Trojan.Badjoke
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Popularity Rank: | 1,753 |
| Threat Level: | 10 % (Normal) |
| Infected Computers: | 4,942 |
| First Seen: | April 5, 2012 |
| Last Seen: | January 26, 2026 |
| OS(es) Affected: | Windows |
Table of Contents
SpyHunter Detects & Remove Trojan.Badjoke
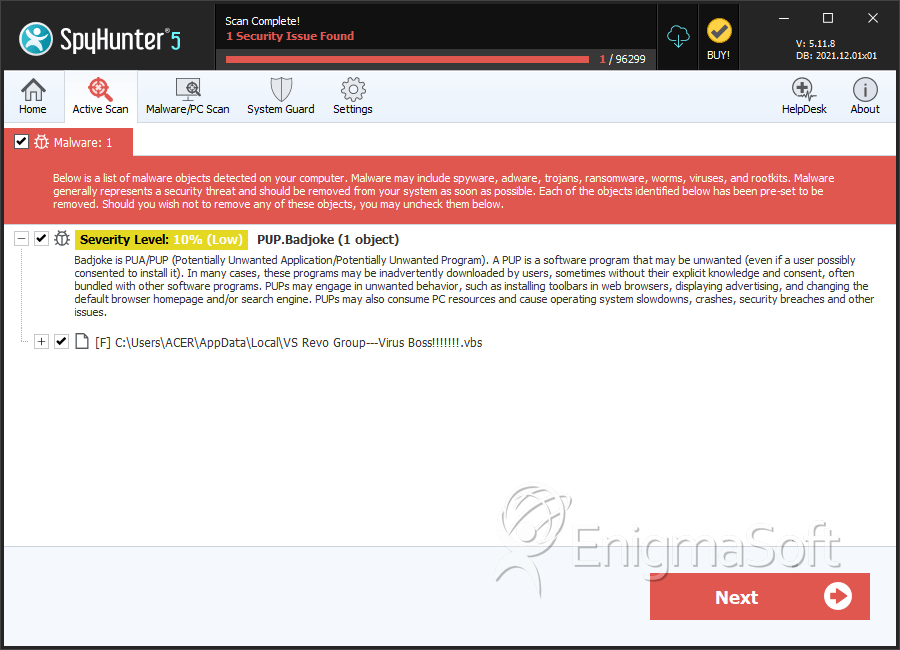
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | VS Revo Group---Virus Boss!!!!!!!.vbs | d68479c58d8ff342d3721bdffe8a0220 | 183 |
| 2. | friend.exe | b2b63a8ce53e18f9dc70bbccf42ede83 | 10 |
Analysis Report
General information
| Family Name: | PUP.Badjoke |
|---|---|
| Signature status: | No Signature |
Known Samples
Known Samples
This section lists other file samples believed to be associated with this family.|
MD5:
ae1aa2de6b8be19775f356e78349c0c7
SHA1:
ca8c0565373312867cec2f2f6650d2708c03499b
File Size:
64.00 KB, 64000 bytes
|
|
MD5:
8db2bc4ed355239adc629409ee80a156
SHA1:
1ee48acf095fad37b022fe16b95cb17e42fd557f
File Size:
419.84 KB, 419840 bytes
|
|
MD5:
0a137e56a8ff25fd0cef22d970142d82
SHA1:
2fca749ff8f9d57c56e0873c9ee788c6cacd3323
SHA256:
5F93BF831407B99E8D5F7CDECACB3E729CCB951FC6220B4D9D884A58B8CA856A
File Size:
153.09 KB, 153088 bytes
|
|
MD5:
6931cf934847b2f341fc34e36cd7bf9f
SHA1:
3b48f80706b63b5e102bef92822158af8e4c2a86
SHA256:
E32E8C77D5191005B03AAC3918A7A46569F6278FE1CDF8DC4BAD6F4E90FFFF01
File Size:
4.54 MB, 4535135 bytes
|
|
MD5:
0b02384d96a7d1aa046618bad40c0a69
SHA1:
fb2d41f057215c52530c23dce863c08c1027c334
SHA256:
00D0AA34A4F90864B05F340A27808AF18E9CDE73108F866A902D1915A72430EB
File Size:
267.26 KB, 267264 bytes
|
Show More
|
MD5:
d4163d85ba71a09b181dea459744698c
SHA1:
002efbdaf3b87a486cd1b577b219a36995a66489
SHA256:
1FD51D6DD83F903B81C2FE5EE5811A32F4EEDDAE97B02C89659E6F0E7DA16B1E
File Size:
613.38 KB, 613376 bytes
|
|
MD5:
8ed8f5c96b0a178fb2c5855729f2af0e
SHA1:
a2c368f0145546d7991079b71f189435d301d80c
SHA256:
D3029297E1B684901D7C7A82A5A80B24B7867CC9CD27F2D5F5E090C2E41CF661
File Size:
552.96 KB, 552960 bytes
|
|
MD5:
e4a61690469507d6da1496c231acc055
SHA1:
42921c9d12286d95594de1c17a60006d6b4f5895
SHA256:
0C16FB3F6EBAEF29004AE74F333774C739CD7BAD324ECD3459945693FBE01AAE
File Size:
1.62 MB, 1624064 bytes
|
Windows Portable Executable Attributes
- File doesn't have "Rich" header
- File doesn't have debug information
- File doesn't have exports table
- File doesn't have relocations information
- File doesn't have security information
- File has been packed
- File has exports table
- File has TLS information
- File is .NET application
- File is 32-bit executable
Show More
- File is 64-bit executable
- File is either console or GUI application
- File is GUI application (IMAGE_SUBSYSTEM_WINDOWS_GUI)
- File is Native application (NOT .NET application)
- File is not packed
- IMAGE_FILE_DLL is not set inside PE header (Executable)
- IMAGE_FILE_EXECUTABLE_IMAGE is set inside PE header (Executable Image)
File Icons
File Icons
This section displays icon resources found within family samples. Malware often replicates icons commonly associated with legitimate software to mislead users into believing the malware is safe.Windows PE Version Information
Windows PE Version Information
This section displays values and attributes that have been set in the Windows file version information data structure for samples within this family. To mislead users, malware actors often add fake version information mimicking legitimate software.| Name | Value |
|---|---|
| Assembly Version |
|
| Command Line | -p "[path]" -t "[file types]" -f "[find what]" -i include subdirs -c case sensitive search.exe -p "c:\windows" -t "*.htm" -f "Microsoft" -c -i |
| Comments |
|
| Company Name |
|
| support@rjlsoftware.com | |
| File Description |
|
| File Version |
|
| Internal Name |
|
| Legal Copyright |
|
| Legal Trademarks |
|
| Original Filename |
|
| Product Name |
|
| Product Version |
|
| Unity Version | 2018.2.21f1_a122f5dc316d |
| Website |
|
File Traits
- .adata
- .aspack
- .NET
- Agile.net
- ASPack v2.12
- big overlay
- CreateThread
- Fody
- HighEntropy
- Installer Manifest
Show More
- Installer Version
- No Version Info
- packed
- VirtualQueryEx
- WriteProcessMemory
- x64
- x86
Block Information
Block Information
During analysis, EnigmaSoft breaks file samples into logical blocks for classification and comparison with other samples. Blocks can be used to generate malware detection rules and to group file samples into families based on shared source code, functionality and other distinguishing attributes and characteristics. This section lists a summary of this block data, as well as its classification by EnigmaSoft. A visual representation of the block data is also displayed, where available.| Total Blocks: | 6,238 |
|---|---|
| Potentially Malicious Blocks: | 29 |
| Whitelisted Blocks: | 5,026 |
| Unknown Blocks: | 1,183 |
Visual Map
? - Unknown Block
x - Potentially Malicious Block
Similar Families
Similar Families
This section lists other families that share similarities with this family, based on EnigmaSoft’s analysis. Many malware families are created from the same malware toolkits and use the same packing and encryption techniques but uniquely extend functionality. Similar families may also share source code, attributes, icons, subcomponents, compromised and/or invalid digital signatures, and network characteristics. Researchers leverage these similarities to rapidly and effectively triage file samples and extend malware detection rules.- Bancos.B
- Farfli.FR
- Fugrafa.T
- Injector.DFF
- Injector.DGB
Show More
- Injector.FGSA
- Injector.FHE
- Injector.GDSA
- Injector.KKF
- LegendMir.B
- Shipup.AG
- Sohanad.A
Files Modified
Files Modified
This section lists files that were created, modified, moved and/or deleted by samples in this family. File system activity can provide valuable insight into how malware functions on the operating system.| File | Attributes |
|---|---|
| \device\namedpipe\gmdasllogger | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\_is74c1.tmp | Synchronize,Write Attributes |
| c:\users\user\appdata\local\temp\_is74c1\0x0409.ini | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\_is74c1\_ismsidel.ini | Generic Read,Write Data,Write Attributes,Write extended,Append data |
| c:\users\user\appdata\local\temp\_is74c1\net send lite.msi | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\_is74c1\setup.ini | Generic Write,Read Attributes |
| c:\users\user\appdata\local\temp\_msi5166._is | Generic Read,Write Data,Write Attributes,Write extended,Append data |
| c:\users\user\appdata\local\temp\~74b0.tmp | Generic Write,Read Attributes |
| c:\windows\downloaded installations\{52df3883-6f28-4253-b39e-77338c33e13b}\net send lite.msi | Generic Read,Write Data,Write Attributes,Write extended,Append data,Delete,LEFT 262144 |
Windows API Usage
Windows API Usage
This section lists Windows API calls that are used by the samples in this family. Windows API usage analysis is a valuable tool that can help identify malicious activity, such as keylogging, security privilege escalation, data encryption, data exfiltration, interference with antivirus software, and network request manipulation.| Category | API |
|---|---|
| Anti Debug |
|
| User Data Access |
|
| Process Manipulation Evasion |
|
| Process Shell Execute |
|
| Encryption Used |
|
| Syscall Use |
Show More
|
Shell Command Execution
Shell Command Execution
This section lists Windows shell commands that are run by the samples in this family. Windows Shell commands are often leveraged by malware for nefarious purposes and can be used to elevate security privileges, download and launch other malware, exploit vulnerabilities, collect and exfiltrate data, and hide malicious activity.
MSIEXEC.EXE /i "C:\WINDOWS\Downloaded Installations\{52DF3883-6F28-4253-B39E-77338C33E13B}\Net Send Lite.msi" SETUPEXEDIR="c:\users\user\downloads"
|
