Trojan.Delf
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Popularity Rank: | 9,321 |
| Threat Level: | 90 % (High) |
| Infected Computers: | 21,064 |
| First Seen: | July 24, 2009 |
| Last Seen: | February 6, 2026 |
| OS(es) Affected: | Windows |
Trojan.Delf is a threat that intercepts the Internet traffic and compromises the system security in a big way. If the computer users encounter this Trojan on their systems, they should keep in mind that there may be other threats on their machine as well. Trojan.Delf is often installed by other threats on the targeted computers, but it also can be a product of a drive-by download under the file name 'bot_unencrypted.exe.' When Trojan.Delf finds its way onto a computer, it changes its name once the installation is complete.
The Trojan.Delf infection ends up being installed in the System32 folder, where it creates a copy of itself bearing the name WtiSysST.exe. Trojan.Delf is then installed as a system drive in an attempt to avoid detection by the usual security products. Trojan.Delf also modifies a Registry sub-key, making it start whenever the infected computer is booted up. Once the installation is complete, Trojan.Delf connects to its remote server for updates and instructions from its developers.
Trojan.Delf will attempt to obtain determined information, such as cookies, browsing history, user names and passwords by intercepting secure and insecure Internet data (HTTPS and HTTP). Once that data is saved, it is later uploaded to a remote server where the attackers may use it to further their scheme.
Trojan.Delf hides from security products by injecting its code into system processes, such as lsass.exe and svchost.exe. Trojan.Delf also may modify the system settings and trick websites to think that computer users are browsing via Mozilla Firefox, Apple Safari, Google Chrome or Avant Browser. This is done to allow Trojan.Delf to avoid removal for as long as possible by obfuscating its presence in a system.
Table of Contents
Aliases
15 security vendors flagged this file as malicious.
| Antivirus Vendor | Detection |
|---|---|
| AVG | Hider.QFR |
| Fortinet | W32/ZAccess.K |
| Microsoft | TrojanDropper:Win32/Sirefef.B |
| Antiy-AVL | Virus/Win32.ZAccess.gen |
| Symantec | Packed.Generic.344 |
| NOD32 | Win32/Sirefef.DA |
| K7AntiVirus | Virus |
| McAfee | Generic.dx!bd3j |
| AVG | Agent_r.BEC |
| Fortinet | W32/ZAccess.K!tr |
| Ikarus | Rootkit.Win32.ZAccess |
| Antiy-AVL | Virus/Win32.ZAccess |
| AntiVir | TR/Conjar.187904.5 |
| Comodo | TrojWare.Win32.Rootkit.ZAcces.HL |
| BitDefender | Gen:Heur.Conjar.11 |
SpyHunter Detects & Remove Trojan.Delf
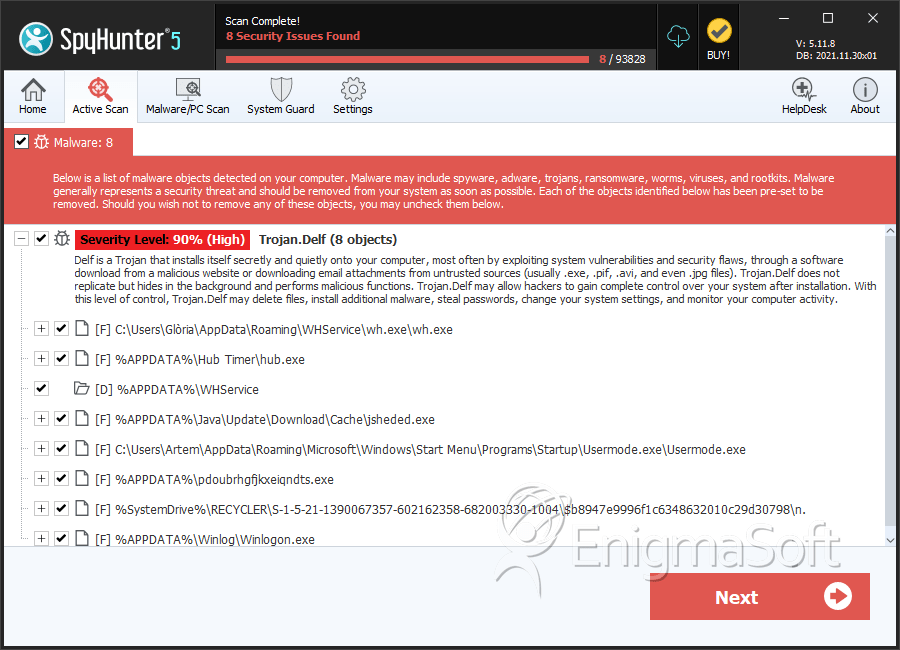
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | wh.exe | 681605a644d93853b6dcad2fb0b759c0 | 3,741 |
| 2. | hub.exe | e28b8169e6766a795a6e0a4b1faece69 | 2,256 |
| 3. | scvhost.exe | 42ad0d9c51373baa39b9c04b303e310a | 268 |
| 4. | jsheded.exe | de2b3d20a8cf3fc7d75f73c3ee757148 | 151 |
| 5. | Usermode.exe | 2adec0cae94520d5700c45c7a7b982e2 | 131 |
| 6. | Winlogon.exe | a6fadf10d3e593803601ddff296a10d7 | 10 |
| 7. | dwm.exe | 8718222259cc28fc98d4c619b7782844 | 8 |
| 8. | FreeListenManager.exe | ba120116bc56efbe381fada54ad930b4 | 6 |
| 9. | winmgr.exe | 972d2cea5f8ed8fe89ef51376fbe5910 | 6 |
| 10. | svhost.exe | b2c187c97295a6828527059f49ccf19a | 6 |
| 11. | batszxye.exe | 7a2ccfa78bace5cd84372aa0be3cff03 | 4 |
| 12. | n. | 55e367336d30de18020f72a4a6671e5c | 4 |
| 13. | iupdater.exe | 62c70a0a68ffc3c7718309957a06564f | 3 |
| 14. | asktbarx.dll | 15594e754153e0e4fd3db6e8f5ed3abe | 3 |
| 15. | 668709b5-34ff-4fd2-8f3a-27b6c6221427.exe | bf4d11d8e4864532e46a350e0576c62b | 2 |
| 16. | build.exe | ea768a24c0fc6edc87c005c66681cd70 | 2 |
| 17. | skype.dat | 32c5a6206e8a00c7337ef47d3c0636b4 | 2 |
| 18. | tjplsgvowg.exe | b7817240ad59e731aadbeffc305f8c36 | 2 |
| 19. | ms3x.exe | 209a909f43e9b6371aa5791b60465ecd | 2 |
| 20. | nqnqe.exe | cac15bbccd5b708290a44086f72deb7d | 2 |
| 21. | 0.5741384901339003.exe | be0bdbc56b875f2645e594d35c006119 | 2 |
| 22. | GoogleApp.exe | 2a650fca7830ce1d4217421378d55835 | 2 |
| 23. | mssfxya.com | 546ca59fae4c1e900dae82b03ecb3952 | 1 |
| 24. | 3732892.dll | 7c92a0b8ccef87355fa5b6836cc4261f | 1 |
| 25. | pmsorg.exe | ceb91da87d07244ed876f0b92da3b192 | 1 |
| 26. | LED.exe | 48babb6a899ae12a30538f2253a9b99a | 1 |
| 27. | ynofjatb.exe | 83cf7cc1fc131553cd56283c29055e31 | 1 |
| 28. | apptj.exe | 97040ed47a7715f6eb37b1207dfd9d64 | 1 |
| 29. | file.exe | d58d090a6e4b8657a0abea0a0fda60fc | 0 |
Registry Details
Directories
Trojan.Delf may create the following directory or directories:
| %APPDATA%\WHService |