Sodinokibi Operators Turn to Monero to Avoid Getting Caught

Monero over Bitcoin
Sodinokibi is already an established name in the ransomware space and it keeps evolving. The latest development seems to be a change of default currency. Sodinokibi's proprietors are moving from bitcoin to the Monero cryptocurrency as their preferred form of ransom payment.
Reportedly, the cybercriminals behind Sodinokibi announced their intention to go through with the transition on a hacker forum back in March. At the time of this writing, the TOR ransom site for Sodinokibi already shows Monero as the preferred currency. Although it is still possible to pay in bitcoin, the victim would have to pay a hefty 10% on top of what they would have to pay in Monero. This is likely just the beginning of the transition. The cybercriminals said in the aforementioned forum post they intended to completely remove bitcoin as a payment option in the future.
This Week in Malware Ep2: Sodinokibi Ransomware is a Ransomware-as-a-Service
Why the transition?
The goal of Sodinokibi’s operators making this move is likely to further hinder law enforcement agencies in their efforts to find and apprehend the cybercriminals. Since its creation in 2014, Monero has evolved and developed with a strong focus on privacy. Unlike most other cryptocurrencies, Monero uses an obfuscated public ledger. This means it is virtually impossible for the authorities to trace transactions. Monero was also very popular with criminals during the WannaCry ransomware attacks.
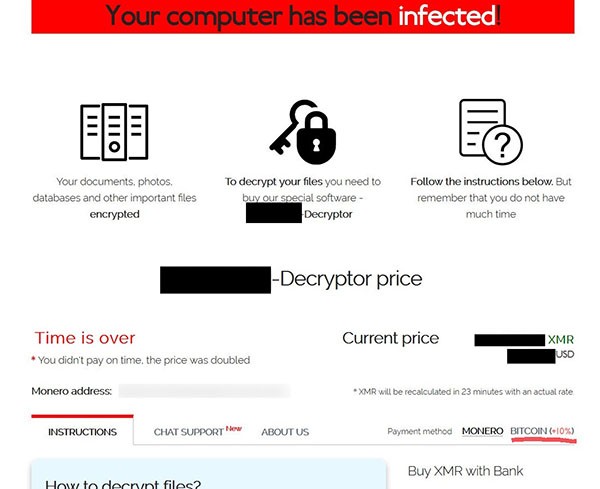
Example image of Sodinokibi ransom note
The Sodinokibi ransomware has only been around since April 2019. However, cybercriminals have used it in a number of attacks and reportedly raked in a fortune in the span of a year. The criminals running Sodinokibi are also trying to recruit third parties to "... assist our victims in acquiring the decryptor..." Those are sometimes referred to as "data recovery" companies. Sodinokibi’s operators attempt to entice such potential partners with a promise of a better profit. While this approach isn’t unique, Sodinokibi’s operators have managed to leverage the Ransomware-as-a-Service model better than most.
The people behind the Sodinokibi ransomware are not the first cybercriminals to take an interest in Monero and they will not be the last. Law enforcement agencies have stated repeatedly they aren't able to trace Monero transactions. This makes it impossible to gather the necessary evidence. Monero may be a huge problem for the authorities, but that makes it an appealing option for cybercriminals.