562d7532d67ac91a04d033a9e088801
SHA256:
2B816730BBEC5B6A1156D619B8BFAE26C6BB702ED04ABC9485FD366CDD457B38
File Size:
7.16 MB, 7159296 bytes
|
|
MD5:
2bcc8e39b6c9b6e7c3d4062a7f2d28d0
SHA1:
797ff21cbfe018dd68b7c0cbabc711d0f400f787
SHA256:
61AE9DECB301DEC97835B9D40F921049A6D6D6EC3E309A00B41FF5A06CC26BA9
File Size:
77.31 KB, 77312 bytes
|
|
MD5:
86c0da7452f8b7f50f7444ac9aa81057
SHA1:
266ab467f1027921868adf169f9ddf15d5bc392b
SHA256:
78CB60F2FF5CB03C02F43AF214104E74F263AB44335C7F1A09FDB1AFCCFD2B0C
File Size:
2.58 MB, 2582536 bytes
|
Windows Portable Executable Attributes
- File doesn't have "Rich" header
- File doesn't have debug information
- File doesn't have exports table
- File has exports table
- File has TLS information
- File is 32-bit executable
- File is 64-bit executable
- File is console application (IMAGE_SUBSYSTEM_WINDOWS_CUI)
- File is either console or GUI application
- File is GUI application (IMAGE_SUBSYSTEM_WINDOWS_GUI)
Show More
- File is Native application (NOT .NET application)
- File is not packed
- IMAGE_FILE_DLL is not set inside PE header (Executable)
- IMAGE_FILE_EXECUTABLE_IMAGE is set inside PE header (Executable Image)
File Icons
File Icons
This section displays icon resources found within family samples. Malware often replicates icons commonly associated with legitimate software to mislead users into believing the malware is safe.Windows PE Version Information
Windows PE Version Information
This section displays values and attributes that have been set in the Windows file version information data structure for samples within this family. To mislead users, malware actors often add fake version information mimicking legitimate software.| Name | Value |
|---|---|
| Company Name | Microsoft Corporation |
| File Description | Windows .NET SDK Generic |
| File Version |
|
| Internal Name | Microsoft© .NET Framework |
| Legal Copyright | © Microsoft Corporation. All rights reserved. |
| Product Name | Microsoft© .NET Framework |
| Product Version |
|
| Program I D | com.embarcadero.Prime989 |
Digital Signatures
Digital Signatures
This section lists digital signatures that are attached to samples within this family. When analyzing and verifying digital signatures, it is important to confirm that the signature’s root authority is a well-known and trustworthy entity and that the status of the signature is good. Malware is often signed with non-trustworthy “Self Signed” digital signatures (which can be easily created by a malware author with no verification). Malware may also be signed by legitimate signatures that have an invalid status, and by signatures from questionable root authorities with fake or misleading “Signer” names.| Signer | Root | Status |
|---|---|---|
| COMERCIAL LAR BELLO LTDA - ME:20432846000108 | COMERCIAL LAR BELLO LTDA - ME:20432846000108 | Self Signed |
| COMP STORE TELEFONIA E INFORMATICA LTDA - ME | Thawte Code Signing CA - G2 | Self Signed |
| M2 AGRO DESENVOLVIMENTO DE SISTEMAS LTDA | Thawte Code Signing CA - G2 | Self Signed |
| FUTURA SOLUCOES E TECNOLOGIA LTDA ME | thawte SHA256 Code Signing CA | Self Signed |
Block Information
Block Information
During analysis, EnigmaSoft breaks file samples into logical blocks for classification and comparison with other samples. Blocks can be used to generate malware detection rules and to group file samples into families based on shared source code, functionality and other distinguishing attributes and characteristics. This section lists a summary of this block data, as well as its classification by EnigmaSoft. A visual representation of the block data is also displayed, where available.| Total Blocks: | 5,431 |
|---|---|
| Potentially Malicious Blocks: | 2 |
| Whitelisted Blocks: | 5,424 |
| Unknown Blocks: | 5 |
Visual Map
? - Unknown Block
x - Potentially Malicious Block
Similar Families
Similar Families
This section lists other families that share similarities with this family, based on EnigmaSoft’s analysis. Many malware families are created from the same malware toolkits and use the same packing and encryption techniques but uniquely extend functionality. Similar families may also share source code, attributes, icons, subcomponents, compromised and/or invalid digital signatures, and network characteristics. Researchers leverage these similarities to rapidly and effectively triage file samples and extend malware detection rules.- Casbaneiro.A
- Casbaneiro.G
- Filecoder.PB
- Gamehack.ODB
- Injector.XN
Show More
- Ropalidia.D
- Ulise.BE
Files Modified
Files Modified
This section lists files that were created, modified, moved and/or deleted by samples in this family. File system activity can provide valuable insight into how malware functions on the operating system.| File | Attributes |
|---|---|
| c:\windows\syswow64\log\rundll32.exe.debug.log | Generic Read,Write Data,Write Attributes,Write extended,Append data |
Windows API Usage
Windows API Usage
This section lists Windows API calls that are used by the samples in this family. Windows API usage analysis is a valuable tool that can help identify malicious activity, such as keylogging, security privilege escalation, data encryption, data exfiltration, interference with antivirus software, and network request manipulation.| Category | API |
|---|---|
| Syscall Use |
Show More
|
| Process Shell Execute |
|
| Anti Debug |
|
| Process Manipulation Evasion |
|
Shell Command Execution
Shell Command Execution
This section lists Windows shell commands that are run by the samples in this family. Windows Shell commands are often leveraged by malware for nefarious purposes and can be used to elevate security privileges, download and launch other malware, exploit vulnerabilities, collect and exfiltrate data, and hide malicious activity.
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\1cf6bee8e24d85a26a495ded0435bdc972e3535c_0008670224.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\618ee80cb562d7532d67ac91a04d033a9e088801_0007159296.,LiQMAxHB
|
