Trojan.MSIL.Agent
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Popularity Rank: | 1,882 |
| Threat Level: | 80 % (High) |
| Infected Computers: | 48,653 |
| First Seen: | January 19, 2011 |
| Last Seen: | February 4, 2026 |
| OS(es) Affected: | Windows |
Trojan.MSIL.Agent is a malicious trojan infection which uses malicious tricks to download nasty malware threats from the web. Trojan.MSIL.Agent penetrates and installs the infected computer system without a user's awareness or authorization when he/she open unidentified email attachment or image, use instant messaging, etc. Trojan.MSIL.Agent is often bundled with free downloadable software or a malicious website you visited that set Trojan.MSIL.Agent on your machine. Trojan.MSIL.Agent may track your Internet activities, steal user names and passwords, credit card numbers and other private details. Trojan.MSIL.Agent is a serious threat for the PC system and has to be removed immediately.
Table of Contents
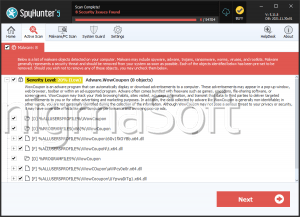
SpyHunter Detects & Remove Trojan.MSIL.Agent
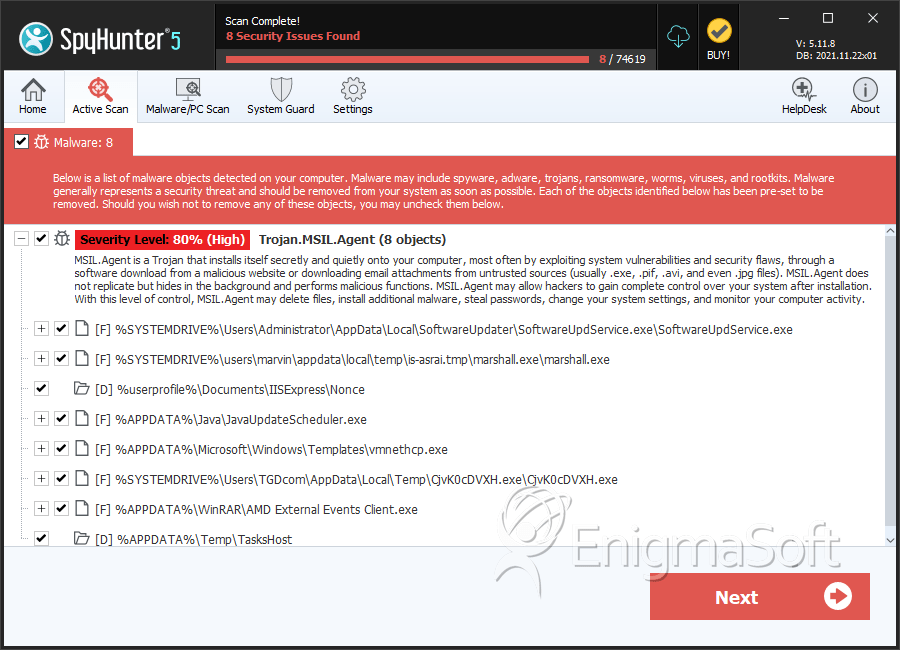
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | SoftwareUpdService.exe | 08ee53134d503e717b9913f15bbecd4f | 2,630 |
| 2. | marshall.exe | 979750935a9c5ae663c2ce1903c24385 | 1,879 |
| 3. | file.exe | 50c1eb3a826e5ac1438065b8e67279a4 | 459 |
| 4. | CjvK0cDVXH.exe | 5488a8d14687c9e6ab0444ce895980c0 | 159 |
| 5. | MicrosoftcriticalUpdate.exe | 51b4290905850a74f321abfd4826f790 | 77 |
| 6. | AppVShNotifyt-t.exe | 0b925cbf8479752674161740b0a3e30f | 56 |
| 7. | vstools.exe | a3e71acf4cb478d9d108d393f65017d8 | 42 |
| 8. | MicrosoftSecurityClient.exe | 3c7a1e9c0a5bcb84cf0c1c045f518178 | 36 |
| 9. | Windows10.exe | 4887164f96bcf1db190d7478f2e86649 | 32 |
| 10. | JavaUpdateScheduler.exe | 8c41c22508935974cc00098e1076d1a1 | 26 |
| 11. | systemstr_Part1.dll | b841325c980d8fb926a41dc6ec4db8f4 | 23 |
| 12. | thostmgr (1).exe | 8ac35832dbbf69db8ed01bf732dfa0a0 | 10 |
| 13. | System Disks Storage_Part1.dll | 4ea010bdcbf011e94c9da553eca8b7b2 | 4 |
| 14. | iepv_setup.exe | df6e95971e700f2a3231ee0366b92cf6 | 3 |
| 15. | Files Manager_Part1.dll | a9ae84d53c70fffbc9becddffd7f498d | 3 |
| 16. | 5beaedad620926c7d78777eeb702b8a1.exe | b5ad362fe8b6f4ada91b84d9bf3eb8a8 | 3 |
| 17. | Audiodb.exe | 61f0565f425d0bb28ea3d4790012876e | 2 |
| 18. | AMD External Events Client.exe | 198334f72d90083282b685fe647f4776 | 2 |
| 19. | thostmgr.exe | 31f044b4d7d921ac3e86842b366a424b | 2 |
| 20. | mdn.exe | 6f7ae7991e1dd6c0a1c8153e61bd378c | 2 |
| 21. | cryptedstealerserver.exe | f20327c8bd7c272f82a3fa62ab858cfb | 1 |
| 22. | vmnethcp.exe | 0514e0c508ad1e140a1d76d11b5bf38c | 1 |
| 23. | viafile.exe | f37d28e6663b0ce28f6c4f59294e3dd6 | 1 |
| 24. | sourcehash{8220eefe-38cd-377e-8595-13398d740ace} | 263ab98632ed4c32a7f3af02de7f080b | 1 |
| 25. |
C:\Documents and Settings\ |
||
| 26. | %PROGRAM_FILES%\Trojan.MSIL.Agent |
Registry Details
Directories
Trojan.MSIL.Agent may create the following directory or directories:
| %APPDATA%\Temp\TasksHost |
| %APPDATA%\ViaFolder |
| %APPDATA%\kna |
| %userprofile%\Documents\IISExpress\Nonce |
Analysis Report
General information
| Family Name: | Trojan.MSIL.Agent |
|---|---|
| Signature status: | No Signature |
Known Samples
Known Samples
This section lists other file samples believed to be associated with this family.|
MD5:
8d1a3de02c2de3d669a06e84f0bf4545
SHA1:
7a6580a3d4803890021e3e531f7fa7590dd14d21
File Size:
3.37 MB, 3366912 bytes
|
|
MD5:
16b985720bbd490bae3658136cae6f4f
SHA1:
7d94de346f5485f0d10272bd67ab406236dbe951
File Size:
8.16 MB, 8161792 bytes
|
|
MD5:
612744d80bb10a597740bdc23fb71f73
SHA1:
ac8400b48c8bba2a650d76496af4b0923cb93e85
SHA256:
7FBEA844155B35614238423BA4411C163C4A92CF0CD38D32001514F923A0C83D
File Size:
137.73 KB, 137728 bytes
|
|
MD5:
7e4c6fd9b32ce3630e0530053bf4efb4
SHA1:
0f23eab69d9a7a5bc4cc2db48a1bb06382987c27
SHA256:
217F3F64278A8B95BA335790A09E9204F0877EE451B571F1C7AA1E436561098C
File Size:
127.49 KB, 127488 bytes
|
|
MD5:
b185c0e04d36d030246181f62a63549c
SHA1:
c0ecce0784902b15822340955bf3a350de52681e
SHA256:
1728514F39F9F9871E10793978C41AD5E91E3F40CE87D4EA11A9BE16251059E5
File Size:
350.21 KB, 350208 bytes
|
Show More
|
MD5:
05cc1bd1f4060a3ee7d17314bc1d56e3
SHA1:
eb99b05eb4fcb1645541ecfd113a1c7569017f39
SHA256:
866F228000E83113894AB5E9F35379C8C618C9C276497D7C141DBA4EFDEF812B
File Size:
143.87 KB, 143872 bytes
|
|
MD5:
102115da485a7c0447eabc54f4ec2616
SHA1:
41d29a124519216bd70d5e8dd51a950bd042b370
SHA256:
D6025982D3901D53FDB0DC195BCA3C1CF595935C0831E978A201C2BA8EF117CE
File Size:
118.27 KB, 118272 bytes
|
|
MD5:
4d18463f474f6ec8c6f504fda96c326f
SHA1:
f0ab35f6b85d7b8c44454084d68a929d78b2f645
SHA256:
E094309A557A800CD0752A64C84DBBD87762FA7925878167356E5AAB52E813D5
File Size:
139.78 KB, 139776 bytes
|
|
MD5:
b716d9cabdaa337dc2403df59708d3ca
SHA1:
b64fab7b7f309ba676e8f5903a4bb0939d803fae
SHA256:
5D729456776174781C21E32AAB151B5F2A54E9D2EE7B953FBE2EBCC55ADBE91D
File Size:
151.55 KB, 151552 bytes
|
|
MD5:
c89b1f7a2a03497c0974c4394f9b9f17
SHA1:
bb8431c5fc572b8a0c6f8cfb6e5e2c5a44737dac
SHA256:
35DFAF13327A885A4CB48672D490CF1E6BCF58526D3357B6D82E37DAE77B7C41
File Size:
146.94 KB, 146944 bytes
|
|
MD5:
22d1c56ddc62b0ee775e71de6678af52
SHA1:
648c2bb8ff522422d5077e0788fe8d797ddaa1d7
SHA256:
2893667ED2541F32738AB5D49B7B10579ABC97059FD4AB064FBA8C2BD533963F
File Size:
136.70 KB, 136704 bytes
|
|
MD5:
736adc3c7df182fe784ffc7ba853c3f8
SHA1:
319acf0a7109f2ae2c41cd5bdc61c7a608c22628
SHA256:
3E29F46D2220FF096417B38738C4AE98C69FA79CB82691EA9425B61F3FC79548
File Size:
151.04 KB, 151040 bytes
|
|
MD5:
e923039eb0b724729854dcd3e414b61d
SHA1:
331b48846e1040ce59004e1db1eeb947499c33ec
SHA256:
2E49C41A69042F067D287D845BE4B376872BD44047D94E3362AF98C051D2304C
File Size:
142.34 KB, 142336 bytes
|
|
MD5:
202b3c972cec94b8fa0fa4c6aa055b2d
SHA1:
c0f592c493be8785e9ba468008e4e4205eca3cc0
SHA256:
59EDFFC957D3E4179D458DB862F2FFAF77FF1194752225725C52C26FD4C96CE3
File Size:
75.26 KB, 75264 bytes
|
|
MD5:
e5c1909458424224885361c33373b6c4
SHA1:
590fad56c274a3869156ee6d09911f7b0b81038c
SHA256:
818233B82174D48680332BE7932783E7F2326CCEE3EBA56F80CB0B376076E8EA
File Size:
139.78 KB, 139776 bytes
|
|
MD5:
e0c84f57b205d9b83d6b340f6e19d8c2
SHA1:
824f26e6a69b93c954c2719075c7c838d5c01ad3
SHA256:
4DB4AFCCEC4860A92F26B03159E6DEFB2A09FEF3293E8DE244D80982F188131B
File Size:
141.82 KB, 141824 bytes
|
|
MD5:
b77d3690e8e7cdcd1f78935e0dab13ab
SHA1:
5dcd2fb42752ae911fc5a86438a7488b875b2bfc
SHA256:
0BF30174A66DAAC4A418B9CE2DEA4C54C30B1AC350C40E698927B8EF445003B5
File Size:
56.83 KB, 56832 bytes
|
|
MD5:
8c8f4416e0ee509949e1591253d9bc76
SHA1:
db0b8542aab7a7232ddb709d1da0dbd35a2d67f0
SHA256:
45940C86813388A3409F06AD4A808C3BAFB1A409EEDA2598F6FFD43E393EAD7E
File Size:
138.24 KB, 138240 bytes
|
|
MD5:
c858b339d5c8006f9278795231907055
SHA1:
64a9422d125776f24c0e690052983055cd4f6a38
SHA256:
7DAD5BA0C8CC0DDFDA6A9F7A641DA62754694C6AC0ED8835B3A80B97C6CD6EF3
File Size:
116.22 KB, 116224 bytes
|
|
MD5:
a057c1bb6264134d191005b030d633e9
SHA1:
cb366e2c644a48f1179d31479973ed34c24841b1
SHA256:
B57CECCC08FCC0D788D52F88D887681953F7523CB61DB753B6CA03530533FBD6
File Size:
155.65 KB, 155648 bytes
|
|
MD5:
033fcedb7152ddb87a9e0261a1a94f94
SHA1:
2aaa8b24f951b35cb6d781285ff96792ecff8814
SHA256:
A443D306D97136E8764E232760BE054956E7483306270DDC190BEF5D3DACCEC2
File Size:
143.87 KB, 143872 bytes
|
|
MD5:
41dedb8ac031fd83c5ddefa04bee09c0
SHA1:
c6aaa3e6263c12b55af7ce2a3f609573d675e7e1
SHA256:
420B4C13F3831ADB4F92DF5F85D68586E2737468464BF752E5F9B30AC9FC26C5
File Size:
130.05 KB, 130048 bytes
|
|
MD5:
b2856ed912bc7f03adcff435094a042e
SHA1:
b5fb6bfe548075f1915a61499e9820a61141806d
SHA256:
165264E5628E85D05FFAE99E69A0E3E99B6AA6DFDC0ED81275B0FCD38F200799
File Size:
133.12 KB, 133120 bytes
|
|
MD5:
642bf5429cbc4aeb295c34ca297eed00
SHA1:
5c51d88d435ffdcd7cbf6556f9d9edda410924d5
SHA256:
0BBBAEE99848AC962CC0C9EF614D6F0374F2A72DDFB77324577866836C213719
File Size:
145.92 KB, 145920 bytes
|
|
MD5:
71f73bb2ae94f7878c5dad9bceab70b8
SHA1:
ccadfcbd4c68a77155d2bb38bc8b1708434247d1
SHA256:
02B3446662B502518FBCD7AD73D740B401C3460B52C50F3C216C240A3E436CDF
File Size:
145.92 KB, 145920 bytes
|
|
MD5:
1b63974a3518b679b05833623ae1adaa
SHA1:
6dae3debfafc7e3eb5c7e5fbf1cb1ef094adc2f3
SHA256:
9834EEE6908E89EE01570F7FB0ADA562844F9756F01BE054357645B1A71FE5E5
File Size:
148.48 KB, 148480 bytes
|
|
MD5:
4b5f4e78d3fd5dc42fe078a3171b712a
SHA1:
666271f9934de077e2dd103177a049564a15af1b
SHA256:
01C7D2F2F1B4085B526755297BA87191CDF240A2F8ABBFD652F4DEEC17165F16
File Size:
140.29 KB, 140288 bytes
|
|
MD5:
d18574870aacdf81606c773d65bcbe88
SHA1:
db2732e26e44496b03851490d886d724d3809d55
SHA256:
65DE567C77B5BF318E6D8A70E5F67311275BCFD147C44ECD45520D40D0C8A8BD
File Size:
119.81 KB, 119808 bytes
|
|
MD5:
5759aaf782211afbb3658fc89f2219a4
SHA1:
0f560e5650acf93a33ecea809a88a1c2bfb7c894
SHA256:
8E5D37B35366DBB7A6E5399D9C4AD23F4FC9759000CF2900C3D8946A28464D1A
File Size:
146.94 KB, 146944 bytes
|
|
MD5:
af47c7b23db077f80df8ec79ced0df7f
SHA1:
5d2ccbc695550e916f002dcb663a94f1a20f6306
SHA256:
E6F809F92600197B10252B058B43A29A8EC302AC333DFF02A7B1536B68C3B7B3
File Size:
148.99 KB, 148992 bytes
|
|
MD5:
c47dc2ae12243ffe80be5527c88f7fb9
SHA1:
4b6b299707e85f1cc37e81091e79b4e5ba54331d
SHA256:
A174E5697803DDDE55D9665493CE6FB9E4435BA0343DFC4AB5486015D348728F
File Size:
146.94 KB, 146944 bytes
|
|
MD5:
700f80a2a2a41e018bebf536d4490a6c
SHA1:
fa5d93319500648e52ffb35edab7966af7a6de49
SHA256:
2774832FE714394756670AA85EE7A8ED23855DEE6A2C69F2D80D2EC48F75D2DC
File Size:
2.60 MB, 2597888 bytes
|
|
MD5:
5610723882b2ab46405a47cad8bfe1f5
SHA1:
d7daa608246b3cb5c450067c7a6386b6127811d5
SHA256:
69E9BC3B70E510A1AB48E46AA97BD9C173B59D4E46F27CAB4B01C6D9F5456589
File Size:
142.34 KB, 142336 bytes
|
|
MD5:
8af84e674dd96c77fa845ef6bfb82772
SHA1:
43c961d7f8edff70ea9b32e42886e1f767d0f480
SHA256:
7E6A174F7E86779C244E108A3B5B86F999B0740AE850FC17BE2B6ED0FC43C58E
File Size:
135.68 KB, 135680 bytes
|
|
MD5:
333aece118f6d16f9dcdf2681a1d5253
SHA1:
c2a339bff70735d5b55acb9be1724bbb8a44e1a8
SHA256:
48D4D789D6FC7F41C3A3CB17479709404F0A5B43CC7BA2E6EC64D9F4F4B1B839
File Size:
134.66 KB, 134656 bytes
|
|
MD5:
9a34aa302619aefd5930d8e4c638cff2
SHA1:
81759aceb6881812d8087decd39f060142009855
SHA256:
0A643A0DA455020A3907785385301B2BD35D6C4F18787D2115BA4D00D0892496
File Size:
149.50 KB, 149504 bytes
|
|
MD5:
87abe801532cb7d4fd7c95f3383ba038
SHA1:
2200bea9666e611a44fa81c5598cf81301f82470
SHA256:
92BA1F245EA74BCD751D073DE1CB28002F3D5551D95225B51C904868C74FD9EC
File Size:
150.02 KB, 150016 bytes
|
|
MD5:
cdb7be4e255b6cf490f4bf8402cbd9ca
SHA1:
a207a6a1adf38aea2300f8e7e7306a60a6e6df2c
SHA256:
60C5143E7FAE58C8507F8F1BC53893721AA7BF72572CDDE8B1B359312A4FC903
File Size:
144.38 KB, 144384 bytes
|
|
MD5:
bdce362896bdf8ba854e89c0bd3d58d5
SHA1:
32c8bbd8eab65a4def952bdf35e9d1c159da49bb
SHA256:
0A89C45C8E2785E83D75DAA406660D6948A46408D5E6F58499137EE30A5A6541
File Size:
150.02 KB, 150016 bytes
|
|
MD5:
f03620d595f1175e2266d03e5a26ca0b
SHA1:
bb5a34de78a635a653d5038e9030053c75519b66
SHA256:
C65A88F3DD2B1688EB335C78F10F2C71013977A770C77AC2CBCC0AA3B7F862FF
File Size:
6.95 MB, 6947613 bytes
|
|
MD5:
e607beeb06f9467b532056eb2858c3e8
SHA1:
4a7ae1e4af5d28d92689d0c7df118983a5da6647
SHA256:
C5E8FE7593D2EBF3990151C678A4E642A32B49951720C4B4D6A265CB4147A77E
File Size:
153.09 KB, 153088 bytes
|
|
MD5:
d2e02404874e9f248b8debe4458fc6e7
SHA1:
f66505b302264de81c8f4331a0112cc137e1eb4c
SHA256:
81529D747F9848EDEE54C92A5B5B6058DD6285A4DA1CDB345AA7B308AFD54CD1
File Size:
156.67 KB, 156672 bytes
|
|
MD5:
60557686f47103f8234147b5c4697fc2
SHA1:
adae4d57cf458a36f0450b99b2b078af96000343
SHA256:
B005FC9E1F948913D8215E63348DEF1A96681116B899CF957510D2304312F115
File Size:
152.58 KB, 152576 bytes
|
|
MD5:
0ea18363517f9e35eb372a2ec161cac4
SHA1:
89ca06daf2003776f9e988bba646b789b7e69626
SHA256:
83AB1717597AD2541158F1BCB57B05925E5E4E17E0E2BCDCBA4D28A8C66228C8
File Size:
135.68 KB, 135680 bytes
|
|
MD5:
8243e009e18f458a00f49d4e74314ba1
SHA1:
c71a31eeedb6c969d5724542b014a380fa1a119d
SHA256:
60F6D3C4DD0F669564A4D2B92B796D26F3CEEFF9FE78AA98CBDB7794C0292A55
File Size:
133.63 KB, 133632 bytes
|
|
MD5:
1e2c9bb28b0a41dc870716bb67b36faa
SHA1:
6cff4cd52bbd39c6566e259ca016a10b9d254181
SHA256:
E868737033B7C2E67464F78AD48451126FE960B25D47D9CAE8DC601709B4F31D
File Size:
115.71 KB, 115712 bytes
|
|
MD5:
da6958528374516e825b74c27c1ec766
SHA1:
c4f617f917a69d5f78b5cafb9ec8f9dd92ef0720
SHA256:
4E476D997C04C2FED9625A731510B1BA6A6501AABF42D9F1CA2404CD8408AF11
File Size:
126.98 KB, 126976 bytes
|
|
MD5:
21539cad85fd5155a8d348351d64654e
SHA1:
48fd581035aa7a990ab324be8623736342b71a9b
SHA256:
B3EE918F0AEB7D09B2F632EFDEFEABC8F55A7442107EE3304ADEE8438CFD901B
File Size:
134.66 KB, 134656 bytes
|
|
MD5:
c3fdf988c1b86fdcfe0d4bc81150dbdf
SHA1:
73c3c1a17feb3ad8a9cbb7acd47e77e6bf526275
SHA256:
FB58A28362961D01438B876AE1E62702A937888E3AD3CF8F68D43D478B36AD0A
File Size:
136.70 KB, 136704 bytes
|
|
MD5:
e90c2494b63b7eb95260be96cc25e6c7
SHA1:
9d96f7f54d7dc34c5f065583b726d63cd41b481c
SHA256:
8A5AB53ABA26FD5B458056692E58C4FA82B9CCC95938552C055F6D8E0EF7F129
File Size:
147.46 KB, 147456 bytes
|
|
MD5:
0c67a8a444abe05518655c0497076cad
SHA1:
1952f9cd53a9e109fd8c18b7d497f85d481591a1
SHA256:
8A4790E312756BDF49B296689584E423D04D79469FD8CC138043428FD722DEC4
File Size:
137.22 KB, 137216 bytes
|
|
MD5:
7d442af130d537726b84720518053ac8
SHA1:
53a15d4ce5122027fad9e6215e56e4f2c1fe0872
SHA256:
1E2927F7B2E36D54C283E4C3AE8E5F2D05B6F431D9D96BC11B62B3C9F7D347D7
File Size:
129.02 KB, 129024 bytes
|
|
MD5:
8b8cb745dcdbff71edf8390f52167009
SHA1:
6634cef5c1a9ed0f12ae0a5d44bae42bb6018b07
SHA256:
AC797A73D3014092A2B5ACFF534B67A18D30F275F24E909CA5F2B7F01CD493B1
File Size:
141.31 KB, 141312 bytes
|
|
MD5:
a2f6d5e62983cfcbb5568aaf4b56f2e0
SHA1:
9845431ac0180e23815a548672f8a1303216c1e7
SHA256:
EBCBC39DEA3190C6DA157D1AAF86A5AD7C38C88616E5C6905B0C84E2D2544F43
File Size:
199.17 KB, 199168 bytes
|
|
MD5:
4c4fcb1b8b51d6d852d5371d8681168a
SHA1:
4f9d15d5221558acf7d42f3346a0d456520b8ffb
SHA256:
95C74F2ED8F39DD334C2013BF74C4C3E0C36F22ACFF463F9A3EF85FF8E6A75FA
File Size:
140.80 KB, 140800 bytes
|
|
MD5:
385104cc40bfaf00d21462cc455fe342
SHA1:
33aba85a0f62e0a9619ba88c6c83f06867bf8c02
SHA256:
05196B62B05577319410D83E5F557AF0BF6CF69CEF89A3D6EC0C59CB8601E533
File Size:
153.09 KB, 153088 bytes
|
|
MD5:
31785644f849c62e51b0086de5f685ae
SHA1:
49b55ac6d8bcea09aef06f8045e7c998700f22d6
SHA256:
235DBEAFE54DF2FDA8FAB938BF4DF6DECCE01A75194B7BCE76DBA3B69FA98AEC
File Size:
127.49 KB, 127488 bytes
|
|
MD5:
c27c1953175085938523a2d54b162453
SHA1:
9be94409a9c7cb04ceec0d5910929f4f1cfa1c1f
SHA256:
D299AA46682FFFEB844D4DC524D8344E68FDBC68B9F4043DF677D8E1AC39B5C9
File Size:
148.48 KB, 148480 bytes
|
|
MD5:
57d96c6f439392fe3f66c7a465852a18
SHA1:
dee487c15acb33e9966bc46e50305e67781fccd8
SHA256:
DBB0D06E83D7A917E4A77C8881C8DA41789F576CA3BD544E6842AAF32DCA0B5A
File Size:
141.31 KB, 141312 bytes
|
|
MD5:
c8d7cf0254f9235d2151e390839e676b
SHA1:
81e1b304740a77e864879a076ce3063b16162451
SHA256:
60A5272A3FAE193F6F4B5F96829CC86C38AF9446EC974DE87CF3909E4C462FC4
File Size:
154.11 KB, 154112 bytes
|
|
MD5:
5c54767681b5e98ce2dc50769b313068
SHA1:
34c3f3eda73f9554e20fd1f0a5916c85c24e424d
SHA256:
CD8D2099C0B8A4C8FA107C114CD575325B6C3876667CB5BDC75881E0FF2F9AF7
File Size:
144.90 KB, 144896 bytes
|
|
MD5:
952505fdc6ea4cc988df7dd94afe85e1
SHA1:
d9ad26ff411234e1852c56fb58ee3214a0e19759
SHA256:
CF614DB6889BC7DCE99D726498B517C78DE10CE345380B26FF639FD734F2236B
File Size:
130.05 KB, 130048 bytes
|
|
MD5:
80d99cf33411fa2a4b6a8dca6ecebb24
SHA1:
49432882369280950bf8bc1876f465c448f3aae3
SHA256:
2FABFFBC9E49AA9D4EE07E7E438FC170135E9295F89095F52E0BF85CC71E4E12
File Size:
153.09 KB, 153088 bytes
|
|
MD5:
2e9148a94ae0ec3f0b054f0849d27510
SHA1:
f3d4019071063776bd1e34a2f1bf3b06cf66f937
SHA256:
15A07505973774113725E309849C5D246CEBA0D5328792E0DAC29A2DB1CC9A7C
File Size:
382.46 KB, 382464 bytes
|
|
MD5:
fa4bb82dd3bc0032bef5cda03f0208f3
SHA1:
5b96e2735f9af5a14fc8dbf617440bcd882954f4
SHA256:
A6135E632583F6A443839DACEF8BB1B17FB30118DFE3E9D4BBCE9B8807189EA0
File Size:
139.26 KB, 139264 bytes
|
|
MD5:
61a97778427fd462145806f13722b212
SHA1:
d1d074568694f78c03db47cb571aac62964e565b
SHA256:
4D53FFA657EFDD7A0DAD4DDDF98D490B3841FCD4FFDBC49394771BECC58EAC35
File Size:
133.63 KB, 133632 bytes
|
|
MD5:
90041981b9ed816c18b0760948314e25
SHA1:
372f0aa50350b580cc5a1b1ff2854362eb9f906e
SHA256:
B2F844AFF2533DD21A2E0900405BEA9C655974C1930BD185CB7A90DD22913C59
File Size:
120.83 KB, 120832 bytes
|
|
MD5:
8f40d4f058aee476ec6c526ce4e25592
SHA1:
115dcfefcff58169f39347147470679dea19daf3
SHA256:
502CE6D6BFA5AC785039777829046BC5959BE29DDA7BF766A1C387EA1DAA507E
File Size:
141.82 KB, 141824 bytes
|
|
MD5:
806ce03cd2f5f73a555cc31a144ffcf4
SHA1:
1733b1e104be689cac5d5aca36bae45fd1fe9b31
SHA256:
6B6FBD076920269FFA9CC85206F1C9CF3E6AC923363704716AC2FE87A1E3BE3C
File Size:
156.67 KB, 156672 bytes
|
|
MD5:
89a2f3604b45f8d86bee4c7da95686ee
SHA1:
b3ea979c50fa78e6614c520a11d3952e6806d58b
SHA256:
F2B27C5C9E7F9D79BCFEBD13F0CBBE8477E97A04AB35418B7341F2BA1D268EE6
File Size:
168.45 KB, 168448 bytes
|
|
MD5:
7c858d00801b92ac58cc0938a5b61765
SHA1:
52b2ee6ce4aafaea9f1620695170df3880d3418b
SHA256:
D767F0D7EF16F7EFA6781933BFB7C98BD3BD01C4F679B9D35B2C85195F7B8D49
File Size:
132.10 KB, 132096 bytes
|
|
MD5:
5a3e0c7876f07da106d6e9efc5bf6d5f
SHA1:
6ac63635f3033e97aeb32633e73751cf27152322
SHA256:
3A24296169C740838799B1D76229DCBE2EA17AAECA6A1ED274F412A6B4B40166
File Size:
146.94 KB, 146944 bytes
|
|
MD5:
68ce65b48ffb604879688cc0191d082b
SHA1:
581baa137028937f903edc002308d5945c1dade6
SHA256:
6B330BBE258AF0BEFB3B59883BA52F73E1C4C93013ACFAFF057F270D03E2DB1B
File Size:
150.53 KB, 150528 bytes
|
|
MD5:
ff96da726099d635a270f3a7ee7963bf
SHA1:
5dc0772268c30c243c46014b9d827be7409cfa40
SHA256:
2DC6CDC07ED83DF53CBC47D53525D36120855B3251F68E77106F265825970CD2
File Size:
158.21 KB, 158208 bytes
|
|
MD5:
9226ce4d02ad6da0d96dd2f8b065c87d
SHA1:
df9ececda4cad75189db25930a0566dc2386fa42
SHA256:
E62C2A5F834AD1204ABAF69E4687E10AA199717757E329501F0F71DEDDC93BE9
File Size:
133.63 KB, 133632 bytes
|
|
MD5:
afb185eea1e16e8e317ae2552172c5fd
SHA1:
e9fb89dc89e19c264ebc2021a1e2480eab20cbe0
SHA256:
8633974381F75DF055AE7DD47411C1F9AE7BA9B162EDC3D7EE48B3D296BC7BDE
File Size:
141.31 KB, 141312 bytes
|
|
MD5:
4118e780f3e04fd4e1ea677f82e6ec85
SHA1:
6954343fb92928f849cf91daee3529fd284cce5f
SHA256:
C5976B71F73503387D9577ED5E68F1B1A5D29D3F7DD5D31450BEA38F30286232
File Size:
179.71 KB, 179712 bytes
|
|
MD5:
226fd199bcbe635f45be0e96bb4c5f1b
SHA1:
20cbd90ed699016db99129cd310db3344acdf0ee
SHA256:
00067EF09C64C4441B628B6CDD9AF18B5C4FC517A3DC2BC7B6750D655F6F7C80
File Size:
156.16 KB, 156160 bytes
|
|
MD5:
04c1d1cd3cfb468de0a3c62080432e6b
SHA1:
1ddec97ec79f8aa5d5d13975abae821e3221db32
SHA256:
8CC5D0A6AA6C89068EBDF5D50E1DE07149893228661A0314C78060D346E232E3
File Size:
147.46 KB, 147456 bytes
|
|
MD5:
dc90a5ec4be9bd362e3e4084f01009aa
SHA1:
6285fab51fd0bd2b1d1b0780ed9535054206cfcd
SHA256:
682663A57B0E24C8CFC9991846446EB832C98D6B565CEC9DA848D39E1235EF28
File Size:
139.78 KB, 139776 bytes
|
|
MD5:
dd7e31b94b37e99575cf6b52aad3ad50
SHA1:
7499ad1b41530310e4c1de18a8a1ca30c4234a2a
SHA256:
154817BA0BA26732B14D099922EBBEFD55381B441837BD4545A8698481CE295F
File Size:
137.73 KB, 137728 bytes
|
|
MD5:
affb1e28667614fc1e60df3eca75b17e
SHA1:
b7bcfcbc92916fafe888b95216ad17062130a568
SHA256:
FBB7D85B5BEE6891014C08A7F4A8B06DCD3953DA03B25E04D3B2AB148AF1397B
File Size:
120.83 KB, 120832 bytes
|
|
MD5:
5dc99751c764afd34145d667df5238ca
SHA1:
37ca244a0ec50312bd6a8c73073f762cdcfb6e13
SHA256:
B29FD73863E904D3FE07AC04B8DC0C26BBF1B2307932F977E66FAA88E0908CF7
File Size:
144.38 KB, 144384 bytes
|
|
MD5:
5818b8687256e9ede439a66d01f07904
SHA1:
483764ad5381f63be20ac35637d92b8acf37cada
SHA256:
51D27B67BA5C328CDD3F1B720621E9A815022C9AE60355031282BCB58018A43B
File Size:
40.45 KB, 40448 bytes
|
|
MD5:
1663c229bdc5887199490a71f6e18c1d
SHA1:
3c92f1cb506af5cfd125095ae51db679e378439a
SHA256:
ECFE5C9379219978F2D57ED39389A804120C83A15AC39893E534A454FB6FDB5D
File Size:
156.16 KB, 156160 bytes
|
|
MD5:
bfddba9230e6dfc5a7c8e28d6daf050f
SHA1:
ee5298ba3701e2b573971264f133a71c0e58dbcb
SHA256:
D32ACC9AC724B6E0FE257F66B95AD17C1E41400B09FF0B10029FA972D1BF2691
File Size:
141.31 KB, 141312 bytes
|
|
MD5:
e3347397b5ed2911187fb6ea13f0085a
SHA1:
0bfe7948e4c0134a3fb4776495cdee735f09e9f1
SHA256:
97EF4E39B5F08A8EDDA7C2765A336AC06B067DD6542CDDF96A9D3CFFB877A468
File Size:
154.62 KB, 154624 bytes
|
|
MD5:
ee5e979fc176d9041752b42f109d5ae4
SHA1:
c76973758ed2f02365f1317a4a9b7c8b1e713403
SHA256:
2C31792A4BBA454821399A042F94C2B882DEE252BF7A025603121744FE7BA66E
File Size:
131.58 KB, 131584 bytes
|
|
MD5:
51469b5bd19647a0e5b32f8a41f8649f
SHA1:
ceb0ad4935871ae8c21b874385f23fb053249120
SHA256:
2B7B88589A322CD2EFC762AB0F528393A97465BF1916D77D336CFE4C0B3F0A44
File Size:
153.09 KB, 153088 bytes
|
|
MD5:
c20d4525b318478447b67b0a2ed85a52
SHA1:
d996af71bc8976a1e0b0df339faae87127306328
SHA256:
F1FAA07209EE38F8E59E5635B419AB694D9FD7EB6B5362CB3A2AD4AD7B8B4FA2
File Size:
131.58 KB, 131584 bytes
|
|
MD5:
1c7d1bae3a037b6c9ce253c60f7fced6
SHA1:
8ec442561f49cb81d38c71aa52c5d1c200a97bb2
SHA256:
EDB0007248695F71D926DD006720666BA707F73B9D52B25EC8F641CB71541E62
File Size:
139.78 KB, 139776 bytes
|
|
MD5:
418e59b87b9560ec6d785e050dfe0e27
SHA1:
24208c8444bcdb27a6ce80d91bd1ae5c14b525a1
SHA256:
6ED69796D6636E3193110C5A95009A12B2D83BE87FA8322B8EE71CFADC3CB1BB
File Size:
11.26 KB, 11264 bytes
|
|
MD5:
b6629d898b9ccc04ad310dd28c7e49c0
SHA1:
0d2d01d41346820261f6d22738ab9a652d64c861
SHA256:
5FDEB8B667B84E290FCDC82F94289CBBF608747FCFF8300F7FC97CA46A30F638
File Size:
139.26 KB, 139264 bytes
|
|
MD5:
b41a5b439ed5d0a3b2c829bbb5f26504
SHA1:
9c41148c591b50e589fcc318e804520844bb1c12
SHA256:
AF55C0C00A342E6220D8C28BA1A9D8BD4BDF82DF653740BA0E7E988D19CD0AA2
File Size:
142.85 KB, 142848 bytes
|
|
MD5:
98ad3da6bc9705bef324ae463d799118
SHA1:
5858d28be3e407b15e3e19afc9e42c1644333878
SHA256:
27BB306328D4BA0D901E6F2E048FB522ABEBFDD1AEF80CE4BC140D01DF62BBBF
File Size:
145.41 KB, 145408 bytes
|
|
MD5:
49b387a0268eaca0fbefa6d60b3fe959
SHA1:
3c6f0543db0b7b1963c022b0f390afdbe9679981
SHA256:
DEA967461CF0B949F2232396FD59182078B5FA7C241E73D014A0AAC5C831EF52
File Size:
11.78 KB, 11776 bytes
|
|
MD5:
2b6475409917fd05776ba82dcb176cac
SHA1:
302757b27b5fcf1036c9bb1176522219d861ae7d
SHA256:
993A91CA552522EAA07B5A23B7DFE3342F85B7CC6B7F9E9E97168CAF6B37984F
File Size:
153.09 KB, 153088 bytes
|
|
MD5:
cbb59094120690d056878337f55e2237
SHA1:
264af14025d2b7eb06cd9fe4a6bb96fff69dc168
SHA256:
02F4F972492F9A2BDCAF1880194515183D53553E0951CD7795C90EB7F13FDAEA
File Size:
1.53 MB, 1529856 bytes
|
|
MD5:
7289f3ef019dd6ccc2962f3cbb98ffb8
SHA1:
e9a7ce8e515cc4d6bbc216827b9de2b902b4a7d1
SHA256:
F0053BC94CB0C6DCD95DF532039EE2CB4160654E9FFC684686552A9BCF2E3F4A
File Size:
153.09 KB, 153088 bytes
|
|
MD5:
7cf12bda08f2adc7e4c1682d4a6dddea
SHA1:
234b20671c7b33a6cd863eb00847bdccd1893b1c
SHA256:
FC066FC18D3659703ADB7B9D8A6673F0FA90DFA90DD99424574B813214704A6B
File Size:
152.58 KB, 152576 bytes
|
|
MD5:
d060d6020b4f4e4ea0e6028c9224e67e
SHA1:
6a37fcdbeb15bf3c406386e52a4e92e89a7bc096
SHA256:
FDF61D99ED7D3759C12900D080AFF194D06C3B3DAE16B251590DC75861D9EBC5
File Size:
2.90 MB, 2898944 bytes
|
|
MD5:
20e63dfb13aa095fd354e5ea17e023ea
SHA1:
870bb5b70d24bf8c96ff97cfa989672dab08be97
SHA256:
FB3315D01942A69B2FE2380E1B2123F4FEE7ABE25753195F1E53AD1BB3F39D4D
File Size:
2.02 MB, 2020352 bytes
|
|
MD5:
7b81e375b4f688db8713f073b5c80679
SHA1:
559f545d8ba58640f6d62cda64b4e7e1f57721de
SHA256:
29BAD55EF41989448132E966C6EE8266FF65D15805247734920FE87BE7008B00
File Size:
129.02 KB, 129024 bytes
|
|
MD5:
91bc466d39887a1bc9c7ec896363d00a
SHA1:
78c2566dfd00e139c0a89b70eed6167d42cfcc70
SHA256:
8724099D277AF984917F29F413423D168D4DF599626AB64C7D04E85F74E6A1CA
File Size:
11.78 KB, 11776 bytes
|
|
MD5:
60ab441f0690ecdfe039547a9672feb9
SHA1:
3ed4bfc3da00b0ba799cb39246e72a57a0928438
SHA256:
A980B6165205321F156F7A8CBF77065D802FC7EFC7FB015FCB3E8478898B242F
File Size:
135.17 KB, 135168 bytes
|
|
MD5:
298cb79289b772ef6bff5dcba693c591
SHA1:
8cd1a2460d95683621c99d4ef45db9b79611f472
SHA256:
28B2AB4D7A502D436D9DE4467A8CA6E7823EFED267019E5F567BEACF99DD5588
File Size:
151.04 KB, 151040 bytes
|
|
MD5:
d0a364932e71454bcfb4965255c6ea63
SHA1:
ae0f7dfac21cce8527ea4172bb5c9ef2a95d6e9a
SHA256:
D570634A349EA8C0DFFC545F98FF7A1336272D6BA7BCEF99E973777DFABDCD33
File Size:
32.77 KB, 32768 bytes
|
|
MD5:
4b11b685fd4a9b086c1f30424b84424b
SHA1:
a10e59c4eddbdf2e6e56262532dc780c75317916
SHA256:
CF3E6BD5A32D5908F8373E2A2CDC4198E337011ED133995FC820EF511301A91D
File Size:
139.26 KB, 139264 bytes
|
|
MD5:
e16dae4685c44d82ac5f85014bd8ef28
SHA1:
fd38419b57a0c9c5a566d10efd3e0108fa807d5d
SHA256:
19FF710CCF31759F2EB7E0F3421B5744E7A9A741DC08AE4DEFAA6999DCAB9013
File Size:
141.31 KB, 141312 bytes
|
|
MD5:
dc3f9e4c743bd6aea2b872f5030db9c1
SHA1:
bab3d54c3f4c09b1c1aae07f590263ff05741cc2
SHA256:
9C535BF1A4104E34856D32294D8CDE59C72ED042B79D138C53CC5845E05987EC
File Size:
134.66 KB, 134656 bytes
|
|
MD5:
e848a4656c3cc11e503da81f9ce391af
SHA1:
52f2e84e7f255636a97acc22b5d2bb913ca5ae4e
SHA256:
9C9838E6181A1B5C5F736BE7A4C3C36B5CA309159B9980737648090473AC353A
File Size:
142.34 KB, 142336 bytes
|
|
MD5:
b610597a733e6825975bbf060d1327cd
SHA1:
86491c45bbd2ee09dd3ba85933d8b203f6039259
SHA256:
6BCE39F70C01560D4BB763FA47E7D1717D7A8C5B5E787D4543E237C08CA8FA3F
File Size:
134.14 KB, 134144 bytes
|
Windows Portable Executable Attributes
- File doesn't have "Rich" header
- File doesn't have debug information
- File doesn't have exports table
- File doesn't have relocations information
- File doesn't have security information
- File has exports table
- File has TLS information
- File is .NET application
- File is 32-bit executable
- File is 64-bit executable
Show More
- File is console application (IMAGE_SUBSYSTEM_WINDOWS_CUI)
- File is either console or GUI application
- File is GUI application (IMAGE_SUBSYSTEM_WINDOWS_GUI)
- File is Native application (NOT .NET application)
- File is not packed
- IMAGE_FILE_DLL is not set inside PE header (Executable)
- IMAGE_FILE_EXECUTABLE_IMAGE is set inside PE header (Executable Image)
File Icons
File Icons
This section displays icon resources found within family samples. Malware often replicates icons commonly associated with legitimate software to mislead users into believing the malware is safe.Windows PE Version Information
Windows PE Version Information
This section displays values and attributes that have been set in the Windows file version information data structure for samples within this family. To mislead users, malware actors often add fake version information mimicking legitimate software.| Name | Value |
|---|---|
| Assembly Version |
|
| Comments |
|
| Company Name |
|
| File Description |
Show More
|
| File Version |
|
| Internal Name |
Show More
9 additional items are not displayed above. |
| Legal Copyright |
|
| Legal Trademarks |
|
| Original Filename |
Show More
9 additional items are not displayed above. |
| Product Name |
Show More
|
| Product Version |
|
File Traits
- .NET
- 00 section
- 2+ executable sections
- Agile.net
- CreateThread
- CryptoObfus
- CryptUnprotectData
- dll
- Fody
- Goliath
Show More
- HighEntropy
- Installer Version
- NewLateBinding
- No CryptProtectData
- ntdll
- Run
- SmartAssembly
- VirtualQueryEx
- WriteProcessMemory
- x64
- x86
- Yano
- ZYXDN
Block Information
Block Information
During analysis, EnigmaSoft breaks file samples into logical blocks for classification and comparison with other samples. Blocks can be used to generate malware detection rules and to group file samples into families based on shared source code, functionality and other distinguishing attributes and characteristics. This section lists a summary of this block data, as well as its classification by EnigmaSoft. A visual representation of the block data is also displayed, where available.| Total Blocks: | 12 |
|---|---|
| Potentially Malicious Blocks: | 1 |
| Whitelisted Blocks: | 0 |
| Unknown Blocks: | 11 |
Visual Map
? - Unknown Block
x - Potentially Malicious Block
Similar Families
Similar Families
This section lists other families that share similarities with this family, based on EnigmaSoft’s analysis. Many malware families are created from the same malware toolkits and use the same packing and encryption techniques but uniquely extend functionality. Similar families may also share source code, attributes, icons, subcomponents, compromised and/or invalid digital signatures, and network characteristics. Researchers leverage these similarities to rapidly and effectively triage file samples and extend malware detection rules.- MSIL.Mardom.SF
- MSIL.Quasar.B
- MSIL.Quasar.CA
- MSIL.Quasar.CB
- MSIL.Spy.RC
Show More
- MSIL.Spy.RCB
Windows API Usage
Windows API Usage
This section lists Windows API calls that are used by the samples in this family. Windows API usage analysis is a valuable tool that can help identify malicious activity, such as keylogging, security privilege escalation, data encryption, data exfiltration, interference with antivirus software, and network request manipulation.| Category | API |
|---|---|
| User Data Access |
|
| Other Suspicious |
|
| Anti Debug |
|
| Syscall Use |
Show More
50 additional items are not displayed above. |
| Process Shell Execute |
|
| Encryption Used |
|
| Process Manipulation Evasion |
|
| Network Winsock2 |
|
| Network Winsock |
|
Shell Command Execution
Shell Command Execution
This section lists Windows shell commands that are run by the samples in this family. Windows Shell commands are often leveraged by malware for nefarious purposes and can be used to elevate security privileges, download and launch other malware, exploit vulnerabilities, collect and exfiltrate data, and hide malicious activity.
C:\WINDOWS\system32\fondue.exe "C:\WINDOWS\system32\fondue.exe" /enable-feature:NetFx3 /caller-name:mscoreei.dll
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\ac8400b48c8bba2a650d76496af4b0923cb93e85_0000137728.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\0f23eab69d9a7a5bc4cc2db48a1bb06382987c27_0000127488.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\eb99b05eb4fcb1645541ecfd113a1c7569017f39_0000143872.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\41d29a124519216bd70d5e8dd51a950bd042b370_0000118272.,LiQMAxHB
|
Show More
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\f0ab35f6b85d7b8c44454084d68a929d78b2f645_0000139776.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\b64fab7b7f309ba676e8f5903a4bb0939d803fae_0000151552.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\bb8431c5fc572b8a0c6f8cfb6e5e2c5a44737dac_0000146944.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\648c2bb8ff522422d5077e0788fe8d797ddaa1d7_0000136704.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\319acf0a7109f2ae2c41cd5bdc61c7a608c22628_0000151040.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\331b48846e1040ce59004e1db1eeb947499c33ec_0000142336.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\590fad56c274a3869156ee6d09911f7b0b81038c_0000139776.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\824f26e6a69b93c954c2719075c7c838d5c01ad3_0000141824.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\db0b8542aab7a7232ddb709d1da0dbd35a2d67f0_0000138240.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\64a9422d125776f24c0e690052983055cd4f6a38_0000116224.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\cb366e2c644a48f1179d31479973ed34c24841b1_0000155648.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\2aaa8b24f951b35cb6d781285ff96792ecff8814_0000143872.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\c6aaa3e6263c12b55af7ce2a3f609573d675e7e1_0000130048.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\b5fb6bfe548075f1915a61499e9820a61141806d_0000133120.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\5c51d88d435ffdcd7cbf6556f9d9edda410924d5_0000145920.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\ccadfcbd4c68a77155d2bb38bc8b1708434247d1_0000145920.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\6dae3debfafc7e3eb5c7e5fbf1cb1ef094adc2f3_0000148480.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\666271f9934de077e2dd103177a049564a15af1b_0000140288.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\db2732e26e44496b03851490d886d724d3809d55_0000119808.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\0f560e5650acf93a33ecea809a88a1c2bfb7c894_0000146944.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\5d2ccbc695550e916f002dcb663a94f1a20f6306_0000148992.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\4b6b299707e85f1cc37e81091e79b4e5ba54331d_0000146944.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\d7daa608246b3cb5c450067c7a6386b6127811d5_0000142336.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\43c961d7f8edff70ea9b32e42886e1f767d0f480_0000135680.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\c2a339bff70735d5b55acb9be1724bbb8a44e1a8_0000134656.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\81759aceb6881812d8087decd39f060142009855_0000149504.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\2200bea9666e611a44fa81c5598cf81301f82470_0000150016.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\a207a6a1adf38aea2300f8e7e7306a60a6e6df2c_0000144384.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\32c8bbd8eab65a4def952bdf35e9d1c159da49bb_0000150016.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\4a7ae1e4af5d28d92689d0c7df118983a5da6647_0000153088.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\f66505b302264de81c8f4331a0112cc137e1eb4c_0000156672.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\adae4d57cf458a36f0450b99b2b078af96000343_0000152576.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\89ca06daf2003776f9e988bba646b789b7e69626_0000135680.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\c71a31eeedb6c969d5724542b014a380fa1a119d_0000133632.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\6cff4cd52bbd39c6566e259ca016a10b9d254181_0000115712.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\c4f617f917a69d5f78b5cafb9ec8f9dd92ef0720_0000126976.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\48fd581035aa7a990ab324be8623736342b71a9b_0000134656.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\73c3c1a17feb3ad8a9cbb7acd47e77e6bf526275_0000136704.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\9d96f7f54d7dc34c5f065583b726d63cd41b481c_0000147456.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\1952f9cd53a9e109fd8c18b7d497f85d481591a1_0000137216.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\53a15d4ce5122027fad9e6215e56e4f2c1fe0872_0000129024.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\6634cef5c1a9ed0f12ae0a5d44bae42bb6018b07_0000141312.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\9845431ac0180e23815a548672f8a1303216c1e7_0000199168.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\4f9d15d5221558acf7d42f3346a0d456520b8ffb_0000140800.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\33aba85a0f62e0a9619ba88c6c83f06867bf8c02_0000153088.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\49b55ac6d8bcea09aef06f8045e7c998700f22d6_0000127488.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\9be94409a9c7cb04ceec0d5910929f4f1cfa1c1f_0000148480.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\dee487c15acb33e9966bc46e50305e67781fccd8_0000141312.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\81e1b304740a77e864879a076ce3063b16162451_0000154112.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\34c3f3eda73f9554e20fd1f0a5916c85c24e424d_0000144896.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\d9ad26ff411234e1852c56fb58ee3214a0e19759_0000130048.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\49432882369280950bf8bc1876f465c448f3aae3_0000153088.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\5b96e2735f9af5a14fc8dbf617440bcd882954f4_0000139264.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\d1d074568694f78c03db47cb571aac62964e565b_0000133632.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\372f0aa50350b580cc5a1b1ff2854362eb9f906e_0000120832.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\115dcfefcff58169f39347147470679dea19daf3_0000141824.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\1733b1e104be689cac5d5aca36bae45fd1fe9b31_0000156672.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\b3ea979c50fa78e6614c520a11d3952e6806d58b_0000168448.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\52b2ee6ce4aafaea9f1620695170df3880d3418b_0000132096.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\6ac63635f3033e97aeb32633e73751cf27152322_0000146944.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\581baa137028937f903edc002308d5945c1dade6_0000150528.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\5dc0772268c30c243c46014b9d827be7409cfa40_0000158208.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\df9ececda4cad75189db25930a0566dc2386fa42_0000133632.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\e9fb89dc89e19c264ebc2021a1e2480eab20cbe0_0000141312.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\6954343fb92928f849cf91daee3529fd284cce5f_0000179712.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\20cbd90ed699016db99129cd310db3344acdf0ee_0000156160.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\1ddec97ec79f8aa5d5d13975abae821e3221db32_0000147456.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\6285fab51fd0bd2b1d1b0780ed9535054206cfcd_0000139776.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\7499ad1b41530310e4c1de18a8a1ca30c4234a2a_0000137728.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\b7bcfcbc92916fafe888b95216ad17062130a568_0000120832.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\37ca244a0ec50312bd6a8c73073f762cdcfb6e13_0000144384.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\3c92f1cb506af5cfd125095ae51db679e378439a_0000156160.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\ee5298ba3701e2b573971264f133a71c0e58dbcb_0000141312.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\0bfe7948e4c0134a3fb4776495cdee735f09e9f1_0000154624.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\c76973758ed2f02365f1317a4a9b7c8b1e713403_0000131584.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\ceb0ad4935871ae8c21b874385f23fb053249120_0000153088.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\d996af71bc8976a1e0b0df339faae87127306328_0000131584.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\8ec442561f49cb81d38c71aa52c5d1c200a97bb2_0000139776.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\0d2d01d41346820261f6d22738ab9a652d64c861_0000139264.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\9c41148c591b50e589fcc318e804520844bb1c12_0000142848.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\5858d28be3e407b15e3e19afc9e42c1644333878_0000145408.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\302757b27b5fcf1036c9bb1176522219d861ae7d_0000153088.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\e9a7ce8e515cc4d6bbc216827b9de2b902b4a7d1_0000153088.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\234b20671c7b33a6cd863eb00847bdccd1893b1c_0000152576.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\559f545d8ba58640f6d62cda64b4e7e1f57721de_0000129024.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\3ed4bfc3da00b0ba799cb39246e72a57a0928438_0000135168.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\8cd1a2460d95683621c99d4ef45db9b79611f472_0000151040.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\a10e59c4eddbdf2e6e56262532dc780c75317916_0000139264.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\fd38419b57a0c9c5a566d10efd3e0108fa807d5d_0000141312.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\bab3d54c3f4c09b1c1aae07f590263ff05741cc2_0000134656.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\52f2e84e7f255636a97acc22b5d2bb913ca5ae4e_0000142336.,LiQMAxHB
|
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\86491c45bbd2ee09dd3ba85933d8b203f6039259_0000134144.,LiQMAxHB
|